
When there’s a lot unhealthy information on this planet of cybersecurity, it’s at all times good to share a optimistic story.
Researchers at cybersecurity agency Unit 221B have revealed that they’ve been secretly serving to victims of the Zeppelin ransomware decrypt their laptop methods since 2020.
Victims of the Zeppelin ransomware since its emergence in 2019 have included companies, important infrastructure organisations, defence contractors, academic establishments, and the healthcare and medical industries.
Sometimes demanding a ransom within the area of US $50,000 (though ransoms of over US $1 million have additionally been requested), Zeppelin leaves a calling card alongside the recordsdata it has encrypted.
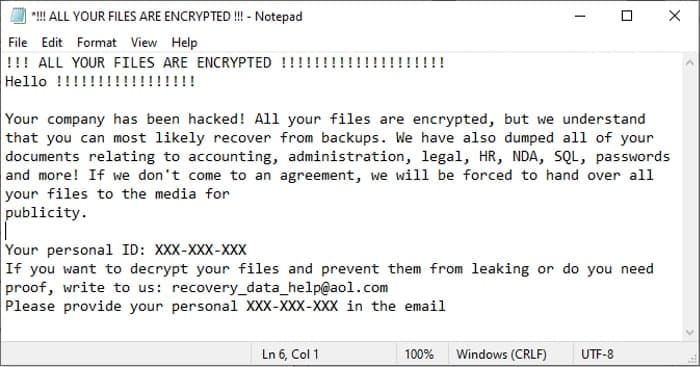
Your organization has been hacked! All of your recordsdata are encrypted, however we perceive that you can probably get well from backups. We have now additionally dumped your whole paperwork referring to accounting, administration, authorized, HR, NDA, SQL, passwords and extra! If we don’t come to an settlement, we shall be compelled handy over all of your recordsdata to the media for publicity.
The boffins at Unit 221B turned their consideration to the Zeppelin ransomware after it focused charities, non-profit organisations, and even homeless shelters – all of which clearly have deserving issues to direct their cash in direction of than the pockets of extortionists.
Or, as a weblog publish on Unit 221B’s web site eloquently places it:
A normal Unit 221B rule of thumb round our places of work is:
“Don’t [REDACTED] with the homeless or sick! It can merely set off our ADHD and we are going to get into that hyper-focus mode that’s good should you’re a superb man, however not so nice in case you are an ***gap.”
What Unit 22B’s researchers found was that Zeppelin’s encryption movement contained a vulnerability, that quickly left a key within the registry. Full particulars of how Unit 221B found the flaw, and have been then in a position to exploit it to crack keys on victims’ computer systems, are contained in a technical weblog publish on the agency’s web site.
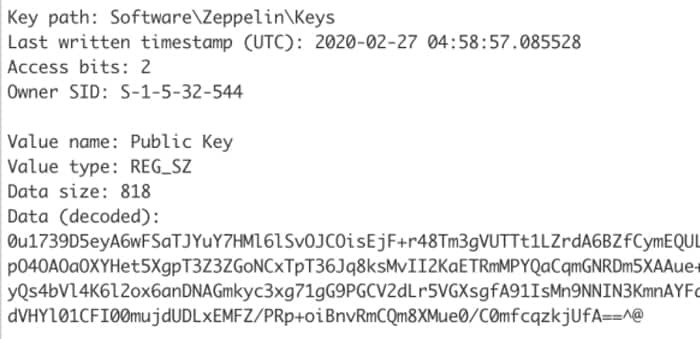
The tip consequence was that the researchers have been in a position to produce a decryption software that victims might run on contaminated methods, that may extract a key. The keys would then be uploaded to some vital computing energy – 20 servers (every with 40 CPUs on board) donated by Digital Ocean – which might finally, after six hours huffing and puffing, crack the encryption key.
It’s a powerful achievement, which could have helped organisations that badly wanted help within the aftermath of a Zeppelin ransomware assault.
And what additionally impresses me is that the researchers stored their discovery quiet all of this time, figuring out that in the event that they bragged about their accomplishment it could solely attain the ears of the ransomware gangs utilizing Zeppelin – who would change their method, and put but extra organisations at even larger danger.
It’s only after a big drop within the variety of Zeppelin victims that Unit 221B has chosen to disclose particulars of its work. The software continues to be accessible freed from cost, and may nonetheless work towards even the newest variations of Zeppelin.
The researchers credit score the safety consultants at Cylance for his or her prior work analysing Zeppelin, internet hosting big Digital Ocean for offering laptop energy, and the builders of CADO-NFS for his or her help with the challenge.
Discovered this text fascinating? Comply with Graham Cluley on Twitter or Mastodon to learn extra of the unique content material we publish.

