The Lazarus Group menace actor has been noticed leveraging faux cryptocurrency apps as a lure to ship a beforehand undocumented model of the AppleJeus malware, in accordance with new findings from Volexity.
“This exercise notably includes a marketing campaign probably focusing on cryptocurrency customers and organizations with a variant of the AppleJeus malware by the use of malicious Microsoft Workplace paperwork,” researchers Callum Roxan, Paul Rascagneres, and Robert Jan Mora mentioned.
The North Korean authorities is understood to undertake a three-pronged strategy by using malicious cyber exercise designed to gather intelligence, conduct assaults, and generate illicit income for the sanctions hit nation. The threats are collectively tracked underneath the identify Lazarus Group (aka Hidden Cobra or Zinc).
“North Korea has performed cyber theft towards monetary establishments and cryptocurrency exchanges worldwide, doubtlessly stealing a whole bunch of hundreds of thousands of {dollars}, in all probability to fund authorities priorities, equivalent to its nuclear and missile applications,” per the 2021 Annual Menace Evaluation launched by U.S. intelligence companies.
Earlier this April, the Cybersecurity and Infrastructure Safety Company (CISA) warned of an exercise cluster dubbed TraderTraitor that targets cryptocurrency exchanges and buying and selling firms by means of trojanized crypto apps for Home windows and macOS.
Whereas the TraderTraitor assaults culminate within the deployment of the Manuscrypt distant entry trojan, the brand new exercise makes use of a supposed crypto buying and selling web site named BloxHolder, a copycat of the professional HaasOnline platform, to ship AppleJeus by way of an installer file.
AppleJeus, first documented by Kaspersky in 2018, is designed to reap details about the contaminated system (i.e., MAC deal with, pc identify, and working system model) and obtain shellcode from a command-and-control (C2) server.
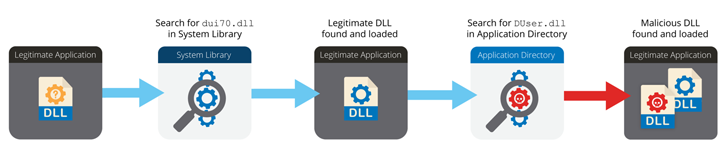
The assault chain is claimed to have undergone a slight deviation in October 2022, with the adversary shifting from MSI installer recordsdata to a booby-trapped Microsoft Excel doc that makes use of macros to obtain a remotely hosted payload, a PNG picture, from OpenDrive.
The thought behind the change is more likely to cut back static detection by safety merchandise, Volexy mentioned, including it could not get hold of the picture file (“Background.png”) from the OpenDrive hyperlink however famous it embeds three recordsdata, together with an encoded payload that is subsequently extracted and launched on the compromised host.
“The Lazarus Group continues its effort to focus on cryptocurrency customers, regardless of ongoing consideration to their campaigns and ways,” the researchers concluded.