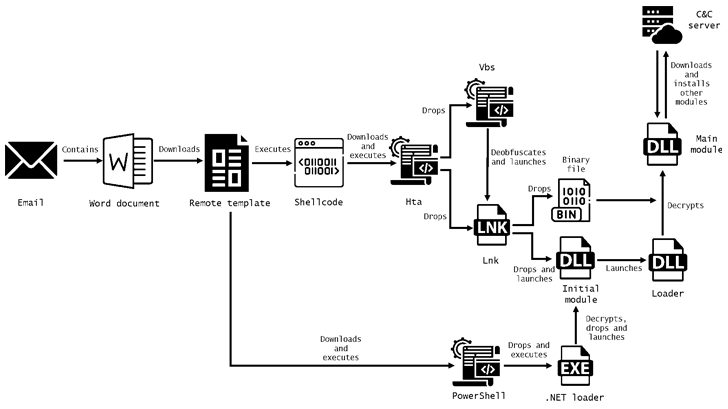
Authorities entities in Ukraine have been breached as a part of a brand new marketing campaign that leveraged trojanized variations of Home windows 10 installer recordsdata to conduct post-exploitation actions.
Mandiant, which found the provision chain assault round mid-July 2022, stated the malicious ISO recordsdata had been distributed by way of Ukrainian- and Russian-language Torrent web sites. It is monitoring the menace cluster as UNC4166.
“Upon set up of the compromised software program, the malware gathers info on the compromised system and exfiltrates it,” the cybersecurity firm stated in a technical deep dive revealed Thursday.
Though the adversarial collective’s provenance is unknown, the intrusions are stated to have focused organizations that had been beforehand victims of disruptive wiper assaults attributed to APT28, a Russian state-sponsored actor.
The ISO file, per the Google-owned menace intelligence agency, was designed to disable the transmission of telemetry information from the contaminated laptop to Microsoft, set up PowerShell backdoors, in addition to block automated updates and license verification.
The first objective of the operation seems to have been info gathering, with extra implants deployed to the machines, however solely after conducting an preliminary reconnaissance of the compromised surroundings to find out if it accommodates the intelligence of worth.
These included Stowaway, an open supply proxy software, Cobalt Strike Beacon, and SPAREPART, a light-weight backdoor programmed in C, enabling the menace actor to execute instructions, harvest information, seize keystrokes and screenshots, and export the data to a distant server.
In some cases, the adversary tried to obtain the TOR anonymity browser onto the sufferer’s machine. Whereas the precise motive for this motion just isn’t clear, it is suspected that it might have served in its place exfiltration route.
SPAREPART, because the identify implies, is assessed to be a redundant malware deployed to take care of distant entry to the system ought to the opposite strategies fail. It is also functionally similar to the PowerShell backdoors dropped early on within the assault chain.
“The usage of trojanized ISOs is novel in espionage operations and included anti-detection capabilities signifies that the actors behind this exercise are safety aware and affected person, because the operation would have required a major time and assets to develop and look forward to the ISO to be put in on a community of curiosity,” Mandiant stated.
Cloud Atlas Strikes Russia and Belarus
The findings come as Examine Level and Optimistic Applied sciences disclosed assaults staged by an espionage group dubbed Cloud Atlas in opposition to the federal government sector in Russia, Belarus, Azerbaijan, Turkey, and Slovenia as a part of a persistent marketing campaign.
The hacking crew, lively since 2014, has a observe report of attacking entities in Jap Europe and Central Asia. However for the reason that outbreak of the Russo-Ukrainian battle, it has been noticed primarily focusing on entities in Russia, Belarus, and Transnistria.
“The actors are additionally sustaining their concentrate on the Russian-annexed Crimean Peninsula, Lugansk, and Donetsk areas,” Examine Level stated in an evaluation final week.
Cloud Atlas, additionally referred to as Clear Ursa, Inception, and Oxygen, stays unattributed up to now, becoming a member of the likes of different APTs like TajMahal, DarkUniverse, and Metador. The group will get its identify for its reliance on cloud companies like OpenDrive to host malware and for command-and-control (C2).
Assault chains orchestrated by the adversary usually make use of phishing emails containing lure attachments because the preliminary intrusion vector, which in the end result in the supply of a malicious payload by way of an intricate multi-stage sequence.
The malware then proceeds to provoke contact with an actor-controlled C2 server to retrieve extra backdoors able to stealing recordsdata with particular extensions from the breached endpoints.
Assaults noticed by Examine Level, however, culminate in a PowerShell-based backdoor referred to as PowerShower, which was first documented by Palo Alto Networks Unit 42 in November 2018.
A few of these intrusions in June 2022 additionally turned out to achieve success, allowing the menace actor to realize full entry to the community and use instruments like Chocolatey, AnyDesk, and PuTTY to deepen their foothold.
“With the escalation of the battle between Russia and Ukraine, their focus for the previous yr has been on Russia and Belarus and their diplomatic, authorities, power and know-how sectors, and on the annexed areas of Ukraine,” Examine Level added.