The Luna Moth marketing campaign has extorted lots of of 1000’s of {dollars} from a number of victims within the authorized and retail sectors.
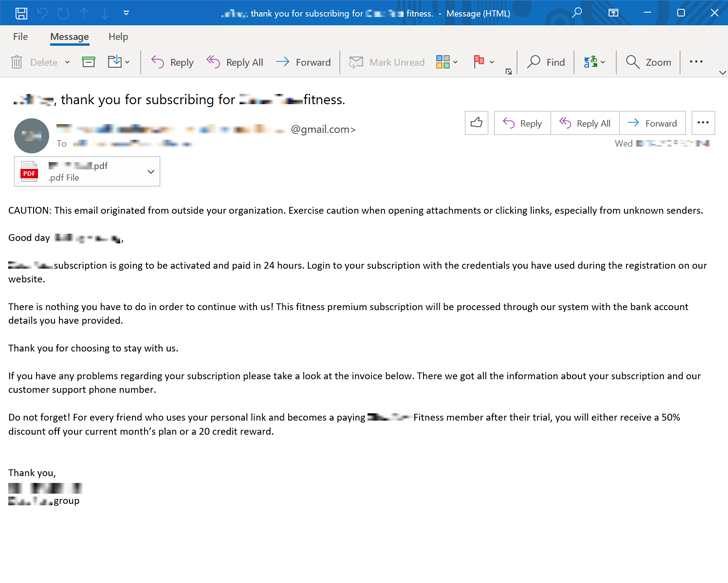
The assaults are notable for using a way known as callback phishing or telephone-oriented assault supply (TOAD), whereby the victims are social engineered into making a telephone name via phishing emails containing invoices and subscription-themed lures.
Palo Alto Networks Unit 42 stated the assaults are the “product of a single extremely organized marketing campaign,” including, “this risk actor has considerably invested in name facilities and infrastructure that is distinctive to every sufferer.”
The cybersecurity agency described the exercise as a “pervasive multi-month marketing campaign that’s actively evolving.”
What’s notable about callback phishing is that the e-mail messages are utterly devoid of any malicious attachment or booby-trapped hyperlink, permitting them to evade detection and slip previous e mail safety options.
These messages usually include an bill that features a telephone quantity that the customers can name to cancel the supposed subscription. In actuality, nonetheless, the victims are routed to an actor-controlled name middle and linked to a reside agent on the opposite finish, who finally ends up putting in a distant entry instrument for persistence.
“The attacker will then search to establish helpful data on the sufferer’s pc and linked file shares, and they’re going to quietly exfiltrate it to a server they management utilizing a file switch instrument,” Unit 42 researcher Kristopher Russo stated.
The marketing campaign could also be useful resource intensive, however can also be technically much less subtle and prone to have a a lot greater success fee than different phishing assaults.
On prime of that, it allows extortion with out encryption, allowing malicious actors to plunder delicate knowledge sans the necessity to deploy ransomware to lock the recordsdata after exfiltration.
The Luna Moth actor, also called Silent Ransom, has change into an skilled of kinds with regards to pulling off such schemes. In accordance with AdvIntel, the cybercrime group is believed to be the mastermind behind the BazarCall assaults final yr.
To offer these assaults a veneer of legitimacy, the adversaries, as a substitute of dropping a malware like BazarLoader, reap the benefits of respectable instruments like Zoho Help to remotely work together with a sufferer’s pc, abusing the entry to deploy different trusted software program akin to Rclone or WinSCP for harvesting knowledge.
Extortion calls for vary from two to 78 Bitcoin based mostly on the group focused, with the risk actor creating distinctive cryptocurrency wallets for every fee. The adversary can also be stated to supply reductions of practically 25% for immediate fee, though there isn’t any assure that the info is deleted.
“The risk actors behind this marketing campaign have taken nice pains to keep away from all non-essential instruments and malware, to attenuate the potential for detection,” Russo stated. “Since there are only a few early indicators {that a} sufferer is below assault, worker cybersecurity consciousness coaching is the primary line of protection.”