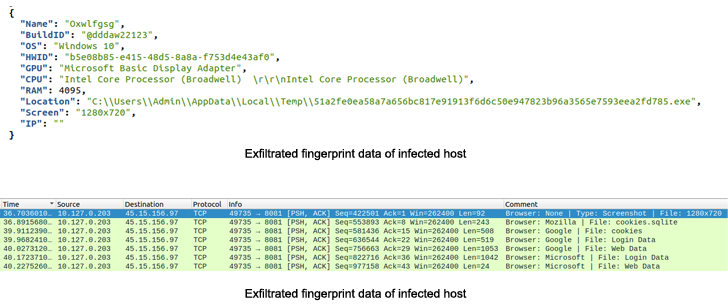
A nascent Go-based malware often called Aurora Stealer is being more and more deployed as a part of campaigns designed to steal delicate data from compromised hosts.
“These an infection chains leveraged phishing pages impersonating obtain pages of respectable software program, together with cryptocurrency wallets or distant entry instruments, and the 911 technique making use of YouTube movies and Search engine optimization-poised pretend cracked software program obtain web sites,” cybersecurity agency SEKOIA stated.
First marketed on Russian cybercrime boards in April 2022, Aurora was provided as a commodity malware for different menace actors, describing it as a “multi-purpose botnet with stealing, downloading and distant entry capabilities.”
Within the intervening months, the malware has been scaled all the way down to a stealer that may harvest recordsdata of curiosity, information from 40 cryptocurrency wallets, and functions like Telegram.
Aurora additionally comes with a loader that may deploy a next-stage payloading utilizing a PowerShell command.
The cybersecurity firm stated no less than completely different cybercrime teams, known as traffers, who’re answerable for redirecting consumer’s site visitors to malicious content material operated by different actors, have added Aurora to their toolset, both completely or alongside RedLine and Raccoon.
“Aurora is one other infostealer focusing on information from browsers, cryptocurrency wallets, native programs, and appearing as a loader,” SEKOIA stated. “Offered at a excessive worth on market locations, collected information is of specific curiosity to cybercriminals, permitting them to hold out follow-up profitable campaigns, together with Large Sport Looking operations.”
The event additionally comes as researchers from Palo Alto Networks Unit 42 detailed an enhanced model of one other stealer known as Typhon Stealer.
The brand new variant, dubbed Typhon Reborn, is designed to steal from cryptocurrency wallets, internet browsers, and different system information, whereas eradicating beforehand present options like keylogging and cryptocurrency mining in a probable try to reduce detection.
“Typhon Stealer supplied menace actors with a simple to make use of, configurable builder for rent,” Unit 42 researchers Riley Porter and Uday Pratap Singh stated.
“Typhon Reborn’s new anti-analysis methods are evolving alongside business traces, changing into more practical within the evasion techniques whereas broadening their toolset for stealing sufferer information.”