Menace searching is the method of on the lookout for malicious exercise and its artifacts in a pc system or community. Menace searching is carried out intermittently in an setting no matter whether or not or not threats have been found by automated safety options. Some menace actors might keep dormant in a corporation’s infrastructure, extending their entry whereas ready for the proper alternative to take advantage of found weaknesses.
Subsequently it is very important carry out menace searching to determine malicious actors in an setting and cease them earlier than they obtain their final aim.
To successfully carry out menace searching, the menace hunter should have a scientific strategy to emulating potential adversary habits. This adversarial habits determines what artifacts may be looked for that point out ongoing or previous malicious exercise.
MITRE ATT&CK
Over time, the safety group has noticed that menace actors have generally used many ways, methods, and procedures (TTPs) to infiltrate and pivot throughout networks, elevate privileges, and exfiltrate confidential knowledge. This has led to the event of assorted frameworks for mapping the actions and strategies of menace actors. One instance is the MITRE ATT&CK framework.
MITRE ATT&CK is an acronym that stands for MITRE Adversarial Ways, Methods, and Widespread Information (ATT&CK). It’s a well-documented data base of real-world menace actor actions and behaviors. MITRE ATT&CK framework has 14 ways and plenty of methods that determine or point out an assault in progress. MITRE makes use of IDs to reference the tactic or method employed by an adversary.
The Wazuh unified XDR and SIEM platform
Wazuh is an open supply unified XDR and SIEM platform. The Wazuh answer is made up of a single common agent that’s deployed on monitored endpoints for menace detection and automatic response. It additionally has central elements (Wazuh server, indexer, and dashboard) that analyze and visualize the safety occasions knowledge collected by the Wazuh agent. It protects on-premises and cloud workloads.
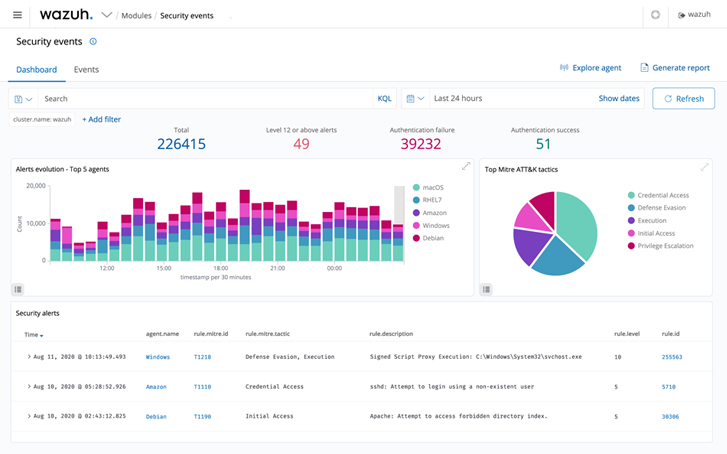 |
| Determine 1: Wazuh safety occasion dashboard |
Menace searching with Wazuh
Menace hunters use numerous instruments, processes, and strategies to seek for malicious artifacts in an setting. These embody however will not be restricted to utilizing instruments for safety monitoring, file integrity monitoring, and endpoint configuration evaluation.
Wazuh gives sturdy capabilities like file integrity monitoring, safety configuration evaluation, menace detection, automated response to threats, and integration with options that present menace intelligence feeds.
Wazuh MITRE ATT&CK module
Wazuh comes with the MITRE ATT&CK module out-of-the-box and menace detection guidelines mapped towards their corresponding MITRE method IDs. This module has 4 elements that are:
a. The intelligence part of the Wazuh MITRE ATT&CK module: Incorporates detailed details about menace teams, mitigation, software program, ways, and methods utilized in cyber assaults. This part helps menace hunters to determine and classify completely different TTPs that adversaries use.
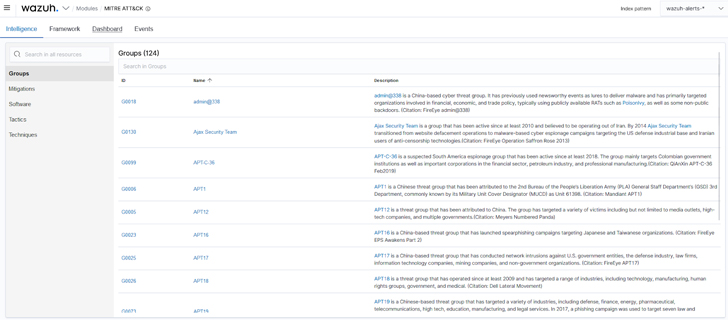 |
| Determine 2: Wazuh MITRE ATT&CK Intelligence |
b. The framework part of the Wazuh MITRE ATT&CK module: Helps menace hunters slim down threats or compromised endpoints. This part makes use of particular methods to see all of the occasions associated to that method and the endpoints the place these occasions occurred.
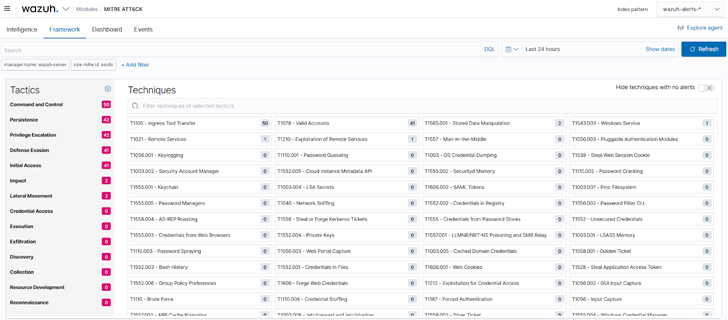 |
| Determine 3: Wazuh MITRE ATT&CK framework |
c. The dashboard part of the MITRE ATT&CK module: Helps to summarize all occasions into charts to help menace hunters in having a fast overview of MITRE associated actions in an infrastructure.
