The 2 vulnerabilities in query are listed within the Nationwide Vulnerability Database (NVD) as CVE-2022-41040 and CVE-2022-41082 and each bear excessive severity scores of 8.8 out of 10. The vulnerabilities additionally seem within the Cybersecurity & Infrastructure Safety Company’s (CISA) Recognized Exploited Vulnerabilities Catalog, as a Chinese language risk actor is leveraging these two vulnerabilities together to achieve distant entry to Trade servers. The attacker chains the 2 vulnerabilities collectively, utilizing the primary vulnerability to carry out privilege escalation, which permits the attacker to then exploit the second vulnerability to conduct distant code execution. From there, the attacker can assortment data, create persistent backdoors, and entry different servers on the native community.
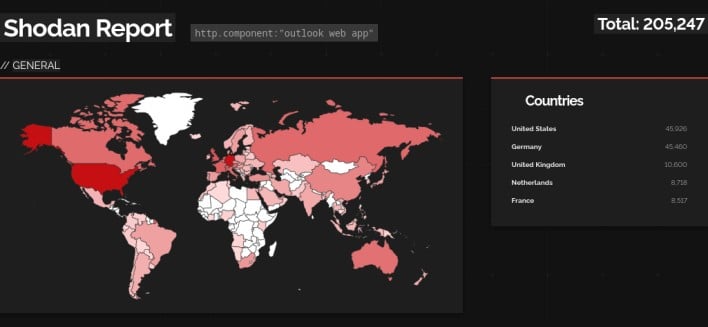
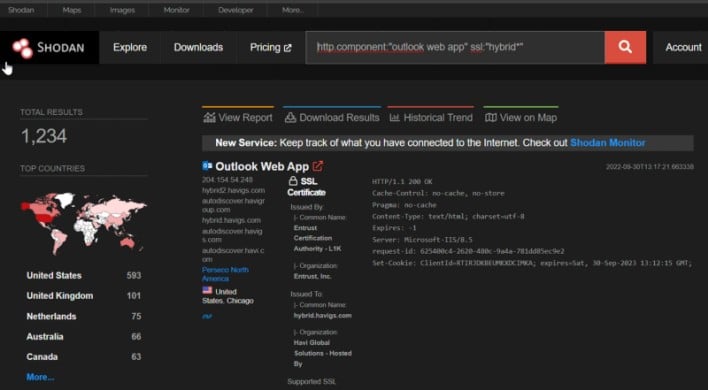
The assault begins with the next request: autodiscover/autodiscover.json?@evil.com/<Trade-backend-endpoint>&E-mail=autodiscover/autodiscover.jsonpercent3f@evil.com. This request seems an identical to the one used within the 2021 ProxyShell assault. Nonetheless, this new assault requires authentication on the a part of the attacker, prompting Kevin Beaumont to call the assault ProxyNotShell. Trade servers with the Outlook Internet App uncovered to the open web are weak to this assault, and a fast search on Shodan exhibits that over 200,000 Trade servers are presently configured this fashion. Trade Server admins can block this particular assault sample by performing the next steps, courtesy of Microsoft:
- Open IIS Supervisor.
- Choose Default Internet Website.
- Within the Characteristic View, click on URL Rewrite.
- Within the Actions pane on the right-hand aspect, click on Add Rule(s)…
- Choose Request Blocking and click on OK.
- Add the string “.*autodiscover.json.*@.*Powershell.*” (excluding quotes).
- Choose Common Expression beneath Utilizing.
- Choose Abort Request beneath Find out how to block after which click on OK.
- Develop the rule and choose the rule with the sample .*autodiscover.json.*@.*Powershell.* and click on Edit beneath Situations.
- Change the Situation enter from {URL} to {REQUEST_URI}
Lower than per week after Microsoft printed its weblog submit advising organizations to use this mitigation, cybersecurity researcher Jang posted a tweet exhibiting {that a} slight modification to the request featured within the ProxyNotShell assault bypasses the mitigation. Thankfully, a modification to the mitigation seems to dam the bypass. Moderately than making a block rule with the string .*autodiscover.json.*@.*Powershell.*, directors can broaden the effectiveness of this rule by as an alternative utilizing the string .*autodiscover.json.*Powershell.*.