Cybersecurity researchers have reported a rise in TrueBot infections, primarily concentrating on Mexico, Brazil, Pakistan, and the U.S.
Cisco Talos mentioned the attackers behind the operation have moved from utilizing malicious emails to different supply strategies such because the exploitation of a now-patched distant code execution (RCE) flaw in Netwrix auditor in addition to the Raspberry Robin worm.
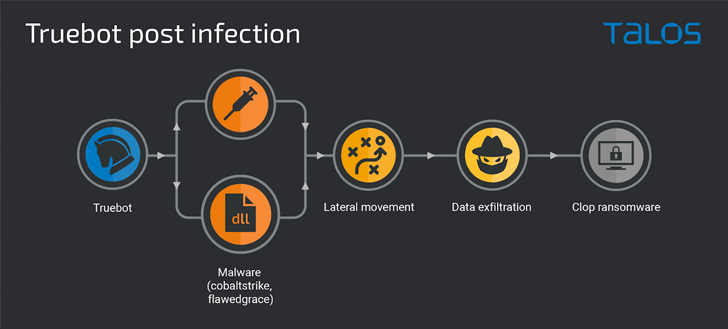
“Put up-compromise exercise included information theft and the execution of Clop ransomware,” safety researcher Tiago Pereira mentioned in a Thursday report.
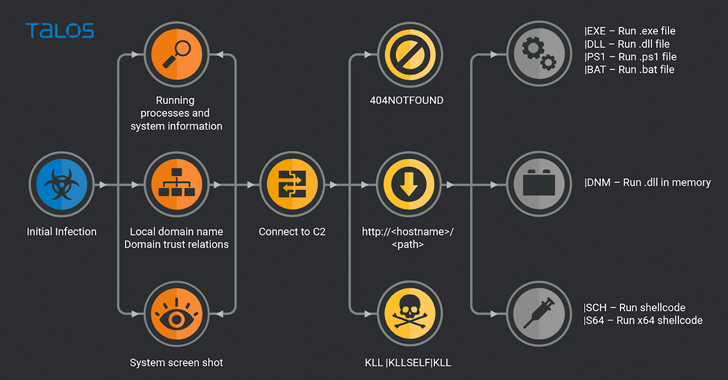
TrueBot is a Home windows malware downloader that is attributed to a menace actor tracked by Group-IB as Silence, a Russian-speaking crew believed to share associations with Evil Corp (aka DEV-0243) and TA505.
The primary-stage module capabilities as an entry level for subsequent post-exploitation actions, together with info theft utilizing a hitherto unknown customized information exfiltration utility dubbed Teleport, the cybersecurity agency mentioned.
The usage of Raspberry Robin – a worm primarily unfold by way of contaminated USB drives – as a supply vector for TrueBot was highlighted just lately by Microsoft, which it mentioned is a part of a “complicated and interconnected malware ecosystem.”
In what’s an extra signal of enmeshed collaboration with different malware households, Raspberry Robin has additionally been noticed deploying FakeUpdates (aka SocGholish) on compromised programs, finally resulting in ransomware-like conduct linked to Evil Corp.
Microsoft is monitoring the operators of the USB-based malware as DEV-0856 and the Clop ransomware assaults that occur through Raspberry Robin and TrueBot underneath the rising menace cluster DEV-0950.
“DEV-0950 historically makes use of phishing to amass the vast majority of their victims, so this notable shift to utilizing Raspberry Robin permits them to ship payloads to current infections and transfer their campaigns extra rapidly to ransomware levels,” the Home windows maker famous in October 2022.
The newest findings from Cisco Talos present that the Silence APT carried out a small set of assaults between mid-August and September 2022 by abusing a crucial RCE vulnerability in Netwrix auditor (CVE-2022-31199, CVSS rating: 9.8) to obtain and run TrueBot.
The truth that the bug was weaponized merely a month after its public disclosure by Bishop Fox in mid-July 2022 means that “attackers aren’t solely looking out for brand spanking new an infection vectors, however are additionally capable of rapidly check them and incorporate them into their workflow,” Pereira mentioned.
TrueBot infections in October, nonetheless, entailed the usage of a distinct assault vector – i.e., Raspberry Robin – underscoring Microsoft’s evaluation concerning the USB worm’s central position as a malware distribution platform.
The first operate of TrueBot is to gather info from the host and deploy next-stage payloads corresponding to Cobalt Strike, FlawedGrace, and Teleport. That is adopted by the execution of the ransomware binary after harvesting related info.
The Teleport information exfiltration instrument can also be notable for its means to restrict add speeds and file sizes, thereby inflicting the transmissions to go undetected by monitoring software program. On prime of that, it may possibly erase its personal presence from the machine.
A more in-depth have a look at the instructions issued through Teleport reveals that this system is being solely used to gather recordsdata from OneDrive and Downloads folders in addition to the sufferer’s Outlook e-mail messages.
“The Raspberry Robin supply led to the creation of a botnet of over 1,000 programs that’s distributed worldwide, however with specific deal with Mexico, Brazil, and Pakistan,” Pereira mentioned.
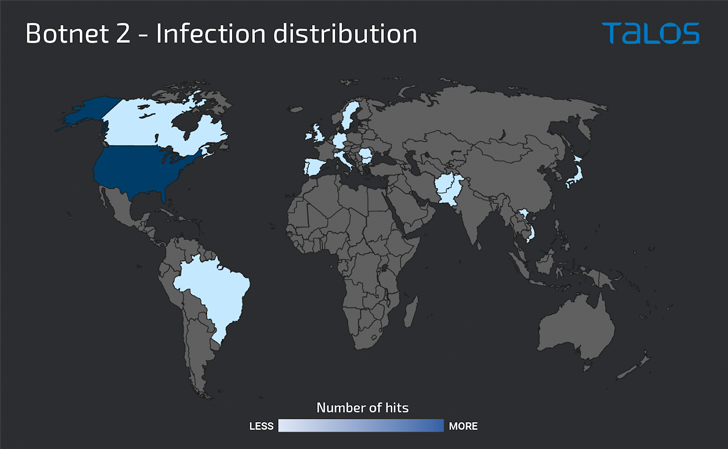
The attackers, nonetheless, seem to have switched to an unknown TrueBot distribution mechanism beginning in November, with the vector succeeding in co-opting over 500 internet-facing Home windows servers situated within the U.S., Canada, and Brazil right into a botnet.