Mixture of evilginx2 and GoPhish.
Credit
Earlier than I start, I wish to say that I’m under no circumstances bashing Kuba Gretzky and his work. I thank him personally for releasing evilginx2 to the general public. In truth, with out his work this work wouldn’t exist. I have to additionally thank Jordan Wright for growing/sustaining the unbelievable GoPhish toolkit.
Conditions
It is best to have a elementary understanding of methods to use GoPhish, evilginx2, and Apache2.
Disclaimer
I shall not be accountable or answerable for any misuse or illegitimate use of this software program. This software program is barely for use in approved penetration testing or pink group engagements the place the operator(s) has(ve) been given express written permission to hold out social engineering.
Why?
As a penetration tester or pink teamer, you’ll have heard of evilginx2 as a proxy man-in-the-middle framework able to bypassing two-factor/multi-factor authentication. That is engaging to us to say the least, however when making an attempt to make use of it for social engineering engagements, there are some points off the bat. I’ll spotlight the 2 fundamental issues which have been addressed with this mission, though another bugs have been fastened on this model which I’ll spotlight later.
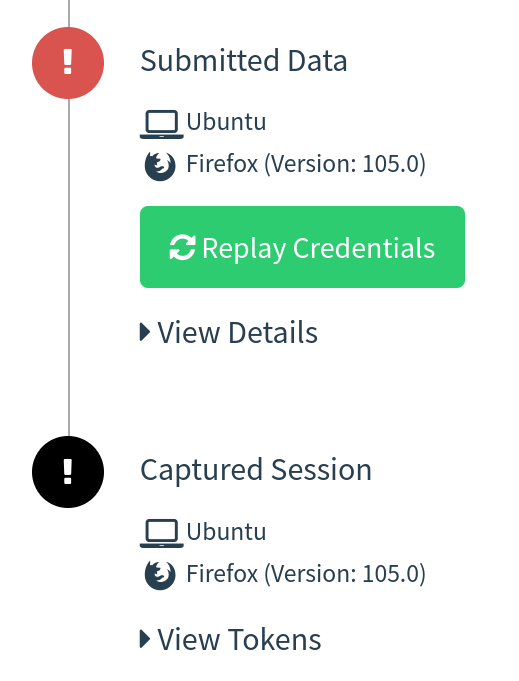
- Lack of monitoring –
evilginx2doesn’t present distinctive monitoring statistics per sufferer (e.g. opened electronic mail, clicked hyperlink, and so on.), that is problematic for shoppers who need/want/pay for these statistics when signing up for a social engineering engagement. - Session overwriting with NAT and proxying –
evilginx2bases a variety of logic off of distant IP deal with and can whitelist an IP for 10 minutes after the sufferer triggers a lure path.evilginx2will then skip creating a brand new session for the IP deal with if it triggers the lure path once more (if nonetheless within the 10 minute window). This presents points for us if our victims are behind a firewall all sharing the identical public IP deal with, as the identical session insideevilginx2will proceed to overwrite with a number of sufferer’s knowledge, resulting in missed and misplaced knowledge. This additionally presents a difficulty for our proxy setup, sincelocalhostis the one IP deal with requestingevilginx2.
Background
On this setup, GoPhish is used to ship emails and supply a dashboard for evilginx2 marketing campaign statistics, however it isn’t used for any touchdown pages. Your phishing hyperlinks despatched from GoPhish will level to an evilginx2 lure path and evilginx2 might be used for touchdown pages. This supplies the power to nonetheless bypass 2FA/MFA with evilginx2, with out shedding these valuable stats. Apache2 is just used as a proxy to the native evilginx2 server and a further hardening layer to your phishing infrastructure. Realtime marketing campaign occasion notifications have been supplied with a neighborhood websocket/http server I’ve developed and full usable JSON strings containing tokens/cookies from evilginx2 are displayed immediately within the GoPhish GUI (and feed):
Infrastructure Format
evilginx2will pay attention domestically on port8443GoPhishwill pay attention domestically on port8080and3333Apache2will pay attention on port443externally and proxy to nativeevilginx2server- Requests might be filtered at
Apache2layer based mostly on redirect guidelines and IP blacklist configuration- Redirect performance for unauthorized requests remains to be baked into
evilginx2if a request hits theevilginx2server
- Redirect performance for unauthorized requests remains to be baked into
- Requests might be filtered at
setup.sh
setup.sh has been offered to automate the wanted configurations for you. As soon as this script is run and you’ve got fed it the appropriate values, you have to be able to get began. Beneath is the setup assist (be aware that certificates setup relies on letsencrypt filenames):
replace_rid.sh
In case you ran setup.sh as soon as and already changed the default RId worth all through the mission, replace_rid.sh was created to switch the RId worth once more.
