An up to date model of a malware loader codenamed IceXLoader is suspected of getting compromised 1000’s of private and enterprise Home windows machines internationally.
IceXLoader is a commodity malware that is offered for $118 on underground boards for a lifetime license. It is mainly employed to obtain and execute further malware on breached hosts.
This previous June, Fortinet FortiGuard Labs mentioned it uncovered a model of the trojan written within the Nim programming language with the aim of evading evaluation and detection.
“Whereas the model found in June (v3.0) appeared like a work-in-progress, we just lately noticed a more recent v3.3.3 loader which seems to be to be totally functionable and features a multi-stage supply chain,” Natalie Zargarov, cybersecurity researcher at Minerva Labs, mentioned in a report printed Tuesday.
IceXLoader is historically distributed by means of phishing campaigns, with emails containing ZIP archives functioning as a set off to deploy the malware. An infection chains have leveraged IceXLoader to ship DarkCrystal RAT and cryptocurrency miners.
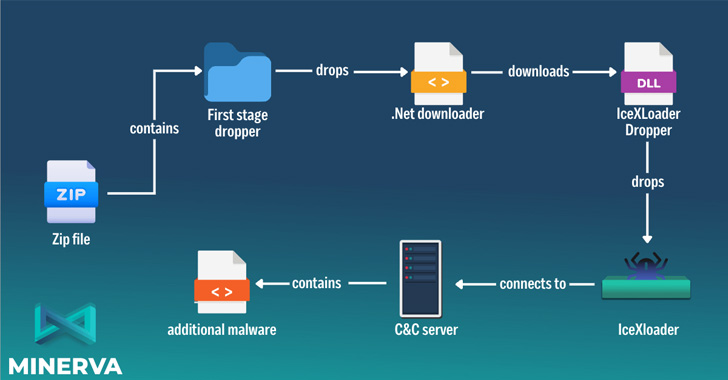
Within the assault sequence detailed by Minerva Labs, the ZIP file has been discovered to harbor a dropper, which drops a .NET-based downloader that, because the title implies, downloads a PNG picture (“Ejvffhop.png”) from a hard-coded URL.
This picture file, one other dropper, is subsequently transformed into an array of bytes, successfully permitting it to decrypt and inject IceXLoader into a brand new course of utilizing a method referred to as course of hollowing.
Model 3.3.3 of IceXLoader, like its predecessor, is written in Nim and is supplied to gather system metadata, all of which is exfiltrated to a distant attacker-controlled area, whereas awaiting additional instructions issued by the server.
The instructions embody the flexibility to restart and uninstall the malware loader and halt its execution. However its major characteristic is to obtain and execute next-stage malware on disk or filelessly in reminiscence.
Minerva Labs mentioned a SQLite database file hosted within the command-and-control (C2) server is being repeatedly up to date with details about 1000’s of victims, including it is within the means of notifying impacted firms.