Digital transformation is a journey, and very like any journey, a little bit of preparation can go a good distance in driving a profitable consequence. Getting ready for any journey contains figuring out the place you wish to go, deciding on the easiest way to get there, and gathering the tools, providers, and provides you’ll want alongside the way in which.
An IT transformation journey usually begins with software transformation, the place you progress purposes out of the information middle and into the cloud. Then, community transformation turns into essential to allow customers to entry purposes that at the moment are broadly dispersed—transferring from a hub-and-spoke community structure to a direct connectivity strategy. This, in flip, drives a necessity for safety transformation, the place you shift from a castle-and-moat safety strategy to a zero-trust structure.
Whereas the aforementioned order is typical, there are just a few alternative ways to realize comparable outcomes. You need to start your journey in the direction of zero belief wherever you’re feeling most comfy or ready. If it makes extra sense to your group to start with safety transformation earlier than app transformation, you possibly can.
Assess Your Gear
Fortress-and-moat safety architectures, leveraging firewalls, VPNs, and centralized safety home equipment, labored properly when purposes lived within the information middle and customers labored within the workplace. It was the appropriate tools for the job on the time. As we speak, although, your workforce works from all over the place, and purposes have moved out of the information middle and into public clouds, SaaS, and different components of the web. These firewalls, VPNs, and legacy safety {hardware} stacks weren’t designed to satisfy the wants of at present’s extremely distributed enterprise and have outlived their usefulness.
To grant customers entry to purposes, VPNs and firewalls should join customers to your community, basically extending the community to all of your distant customers, units, and areas. This places your group at larger threat by giving attackers extra alternatives to compromise customers, units, and workloads, and extra methods to maneuver laterally to succeed in high-value property, extract delicate information, and inflict harm on your corporation. Defending your extremely distributed customers, information, and purposes requires a brand new strategy—a greater strategy.
Mapping the Finest Route
On the subject of safety transformation, progressive leaders are turning to zero belief. Not like perimeter-based safety approaches that depend on firewalls and implicit belief and supply broad entry as soon as belief is established, zero belief is a holistic strategy to safety based mostly on the precept of least-privileged entry and the concept no person, system, or workload ought to be inherently trusted. It begins with the idea that all the things is hostile, and grants entry solely after identification and context are verified and coverage checks are enforced.
Attaining true zero belief requires greater than pushing firewalls to the cloud. It requires a brand new structure, born within the cloud and delivered natively by way of the cloud, to securely join customers, units, and workloads to purposes with out connecting to the community.
As with every vital journey, it’s useful to interrupt your journey to zero belief into varied legs that clearly outline the trail whereas retaining the last word vacation spot in thoughts. When contemplating your strategy, seven important components will allow you to dynamically and repeatedly assess threat and securely dealer communications over any community, from any location.
Utilizing these components, your group can implement true zero belief to eradicate your assault floor, stop the lateral motion of threats, and shield your corporation in opposition to compromise and information loss.
These components could be grouped into three sections:
- Confirm identification and context
- Management content material and entry
- Implement coverage
Let’s take a better look.
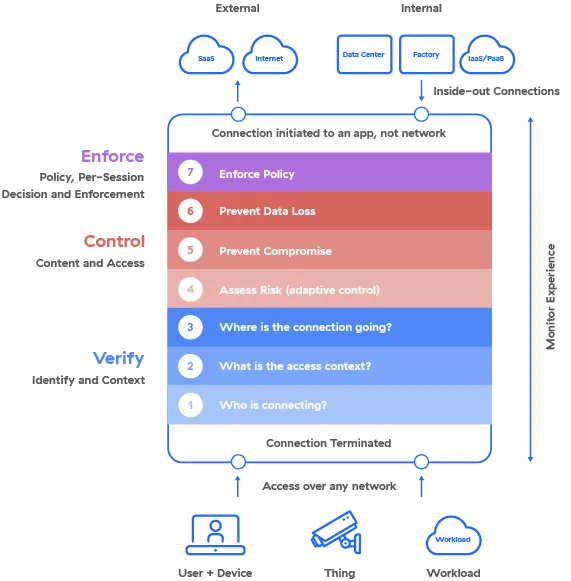
Confirm Identification and Context
The journey begins when a connection is requested. The zero belief structure will start by terminating the connection and verifying identification and context. It seems on the who, what, and the place of the requested connection.
1. Who’s connecting?—The primary important factor is to confirm the person/system, IoT/OT system, or workload identification. That is achieved by way of integrations with third-party identification suppliers (IdPs) as a part of an enterprise identification entry administration (IAM) supplier.
2. What’s the entry context?—Subsequent, the answer should validate the context of the connection requester by trying into particulars such because the position, duty, time of day, location, system kind, and circumstances of the request.
3. The place is the connection going?—The answer subsequent wants to verify that the identification proprietor has the rights and meets the required context to entry the appliance or useful resource based mostly on entity-to-resource segmentation guidelines—the cornerstone of zero belief.
Management Content material and Entry
After verifying identification and context, the zero belief structure evaluates the danger related to the requested connection and inspects visitors to guard in opposition to cyberthreats and the lack of delicate information.
4. Assess threat—The answer ought to use AI to dynamically compute a threat rating. Elements together with system posture, threats, vacation spot, conduct, and coverage ought to be regularly evaluated all through the lifetime of the connection to make sure the danger rating stays updated.
5. Forestall compromise—To determine and block malicious content material and stop compromise, an efficient zero belief structure should decrypt visitors inline and leverage deep content material inspection of entity-to-resource visitors at scale.
6. Forestall information loss—Outbound visitors should be decrypted and inspected to determine delicate information and stop its exfiltration utilizing inline controls or by isolating entry inside a managed surroundings.
Implement Coverage
Earlier than reaching the tip of the journey and finally establishing a connection to the requested inner or exterior software, one remaining factor should be carried out: implementing coverage.
7. Implement coverage—Utilizing the outputs of the earlier components, this factor determines what motion to take relating to the requested connection. The tip purpose will not be a easy move/not move determination. As a substitute, the answer should consistently and uniformly apply coverage on a per session foundation—no matter location or enforcement level—to offer granular controls that finally lead to a conditional permit or conditional block determination.
As soon as an permit determination is reached, a person is granted a safe connection to the web, SaaS app, or inner software.
Securely Attain Your Vacation spot
Your journey to zero belief could be perilous when you’re making an attempt to get there with legacy tools that wasn’t designed for it. Whereas discovering an answer that allows true zero belief might at first appear daunting, start the place it makes essentially the most sense to your group, and let the seven components outlined right here function your information.
Learn extra Accomplice Views from Zscaler.


