Netcat, the All- Highly effective
Netcat is a type of few tools–like nmap, Metasploit, Wireshark and few others– that each hacker ought to be aware of. It’s easy, elegant and has a mess of makes use of.
For example, netcat can be utilized to;
-
scan to see if a port is open on a distant system
-
pull the banner from a distant system
-
connect with a community service manually
-
distant administration
This lesson might be devoted to studying to make use of netcat and its encrypted cousin, cryptcat. Later in your research, we are going to discover many makes use of for this easy software.
Like so many functions within the Linux world, netcat runs in a consumer and server mode. Which means we should designate one facet the server and one facet the consumer, when utilizing ncat.
I. Netcat Fundamentals
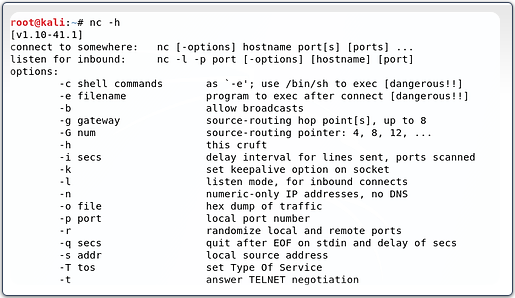
Let’s begin off by wanting on the assist display for netcat. When utilizing netcat, the command is just “nc”. To get the assistance display then, kind;
kali > nc -h

Be aware a couple of key switches;
-e execute
-l pay attention mode
-n numeric mode (no DNS. Its quicker)
-p designates the port
-u UDP mode
-v verbose output
II. Create a Easy TCP Connection
Netcat be used to create easy TCP or UDP connection to system to see whether or not the port and repair out there. So, as an example, if I wished to hook up with the SSH on one other Kali system, I can kind;
kali > nc -vn 192.168.1.103 22

As you’ll be able to see, netcat was ready to hook up with OpenSSH on a distant server and the server marketed the service with its banner
(SSH-2.0-OpenSSH_4.7p1 Debian-8Ubuntu1).
III. Banner Grabbing
We will additionally use netcat to “seize” the banner on net servers by connecting to port 80 after which sending a HTTP / HEAD/1.0 request.
kali > nc -vn 192.168.1.103 80
HEAD / HTTP/1.0
Make sure to hit “Enter” a pair instances after typing the HEAD request to tug the banner.

As you’ll be able to see, we grabbed the banner of Apache 2.2.8 net server operating on Ubuntu.
IV. Opening TCP connection between two machines for “chat”
Netcat is able to making a easy TCP or UDP connection between two computer systems after which open a communication channel between them. Let’s open a listener on the distant system first.
kali > nc -l -p6996
Then connect with that listener from a distant machine
kali > nc 192.168.1.105 6996
When it connects, I can then start typing my message, akin to “What’s the greatest place to study hacking?”

That message will then seem on the distant system with the listener. The listener machine can then reply, “For sure, Hackers-Come up!”

…after which the distant machine receives the response!

On this means, we will create a non-public “chat room” between any two machines!
V. Transferring Recordsdata with Netcat
One of many easy wonders of netcat is its capacity to switch information between computer systems. By creating this easy connection, we will then use that connection to switch information between two computer systems. This may be extraordinarily helpful as a community administrator and much more helpful as a hacker. Netcat can be utilized to add and obtain information from and to the goal system.
Let’s create a file known as “hacker_training”.
kali > echo “That is first module in Hacker Fundamentals at Hackers-Come up” > hacker_training
Then, let’s view the contents of that file utilizing the Linux command “cat”.
kali > cat hacker_training

Now, let’s open a listener on the distant system.
kali > nc -l -p6996
Subsequent, let’s ship the file to the distant system.
kali > nc 192.168.1.103 6996 <hacker_training

Be aware, that we use the < to direct the file to netcat.
Lastly, return to our listening system and we must always discover that the file has been transferred and seems on the display!

VI. Distant Administration with netcat
Most likely probably the most malicious use of netcat– and the simplest for the hacker –is the power to make use of netcat for distant administration. We will use netcat’s capacity to execute instructions to present the distant connection a shell on the listening system. We will do that in a Linux/Unix machine by making /bin/sh out there to the distant reference to the -e (execute), like beneath. If we have been connecting to a Home windows machine, we might use cmd.exe (-e cmd.exe) as an alternative of /bin/sh.
kali > nc -l -p6996 -e /bin/sh
Now after I connect with the distant machine, I ought to be capable of get a shell on the distant system. Discover that when I connect with the distant system, I get only a clean line, no command immediate, nothing (if we connect with a Home windows system, although, we are going to get the normal Home windows C: > immediate). This may be complicated to the novice.
If we then kind “ls -l” , we get a listing itemizing from the listing that the place we began the netcat listener on the distant system and once we enter “ifconfig”, we will see that it returns the IP handle of our distant system.

VII. Cryptcat
Cryptcat is netcat’s encrypted cousin. Which means we will make a connection to a distant machine the place all our visitors is encrypted with a number of the strongest encryption algorithms out there anyplace, Two-fish (Two-fish encryption is sort of as robust as AES). You possibly can obtain it at www.cryptcat.sourceforge.web, however if you’re utilizing Kali, it’s already put in. Though the switches are largely the identical as netcat, the command is “cryptcat” quite than “nc”.