Microsoft has revised its mitigation measures for the newly disclosed and actively exploited zero-day flaws in Change Server after it was discovered that they may very well be trivially bypassed.
The 2 vulnerabilities, tracked as CVE-2022-41040 and CVE-2022-41082, have been codenamed ProxyNotShell resulting from similarities to a different set of flaws known as ProxyShell, which the tech large resolved final yr.
In-the-wild assaults abusing the shortcomings have chained the 2 flaws to realize distant code execution on compromised servers with elevated privileges, resulting in the deployment of net shells.
The Home windows maker, which is but to launch a repair for the bugs, has acknowledged {that a} single state-sponsored risk actor might have been weaponizing the failings since August 2022 in restricted focused assaults.
Within the meantime, the corporate has made accessible short-term workarounds to cut back the danger of exploitation by proscribing identified assault patterns by a rule within the IIS Supervisor.
Nevertheless, in response to safety researcher Jang (@testanull), the URL sample may be simply circumvented, with senior vulnerability analyst Will Dormann noting that the block mitigations are “unnecessarily exact, and due to this fact inadequate.”
Microsoft has since revised the URL Rewrite rule (additionally accessible as a standalone PowerShell script) to take this into consideration –
- Open IIS Supervisor
- Choose Default Internet Web site
- Within the Characteristic View, click on URL Rewrite
- Within the Actions pane on the right-hand facet, click on Add Rule(s)…
- Choose Request Blocking and click on OK
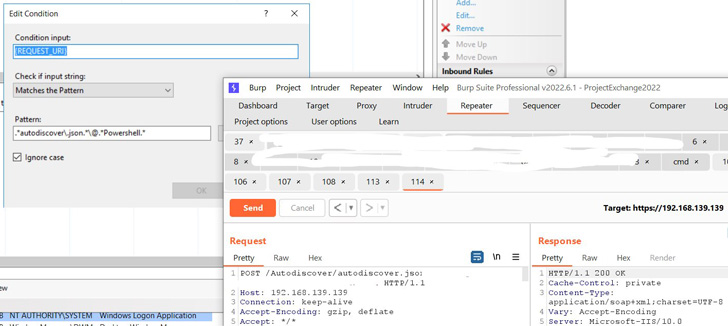
- Add the string “.*autodiscover.json.*Powershell.*” (excluding quotes)
- Choose Common Expression below Utilizing
- Choose Abort Request below How one can block after which click on OK
- Develop the rule and choose the rule with the sample: .*autodiscover.json.*Powershell.* and click on Edit below Situations
- Change the Situation enter from {URL} to {REQUEST_URI}
It isn’t instantly clear when Microsoft plans to push a patch for the 2 vulnerabilities, nevertheless it’s potential that they may very well be shipped as a part of Patch Tuesday updates subsequent week on October 11, 2022.