In case you missed it, cybersecurity agency ThreatFabric printed a report final Friday relating to its discovery of 5 malicious Google Play apps masquerading as respectable companies, together with finance monitoring and calculating taxes.
The quintet of apps fall beneath two comparatively new malware households: Vultur and Sharkbot. And sure, they’re each bit as vicious as they sound (h/t GreenBot).
The 5 apps you need to take away ASAP
Let’s begin with the malicious trio of apps that stem from the villainous Vultur household: My Funds Tracker: Finances, C, Zetter Authenticator, and Get better Audio, Pictures & Movies. The three apps attracted 1,000+, 10,000+ and 100,000+ downloads respectively.
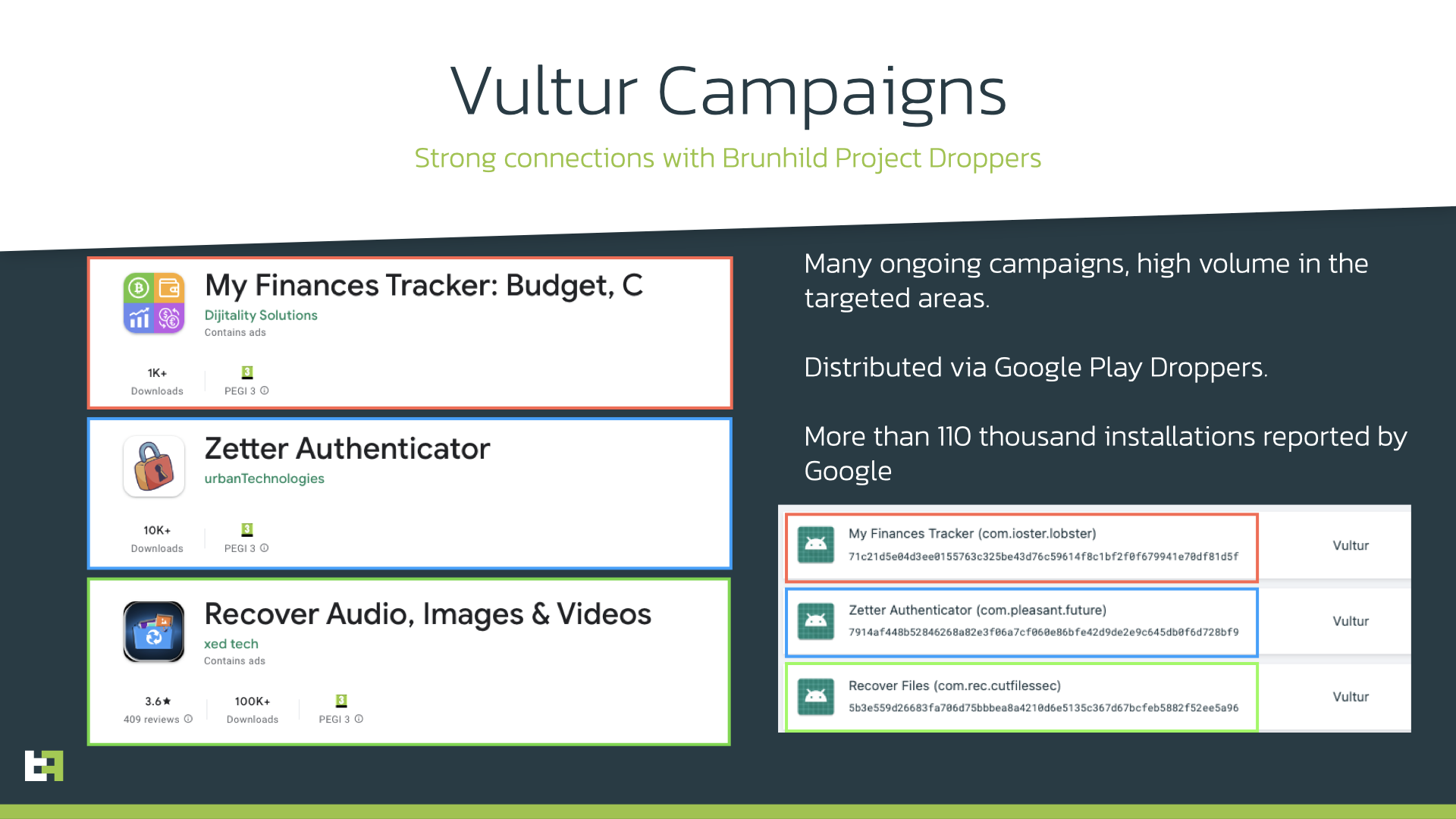
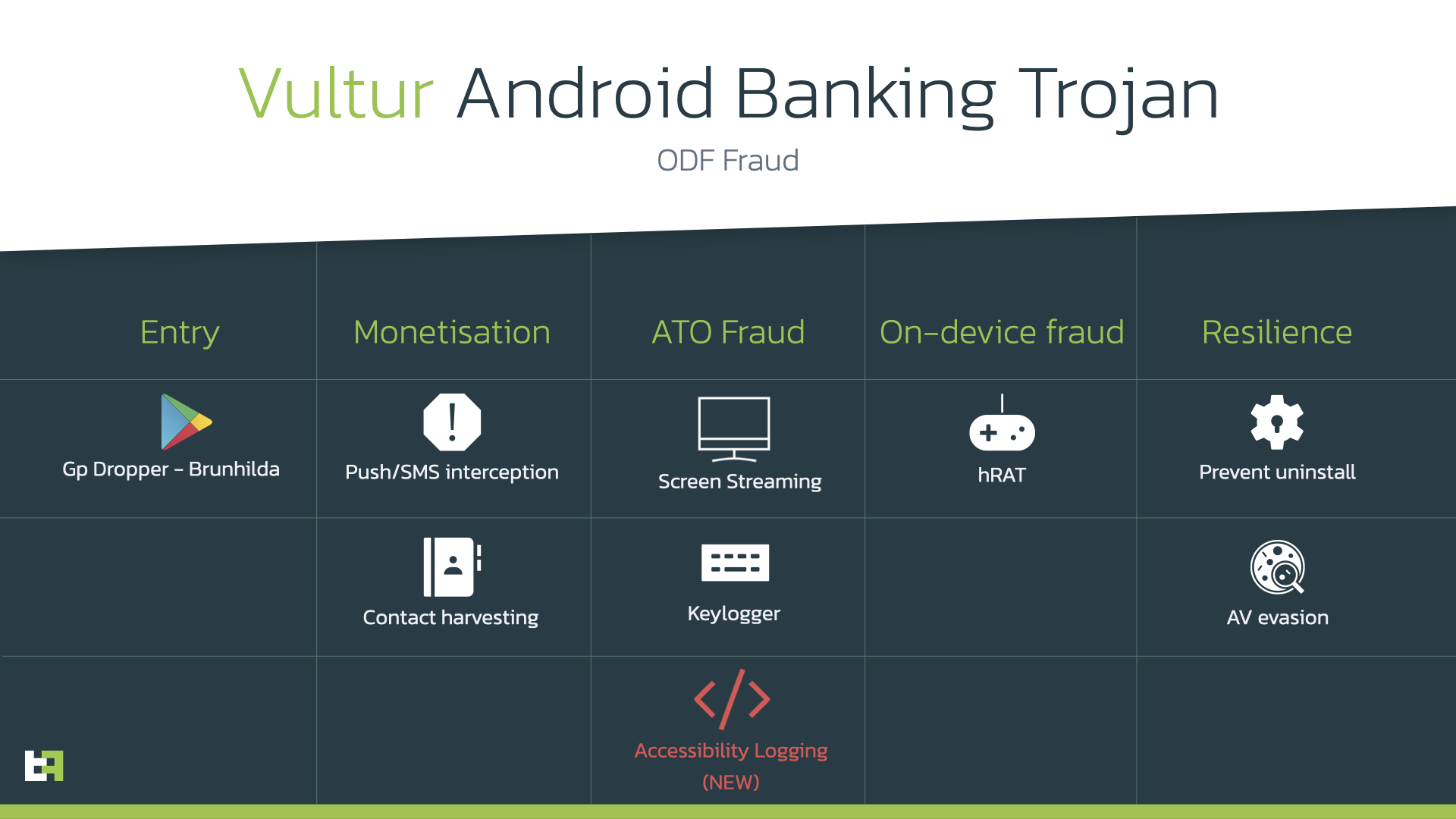
You might be questioning, “What, precisely, is Vultur malware?” In keeping with the cybersecurity report, Vultur was first found in July 2021. It is an Android banking trojan that steals personally identifiable data (PII) by recording your display screen.
“It is usually in a position to create a distant session on the gadget utilizing VNC know-how to carry out actions on the sufferer’s gadget, successfully resulting in On-System Fraud (ODF),” the ThreatFabric report stated.
Apparently, ThreatFabric found a brand new, regarding modus operandi with the three aforementioned Vultur-injected Google Play apps. Not solely does it depend on display screen streaming to steal data from unwitting victims, but it surely additionally makes use of accessibility logging. In different phrases, the trio of apps can observe your gestures and faucets to spy in your information.
If that wasn’t creepy sufficient, ThreatFabric additionally unveiled its findings relating to two apps beneath the Sharkbot malware household: Codice Fiscale 2022 and File Supervisor, Lite. The previous app targets Italian customers whereas the latter targets Italian and UK quarries. Nonetheless, ThreatFabric warns that Android customers should not get too snug.
“The payload delivered [from Codice Fiscale 2022 and File Manager, Lite] nonetheless has banks from Italy, UK, Germany, Spain, Poland, Austria, US, and Australia in its goal checklist,” the report stated.
What’s fearsome about this new Sharkbot iteration is that, in contrast to earlier campaigns, this one slips beneath the radar extra simply as a result of it doesn’t immediate customers to just accept suspicious, fishy permissions.
When Sharkbot will get its fins on a tool, it will probably steal customers’ banking account credentials and even slip by means of multi-factor authentication boundaries. Regardless of Google’s coverage and safety adjustments, harmful malware nonetheless finds a method to wiggle its means into the Play Retailer.
“Google Play nonetheless stays essentially the most ‘inexpensive’ and scalable means of reaching victims for many of the actors of various degree,” ThreatFabric concluded.


