 As ransomware, enterprise e mail compromise, and phishing assaults proceed to escalate, new information sheds mild on the place organizations have to focus to assist put a cease to assault success.
As ransomware, enterprise e mail compromise, and phishing assaults proceed to escalate, new information sheds mild on the place organizations have to focus to assist put a cease to assault success.
We’ve lengthy identified that credentials are the important thing to a profitable cyberattack. They allow preliminary entry to endpoints, lateral motion, entrance to purposes, and entry to information. New information from safety vendor Talos’ Quarterly Report: Incident Response Traits in Q3 2022 exhibits repeatedly that credentials are a fabric focus for menace actors from a number of views.
Perspective 1: Preliminary Assault Vector
Everyone knows that the necessity for credentials are an eventual certainty, however Talos recognized the usage of Legitimate Accounts as the highest an infection vector in Q3, citing circumstances the place “accounts had been misconfigured, not disabled correctly, or had weak passwords.”
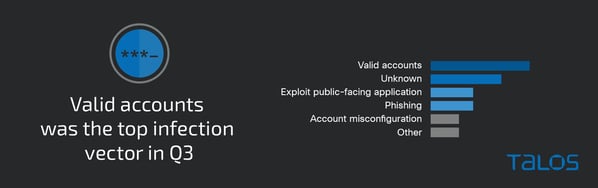
Supply: Talos
Perspective 2: Instruments Used
Menace actors have a variety of native, malicious, and misused legit instruments at their disposal that support in each facet of a cyberattack. What’s fascinating is that, in line with the Talos information, over two-thirds of instruments seen getting used throughout assaults centered on accessing and amassing credentials.
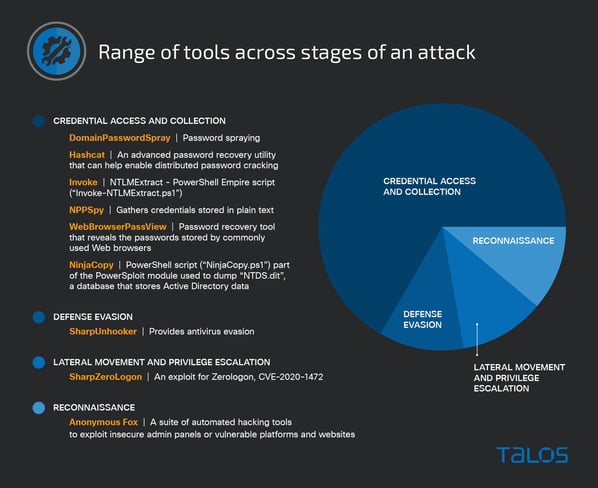
Supply: Talos
Perspective 3: Prime Noticed MITRE ATT&CK Strategies
I’m a giant fan of the ATT&CK framework, because it supplies safety professionals with a strategy to higher perceive the menace actions being taken with a view to create a simpler protection. In line with the Talos information, the MITRE approach T1078 Legitimate Accounts was essentially the most noticed menace motion throughout assaults.
The Talos information supplies goal proof that credentials are a spotlight for assaults as we speak. What’s essential is to cease the misuse of credentials on the preliminary assault by guaranteeing sturdy passwords are used, and that customers don’t fall sufferer to credential harvesting scams – one thing taught through Safety Consciousness Coaching. If we are able to cease making it really easy for menace actors to misuse legitimate credentials, the tip end result can be far much less profitable cyber assaults.


