Cloud transformation usually happens concurrently throughout siloed organizational items and teams, every probably utilizing a distinct cloud for his or her functions and workloads. Nevertheless, taking stock of all their cloud assets and constructing a compliant, safe, easy, and unified technique has develop into a typical problem.
It wouldn’t be shocking to see a corporation with most of its workloads in AWS utilizing Microsoft 365 and Azure Energetic Listing whereas additionally closely utilizing Google Cloud GKE and Massive Question. On high of that, Oracle Cloud can also be within the combine with some autonomous database choices. As cloud adoption matures in a corporation, and as smaller cloud suppliers acquire traction, the combo of providers and cloud platforms turns into extremely numerous and complicated. In gentle of those challenges, organizations should nonetheless discover methods to manipulate and safe their total cloud infrastructure.
The reply? A framework that works throughout all clouds to unify detection, prioritization, and remediation of essentially the most impactful dangers dealing with the group.
Identities and Authentication Keys
Diving right into a use case round cloud identification authentication keys for entry, let’s see how one can defend your group’s crown jewels in your multicloud atmosphere. Within the cloud world, identification is maybe essentially the most important cloud object to manipulate, monitor, detect, and remediate. Compromising a cloud identification has the most important blast radius since, frankly, the general public cloud is only a bunch of public APIs that reply to authenticated requests.
Authentication keys are cryptographic entities hooked up to an identification that let you problem authenticated API requests from the Web. Therefore, these keys name for the undivided consideration of any governance and safety technique. Nevertheless, every cloud supplier defines identification differently, with a totally new set of capabilities and dangers.
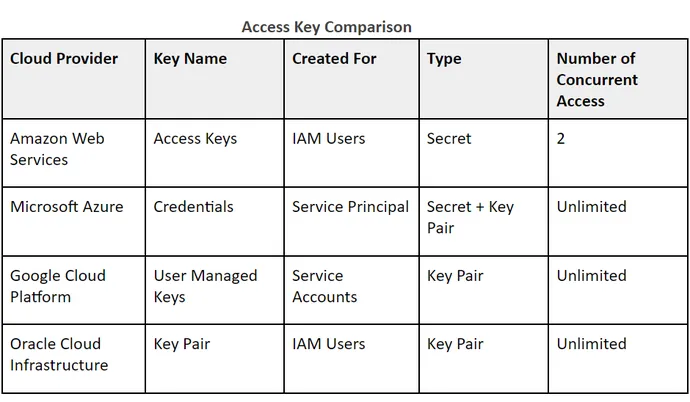
The concept right here is to think about a corporation that desires to implement the next coverage: “Authentication keys must be rotated each 90 days, and each 30 days if they permit personally figuring out info entry.” This seemingly easy coverage would wish to take 4 completely different implementations, relying on which cloud it’s utilizing. Moreover, the safety admin would wish to tailor particular insurance policies, reminiscent of limiting the variety of concurrent keys (not related to AWS) or implementing expiration dates upon key creation (not related for secrets and techniques).
The identical idea applies when a corporation tries to implement “don’t enable public entry to storage objects” or “solely construct workloads from photographs which are updated.”
Constructing, Securing, and Governing the Cloud
Whereas every cloud is exclusive, foundationally, they don’t seem to be so completely different. All of them have an idea of a pc occasion, object and file storage, and each human and nonhuman identities, every of which might be assigned permissions. In consequence, the multicloud infrastructure requires unification between constructing, securing, and governing the cloud.
When constructing cloud deployments, organizations depend on infrastructure as code (IaC) languages like HashiCorp’s Terraform to create a unified strategy to handle cloud objects. Consider IaC as a higher-level language over the lower-level cloud-specific API calls.
The parallel higher-level language for securing and governing the cloud is the cloud-native software safety platform (CNAPP). CNAPP converges instruments like cloud safety posture administration, cloud infrastructure entitlement administration, cloud workload safety platform, configuration administration database, and others, offering full safety on your cloud, spanning the cloud improvement lifecycle from construct time to run time. CNAPP supplies a single pane of glass for all of your cloud environments.
These options present a whole stock of your cloud property, in addition to visibility into potential safety gaps and dangers, correlating throughout a broad vary of indicators together with misconfigurations, vulnerabilities, Web publicity, extreme permissions, and extra.
By means of a CNAPP, groups can allow unified detection, investigation, and enforcement of frequent cloud objects, in addition to pitfalls reminiscent of uncovered storage, unpatched compute situations, and extra. Ideally, a single UI workflow permits you to implement multicloud group insurance policies reminiscent of “block public entry for cloud storage” or “isolate compute situations that settle for site visitors from the Web and expose a service with important vulnerabilities.”
Listed here are further finest practices and suggestions for securing your cloud footprint:
- Resolve whether or not to measure towards a safety framework like NIST or CIS, or your individual internally developed insurance policies. Implement these insurance policies throughout the event lifecycle, with specific definition of the place to implement action-blocking guardrails. A CNAPP may help you accomplish this.
- Guarantee your safety crew is diversified when it comes to multicloud data, e.g., AWS, Azure, and GCP.
- Implement identification finest practices, reminiscent of single sign-on and multifactor authentication, by way of your group’s present IAM supplier, each time attainable. Keep away from the usage of cloud-specific native identities to entry the cloud from the Web.
- Outline the unified view as a prerequisite for procurement of cloud safety instruments. Ideally, select instruments that allow a unified strategy of implementing organizational insurance policies throughout clouds.
Cloud transformation has develop into an important initiative for a lot of organizations. As you undergo the cloud transformation journey, do not forget that your strategy to safety (and the instruments you utilize) should rework as effectively. Whether or not you’re unifying siloed instruments, safety and DevOps groups, completely different cloud distributors, administration, or insurance policies and languages, bringing instruments collectively and implementing commonalities will profit your group in the long term.
Learn extra Accomplice Views from Zscaler.


