Google Cloud final week disclosed that it recognized 34 completely different hacked launch variations of the Cobalt Strike software within the wild, the earliest of which shipped in November 2012.
The variations, spanning 1.44 to 4.7, add as much as a complete of 275 distinctive JAR information, in line with findings from the Google Cloud Menace Intelligence (GCTI) crew. The newest model of Cobalt Strike is model 4.7.2.
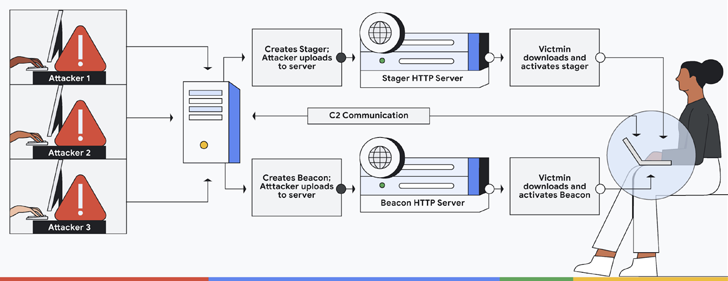
Cobalt Strike, developed by Fortra (née HelpSystems), is a well-liked adversarial framework utilized by pink groups to simulate assault eventualities and take a look at the resilience of their cyber defenses.
It includes a Workforce Server that acts because the command-and-control (C2) hub to remotely commandeer contaminated gadgets and a stager that is designed to ship a next-stage payload known as the Beacon, a fully-featured implant that experiences again to the C2 server.
Given its wide-ranging suite of options, unauthorized variations of the software program have been more and more weaponized by many a risk actor to advance their post-exploitation actions.
“Whereas the intention of Cobalt Strike is to emulate an actual cyber risk, malicious actors have latched on to its capabilities, and use it as a strong software for lateral motion of their sufferer’s community as a part of their second-stage assault payload,” Greg Sinclair, a reverse engineer at Google’s Chronicle subsidiary, stated.
In a bid to deal with this abuse, GCTI has launched a set of open supply YARA Guidelines to flag completely different variants of the software program utilized by malicious hacking teams.
The thought is to “excise the dangerous variations whereas leaving the respectable ones untouched,” Sinclair stated, including “our intention is to maneuver the software again to the area of respectable pink groups and make it more durable for dangerous guys to abuse.”