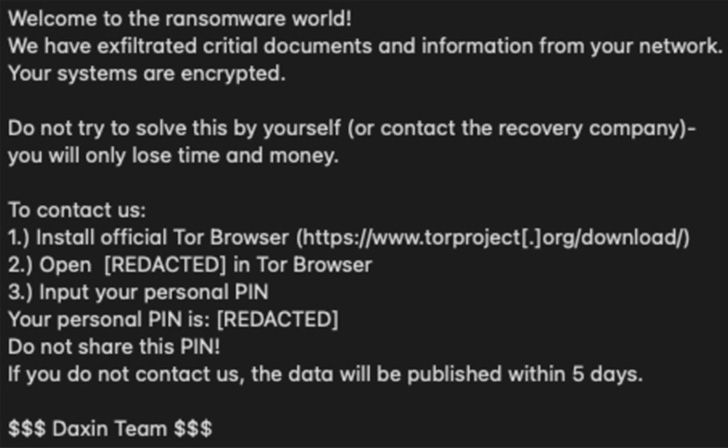
U.S. cybersecurity and intelligence businesses have revealed a joint advisory warning of assaults perpetrated by a cybercrime gang referred to as the Daixin Staff primarily focusing on the healthcare sector within the nation.
“The Daixin Staff is a ransomware and knowledge extortion group that has focused the HPH Sector with ransomware and knowledge extortion operations since at the very least June 2022,” the businesses mentioned.
The alert was revealed Friday by the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Safety Company (CISA), and the Division of Well being and Human Providers (HHS).
Over the previous 4 months, the group has been linked to a number of ransomware incidents within the Healthcare and Public Well being (HPH) sector, encrypting servers associated to digital well being information, diagnostics, imaging, and intranet providers.
It is also mentioned to have exfiltrated private identifiable info (PII) and affected person well being info (PHI) as a part of a double extortion scheme to safe ransoms from victims.
A type of assaults was geared toward OakBend Medical Heart on September 1, 2022, with the group claiming to have siphoned roughly 3.5GB of information, together with over a million information with affected person and worker info.
It additionally revealed a pattern containing 2,000 affected person information on its knowledge leak website, which included names, genders, dates of delivery, Social Safety numbers, addresses, and different appointment particulars, based on DataBreaches.web.
On October 11, 2022, it notified its clients of emails despatched by “third-parties” relating to the cyber assault, stating it is straight informing affected sufferers, along with providing free credit score monitoring providers for 18 months.
Per the brand new alert, preliminary entry to focused networks is achieved by way of digital personal community (VPN) servers, usually profiting from unpatched safety flaws and compromised credentials obtained through phishing emails.
Upon gaining a foothold, the Daixin Staff has been noticed shifting laterally by making use of distant desktop protocol (RDP) and safe shell (SSH), adopted by gaining elevated privileges utilizing methods like credential dumping.
“The actors have leveraged privileged accounts to achieve entry to VMware vCenter Server and reset account passwords for ESXi servers within the surroundings,” the U.S. authorities mentioned. “The actors have then used SSH to hook up with accessible ESXi servers and deploy ransomware on these servers.”
What’s extra, the Daixin Staff’s ransomware is predicated on one other pressure referred to as Babuk that was leaked in September 2021, and has been used as a basis for a lot of file-encrypting malware households similar to Rook, Night time Sky, Pandora, and Cheerscrypt.
As mitigations, it is really useful that organizations apply the newest software program updates, implement multi-factor authentication, implement community segmentation, and keep periodic offline backups.