AWS Config gives an in depth view of the configuration of AWS assets in your AWS account. This contains how assets are associated to one another and the way assets have been organized prior to now, so you may see how their configurations and relationships change over time.
- If you allow AWS Config, it first identifies the supported AWS assets in your account and creates a configuration merchandise for every useful resource.
- AWS Config additionally creates a configuration merchandise when the useful resource configuration modifications and retains a historic report of the useful resource configuration merchandise after the configuration writer runs.
- By default, AWS Config creates a configuration merchandise for every supported useful resource in a area.
- If you do not need AWS Config to create configuration objects for all supported assets, you may specify the varieties of assets you wish to observe.
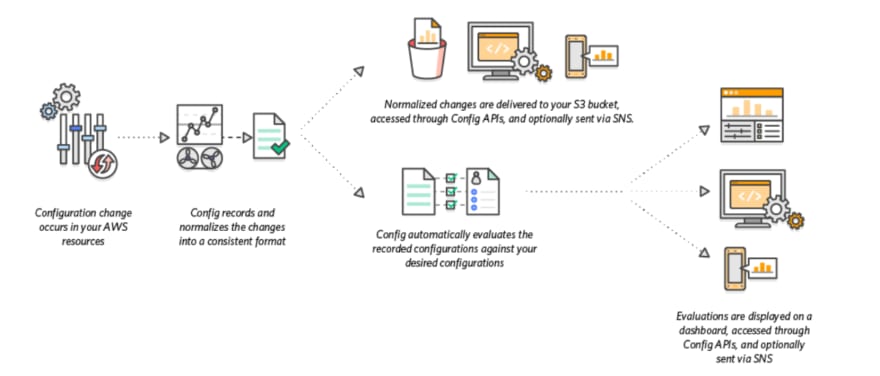
AWS Config tracks all useful resource modifications by calling the Describe or Checklist API requires every useful resource in your account. The service makes use of the identical API name to retrieve configuration particulars for all associated assets.
For instance,
In case you delete an egress rule from a VPC safety group, AWS Config makes an API describe name on the safety group.
AWS Config then makes an API name to explain all cases related to the safety group. Up to date configurations for safety teams (assets) and every occasion (associated assets) are recorded as configuration objects and delivered to the Amazon Easy Storage Service folder within the configuration movement.
AWS Config additionally tracks configuration modifications not applied within the API. AWS Config periodically checks the useful resource configuration and creates configuration objects for modified configurations.
In case you use AWS Config guidelines, AWS Config constantly evaluates the configuration of your AWS assets for the specified settings. Relying on the rule, AWS Config evaluates assets periodically or in response to configuration modifications.
Every rule is related to an AWS Lambda operate that comprises the rule’s analysis logic. When AWS Config evaluates a useful resource, it invokes the rule’s AWS Lambda operate. This operate returns the match standing of the evaluated useful resource.
If a useful resource violates the situations of a rule, AWS Config marks the useful resource and the rule as non-compliant. When the compliance standing of useful resource modifications, AWS Config sends a notification to an Amazon SNS matter.
Kindly watch the beneath video to know extra about AWS Config.
AWS Config is a service that lets you view, monitor, and consider the configuration of your AWS assets. Config constantly screens and logs AWS supply configurations, which might automate the analysis of logged configurations in opposition to desired configurations.
Use AWS Config to find out which elastic community interfaces or ENIs will not be hooked up to assets in your surroundings, after which use System Supervisor to revive assets marked as non-compliant.
- AWS Config lets you outline guidelines for evaluating the provisioning and configuration of AWS assets. These guidelines may be supplied with bundled compliance remediation actions that may be applied on the particular person account or group degree.
- Preliminary configuration or configuration modifications that deviate from the foundations mechanically set off Amazon Easy Notification Service (SNS) notifications and Amazon CloudWatch occasions so you may keep knowledgeable.
Earlier than you can begin utilizing the configuration, you need to allow the configuration recording and configure a supply channel.
Kindly watch the beneath video to get began with AWS Config guidelines and remediation.
On this article, you created plenty of unattached elastic IP addresses and added an AWS configuration. You then applied a rule to examine for unattached EIPs and used Methods Supervisor Automation runbooks to repair the non-compliant assets.
Gratitude for perusing my article until the top. I hope you realized one thing distinctive right this moment. In case you loved this text then please share it together with your buddies and you probably have ideas or ideas to share with me then please write within the remark field.
Comply with me and share your ideas,
GitHub
LinkedIn
Twitter
The above weblog is submitted below ‘Devtron Hacktoberfest 2022’ carried out by Devtron. Try their Github repo and provides it a star