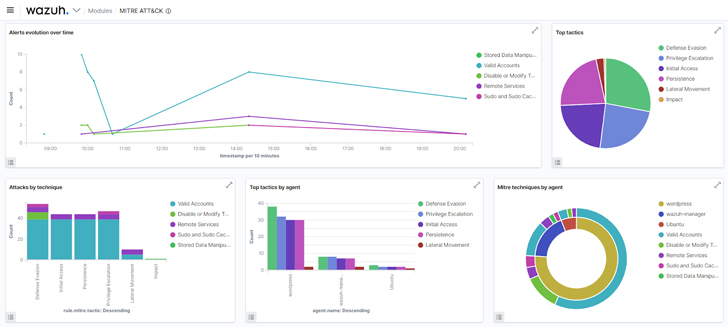 |
| Determine 4: Wazuh MITRE ATT&CK dashboard |
d. The Wazuh MITRE ATT&CK occasions part: Shows occasions in real-time, with their respective MITRE IDs, to raised perceive every reported alert.
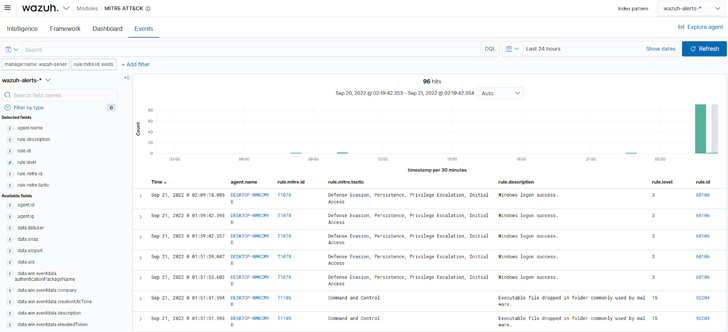 |
| Determine 5: Wazuh MITRE ATT&CK occasions |
Wazuh guidelines and decoders
Wazuh has out-of-the-box guidelines and decoders to parse safety and runtime knowledge generated from completely different sources. Wazuh helps guidelines for various applied sciences (e.g., Docker, CISCO, Microsoft Change), which have been mapped to their applicable MITRE IDs. Customers may create customized guidelines and decoders and map every rule with its applicable MITRE tactic or method. This weblog submit exhibits an instance of leveraging MITRE ATT&CK and Wazuh customized guidelines to detect an adversary.
Safety Configuration Evaluation (SCA) module
The Wazuh SCA module performs periodic scans in endpoints to detect system and software misconfigurations. It may also be used to scan for indicators of compromise, like malicious recordsdata and folders which have been created by malware. Analyzing software program inventories, providers, misconfigurations, and modifications within the configuration on an endpoint will help menace hunters detect assaults underway.
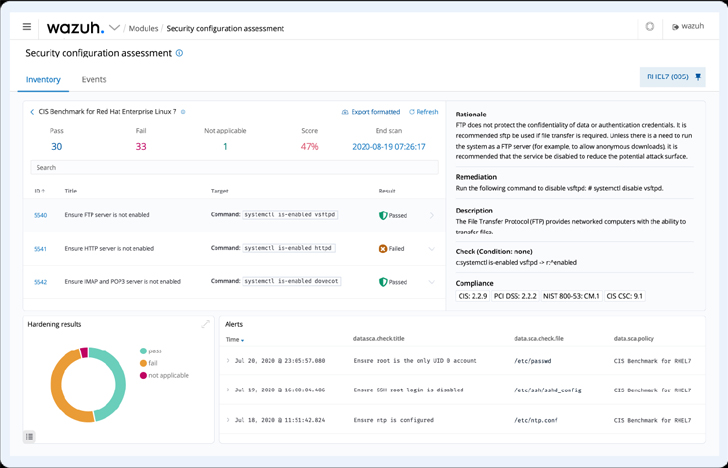 |
| Determine 6: Wazuh SCA dashboard |
Integration with menace intelligence options
On account of its open supply nature, Wazuh gives a possibility to combine with menace intelligence APIs and different safety options. Wazuh integrates with open supply menace intelligence platforms like Virustotal, URLHaus, MISP, and AbuseIPDB to call just a few. Relying on the combination, related alerts seem within the Wazuh dashboard. Particular data, similar to IP addresses, file hashes, and URLs, may be queried utilizing filters on the Wazuh dashboard.
File integrity monitoring
File integrity monitoring (FIM) is used to watch and audit delicate recordsdata and folders on endpoints. Wazuh gives an FIM module that screens and detects modifications in specified directories or recordsdata on an endpoint’s filesystem. The FIM module may detect when recordsdata launched to endpoints match hashes of identified malware.
Wazuh archives
Wazuh archives may be enabled to gather and retailer all safety occasions ingested from monitored endpoints. This function assists menace hunters by offering them with knowledge that can be utilized to create detection guidelines and keep forward of menace actors. Wazuh archives are additionally useful in assembly regulatory compliance the place audit log historical past is required.
Conclusion
The MITRE ATT&CK framework helps to correctly classify and determine threats in response to found TTPs. Wazuh makes use of its devoted MITRE ATT&CK elements to show details about how safety knowledge from endpoints correspond to TTPs. The menace searching capabilities of Wazuh assist cybersecurity analysts to detect obvious cyber assaults in addition to underlying compromises to infrastructure.
Wazuh is a free and open supply platform that can be utilized by organizations with cloud and on-premises infrastructure. Wazuh has one of many fastest-growing open supply group on the earth, the place studying, discussions, and assist is obtainable at zero value. Try this documentation to get began with Wazuh.


