D4TA-HUNTER is a device created so as to automate the gathering of details about the staff of an organization that’s going to be audited for moral hacking.
As well as, on this device we will discover within the “search firm” part by inserting the area of an organization, emails of workers, subdomains and IP’s of servers.
Register on https://rapidapi.com/rohan-patra/api/breachdirectory
git clone https://github.com/micro-joan/D4TA-HUNTER
cd D4TA-HUNTER/
chmod +x run.sh
./run.sh
After executing the appliance launcher you’ll want to have all of the parts put in, the launcher will examine one after the other, and within the case of not having any element put in it’s going to present you the assertion that you will need to enter to put in it:
First you will need to have a free or paid api-key from BreachDirectory.org, if you do not have one and do a search D4TA-HUNTER supplies you with a information on the way to get one.
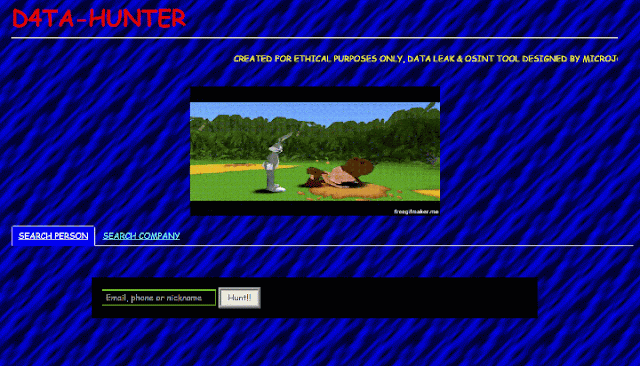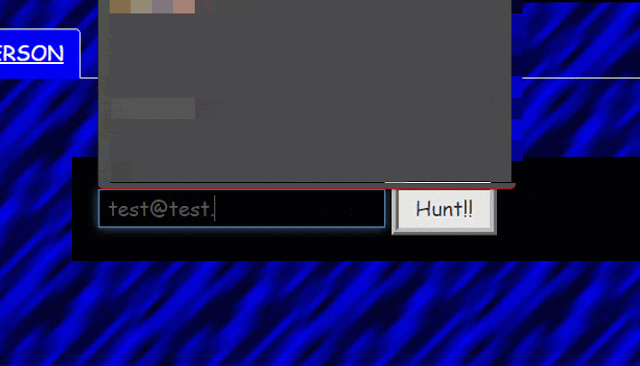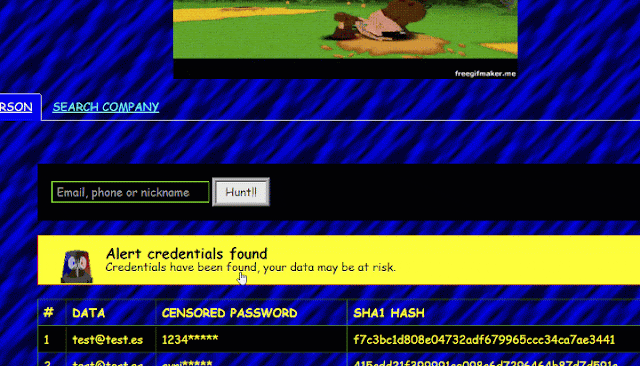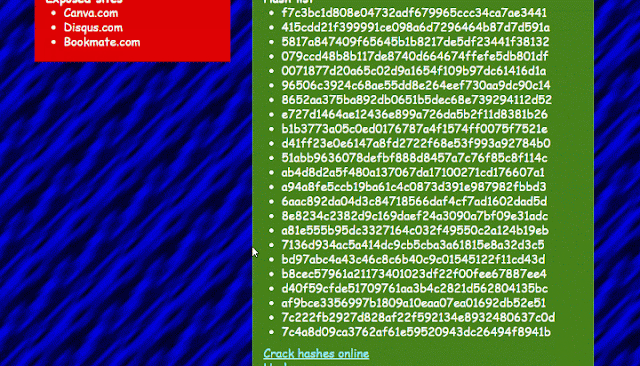
After you have the api-key it is possible for you to to seek for emails, with the benefit of displaying you a listing of all of the password hashes prepared so that you can copy and paste into one of many on-line assets supplied by D4TA-HUNTER to crack passwords 100 % free.
You may as well insert a site of an organization and D4TA-HUNTER will seek for worker emails, subdomains which may be of curiosity along with IP’s of machines discovered:
| Service | Features | Standing |
|---|---|---|
| BreachDirectory.org | Electronic mail, cellphone or nick leaks |
(free plan) |
| TheHarvester | Domains and emails of firm |
Free |
| Kalitorify | Tor search |
Free |