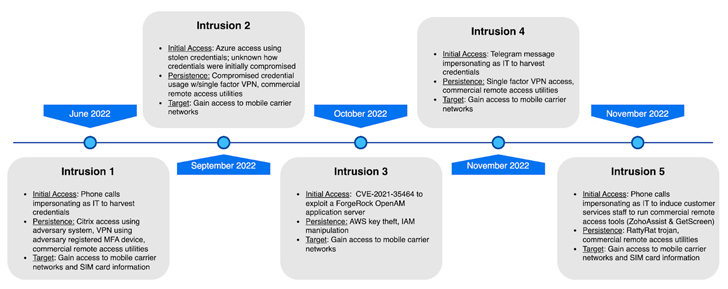
A persistent intrusion marketing campaign has set its eyes on telecommunications and enterprise course of outsourcing (BPO) corporations at lease since June 2022.
“The tip goal of this marketing campaign seems to be to achieve entry to cellular provider networks and, as evidenced in two investigations, carry out SIM swapping exercise,” CrowdStrike researcher Tim Parisi mentioned in an evaluation printed final week.
The financially motivated assaults have been attributed by the cybersecurity firm to an actor tracked as Scattered Spider.
Preliminary entry to the goal atmosphere is claimed to be undertaken by means of quite a lot of strategies starting from social engineering utilizing cellphone calls and messages despatched by way of Telegram to impersonate IT personnel.
This method is leveraged to direct victims to a credential harvesting website or trick them into putting in industrial distant monitoring and administration (RMM) instruments like Zoho Help and Getscreen.me.
Ought to the goal accounts be secured by two-factor authentication (2FA), the risk actor both satisfied the sufferer into sharing the one-time password or employed a method known as immediate bombing, which was put to make use of within the latest breaches of Cisco and Uber.
In an alternate an infection chain noticed by CrowdStrike, a consumer’s stolen credentials beforehand obtained by means of unknown means have been utilized by the adversary to authenticate to the group’s Azure tenant.
One other occasion concerned the exploitation of a crucial distant code execution bug in ForgeRock OpenAM entry administration resolution (CVE-2021-35464) that got here below lively exploitation final 12 months.
Lots of the assaults additionally concerned Scattered Spider getting access to the compromised entity’s multi-factor authentication (MFA) console to enroll their very own gadgets for persistent distant entry by means of reliable distant entry instruments to keep away from elevating purple flags.
Preliminary entry and persistence steps are adopted by reconnaissance of Home windows, Linux, Google Workspace, Azure Energetic Listing, Microsoft 365, and AWS environments in addition to conducting lateral motion, whereas additionally downloading extra instruments to exfiltrate VPN and MFA enrollment information in choose circumstances.
“These campaigns are extraordinarily persistent and brazen,” Parisi famous. “As soon as the adversary is contained or operations are disrupted, they instantly transfer to focus on different organizations throughout the telecom and BPO sectors.”