A brand new information wiper malware referred to as CryWiper has been discovered focusing on Russian authorities companies, together with mayor’s workplaces and courts.
“Though it disguises itself as a ransomware and extorts cash from the sufferer for ‘decrypting’ information, [it] doesn’t really encrypt, however purposefully destroys information within the affected system,” Kaspersky researchers Fedor Sinitsyn and Janis Zinchenko mentioned in a write-up.
Further particulars of the assaults have been shared by the Russian-language information publication Izvestia. The intrusions haven’t been attributed to a selected adversarial group thus far.
A C++-based malware, CryWiper is configured to determine persistence through a scheduled activity and talk with a command-and-control (C2) server to provoke the malicious exercise.
Apart from terminating processes associated to database and e mail servers, the malware is provided with capabilities to delete shadow copies of information and modify the Home windows Registry to forestall RDP connections in a possible try and hinder incident response efforts.
Because the final step, the wiper corrupts all information except these with “.exe,” “.dll,” “lnk,” “.sys,” and “.msi” extensions, whereas additionally skipping particular directories, together with C:Home windows, Boot, and tmp, which might in any other case render the machine inoperable.
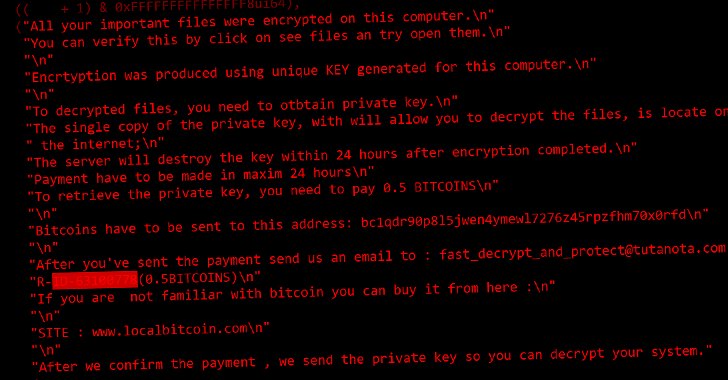
The information overwritten with rubbish information are subsequently appended with an extension referred to as “.CRY,” following which a ransom be aware is dropped to offer the impression that it is a ransomware program, urging the sufferer to pay 0.5 Bitcoin to get better entry.
“The exercise of CryWiper as soon as once more reveals that the cost of the ransom doesn’t assure the restoration of information,” the researchers mentioned, stating the malware “intentionally destroys the contents of information.”
CryWiper is the second retaliatory wiper malware pressure geared toward Russia after RURansom, a .NET-based wiper that was discovered focusing on entities within the nation earlier this March.
The continuing battle between Russia and Ukraine has concerned the deployment of a number of wipers, with the latter hit with a variety of malware similar to WhisperGate, HermeticWiper, AcidRain, IsaacWiper, CaddyWiper, Industroyer2, and DoubleZero.
“Wipers could be efficient whatever the technical abilities of the attacker, as even the only wiper can wreak havoc on affected methods,” Trellix researcher Max Kersten mentioned in an evaluation of harmful malware final month.
“The required time to create such a bit of malware is low, particularly when in comparison with advanced espionage backdoors and the often-accompanying vulnerabilities which can be used. The return of funding needn’t be excessive in these circumstances, though it’s unlikely that just a few wipers are to wreak that a lot havoc in and of themselves.”