Utilization:
./replace_rid <earlier rid> <new rid>
- earlier rid - the earlier rid worth that was changed
- new rid - the brand new rid worth to switch the earlier
Instance:
./replace_rid.sh user_id client_id
E mail Marketing campaign Setup
As soon as setup.sh is run, the subsequent steps are:
- Begin
GoPhishand configure electronic mail template, electronic mail sending profile, and teams - Begin
evilginx2and configure phishlet and lure (should specify full path toGoPhishsqlite3database with-gflag) - Guarantee
Apache2server is began - Launch marketing campaign from
GoPhishand make the touchdown URL your lure path forevilginx2phishlet - PROFIT
SMS Marketing campaign Setup
A whole transforming of GoPhish was carried out with a view to present SMS marketing campaign assist with Twilio. Your new evilgophish dashboard will appear to be under:
After getting run setup.sh, the subsequent steps are:
- Configure
SMSmessage template. You’ll useTextual contentsolely when making aSMSmessage template, and you shouldn’t embody a monitoring hyperlink as it can seem within theSMSmessage. Go awayEnvelope SenderandTopicclean like under:
- Configure
SMS Sending Profile. Enter your telephone quantity fromTwilio,Account SID,Auth Token, and delay in between messages into theSMS Sending Profilesweb page:
- Import teams. The
CSVtemplate values have been saved the identical for compatibility, so maintain theCSVcolumn names the identical and place your goal telephone numbers into theE mailcolumn. Notice thatTwilioaccepts the next telephone quantity codecs, in order that they have to be in one in every of these three:
- Begin
evilginx2and configure phishlet and lure (should specify full path toGoPhishsqlite3database with-gflag) - Guarantee
Apache2server is began - Launch marketing campaign from
GoPhishand make the touchdown URL your lure path forevilginx2phishlet - PROFIT
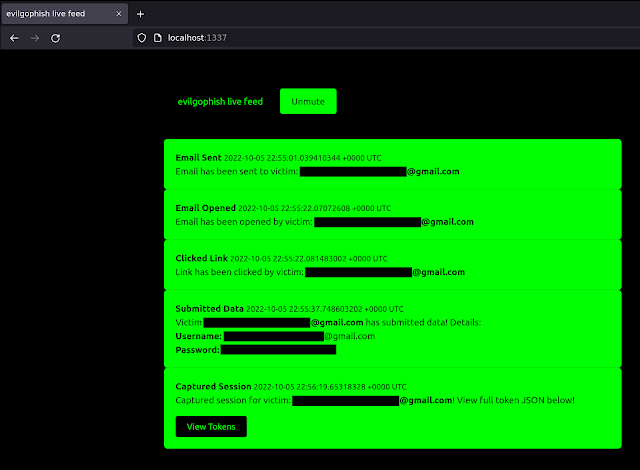
Stay Feed Setup
Realtime marketing campaign occasion notifications are dealt with by a neighborhood websocket/http server and dwell feed app. To get setup:
-
Choose
trueforfeed boolwhen operatingsetup.sh -
cdinto theevilfeedlisting and begin the app with./evilfeed -
When beginning
evilginx2, provide the-feedflag to allow the feed. For instance:
./evilginx2 -feed -g /decide/evilgophish/gophish/gophish.db
- You’ll be able to start viewing the dwell feed at:
http://localhost:1337/. The feed dashboard will appear to be under:
IMPORTANT NOTES
- The dwell feed web page hooks a websocket for occasions with
JavaScriptand also you DO NOT must refresh the web page. For those who refresh the web page, you’ll LOSE all occasions as much as that time.
Phishlets Shock
Included within the evilginx2/phishlets folder are three customized phishlets not included in evilginx2.
o3652– modified/up to date model of the uniqueo365(stolen from Optiv weblog)google– up to date from earlier examples on-line (has points, do not use in dwell campaigns)knowbe4– customized (haven’t got entry to an account for testing auth URL, works for single-factor campaigns, haven’t totally examined MFA)
A Phrase About Phishlets
I really feel just like the world has been missing some good phishlet examples these days. It could be nice if this repository might be a central repository for the newest phishlets. Ship me your phishlets at [email protected] for an opportunity to finish up in evilginx2/phishlets. For those who present high quality work, I’ll create a Phishlets Corridor of Fame and you’ll be added to it.
Adjustments To evilginx2
- All IP whitelisting performance eliminated, new proxy session is established for each new customer that triggers a lure path no matter distant IP
- Fastened challenge with phishlets not extracting credentials from
JSONrequests - Additional “dangerous” headers have been faraway from responses
- Added logic to examine if
mimesort was did not be retrieved from responses - All
Xheaders regardingevilginx2have been eliminated all through the code (to take away IOCs)
Adjustments to GoPhish
- All
Xheaders regardingGoPhishhave been eliminated all through the code (to take away IOCs) - Customized 404 web page performance, place a
.htmlfile named404.htmlintemplatesfolder (instance has been offered) - Default
ridstring in phishing URLs is chosen by the operator insetup.sh - Transparency endpoint and messages utterly eliminated
- Added
SMSMarketing campaign Assist
Changelog
See the CHANGELOG.md file for adjustments made for the reason that preliminary launch.
Points and Assist
I’m taking the identical stance as Kuba Gretzky and won’t assist creating phishlets. There are many examples of working phishlets and so that you can create your personal, in the event you open a difficulty for a phishlet it will likely be closed. I may even not take into account points together with your Apache2, DNS, or certificates setup as reputable points and they are going to be closed. Nevertheless, in the event you encounter a reputable failure/error with this system, I’ll take the difficulty critically.
Future Objectives
- Additions to IP blacklist and redirect guidelines
- Add extra phishlets
Contributing
I wish to see this mission enhance and develop over time. You probably have enchancment concepts, new redirect guidelines, new IP addresses/blocks to blacklist, phishlets, or options, please electronic mail me at: [email protected] or open a pull request.