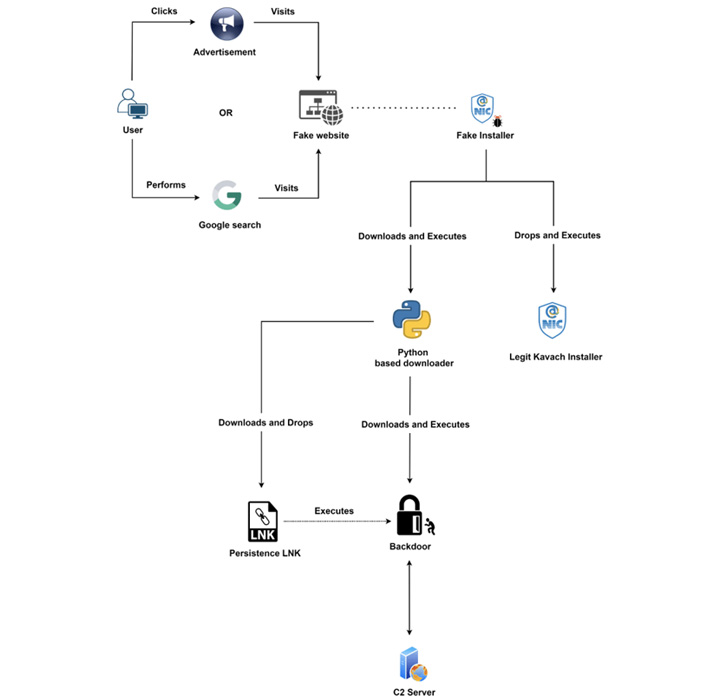
The Clear Tribe menace actor has been linked to a brand new marketing campaign geared toward Indian authorities organizations with trojanized variations of a two-factor authentication answer known as Kavach.
“This group abuses Google ads for the aim of malvertising to distribute backdoored variations of Kavach multi-authentication (MFA) functions,” Zscaler ThreatLabz researcher Sudeep Singh mentioned in a Thursday evaluation.
The cybersecurity firm mentioned the superior persistent menace group has additionally carried out low-volume credential harvesting assaults during which rogue web sites masquerading as official Indian authorities web sites have been set as much as lure unwitting customers into coming into their passwords.
Clear Tribe, additionally recognized by the monikers APT36, Operation C-Main, and Mythic Leopard, is a suspected Pakistan adversarial collective that has a historical past of putting Indian and Afghanistan entities.
The most recent assault chain isn’t the primary time the menace actor has set its sights on Kavach (which means “armor” in Hindi), a obligatory app required by customers with electronic mail addresses on the @gov.in and @nic.in domains to sign up to the e-mail service as a second layer of authentication.
Earlier this March, Cisco Talos uncovered a hacking marketing campaign that employed pretend Home windows installers for Kavach as a decoy to contaminate authorities personnel with CrimsonRAT and different artifacts.
One in every of their frequent techniques is the mimicking of respectable authorities, navy, and associated organizations to activate the killchain. The most recent marketing campaign carried out by the menace actor is not any exception.
“The menace actor registered a number of new domains internet hosting internet pages masquerading because the official Kavach app obtain portal,” Singh mentioned. “They abused the Google Advertisements’ paid search function to push the malicious domains to the highest of Google search outcomes for customers in India.”
Since Could 2022, Clear Tribe can also be mentioned to have distributed backdoored variations of the Kavach app via attacker-controlled software shops that declare to supply free software program downloads.
This web site can also be surfaced as a prime lead to Google searches, successfully performing as a gateway to redirect customers on the lookout for the app to the .NET-based fraudulent installer.
The group, starting August 2022, has additionally been noticed utilizing a beforehand undocumented information exfiltration instrument codenamed LimePad, which is designed to add recordsdata of curiosity from the contaminated host to the attacker’s server.
Zscaler mentioned it additionally recognized a site registered by Clear Tribe spoofing the login web page of the Kavach app that was solely displayed accessed from an Indian IP handle, or else redirected the customer to the house web page of India’s Nationwide Informatics Centre (NIC).
The web page, for its half, is provided to seize the credentials entered by the sufferer and ship them to a distant server for finishing up additional assaults towards government-related infrastructure.
The usage of Google advertisements and LimePad factors to the menace actor’s continued makes an attempt at evolving and refining its techniques and malware toolset.
“APT-36 continues to be one of the prevalent superior persistent menace teams targeted on focusing on customers working in Indian governmental organizations,” Singh mentioned. “Functions used internally on the Indian authorities organizations are a well-liked alternative of social engineering theme utilized by the APT-36 group.”