A beforehand undocumented risk actor of unknown origin has been linked to assaults focusing on telecom, web service suppliers, and universities throughout a number of nations within the Center East and Africa.
“The operators are extremely conscious of operations safety, managing rigorously segmented infrastructure per sufferer, and shortly deploying intricate countermeasures within the presence of safety options,” researchers from SentinelOne stated in a brand new report.
The cybersecurity agency codenamed the group Metador in reference to a string “I’m meta” in certainly one of their malware samples and due to Spanish-language responses from the command-and-control (C2) servers.
The risk actor is alleged to have primarily centered on the event of cross-platform malware in its pursuit of espionage goals. Different hallmarks of the marketing campaign are the restricted variety of intrusions and long-term entry to targets.
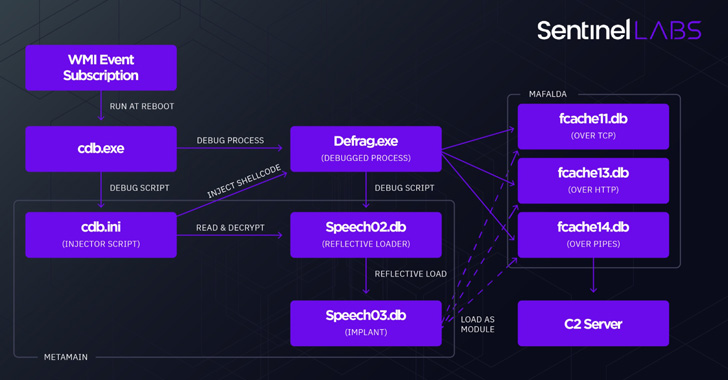
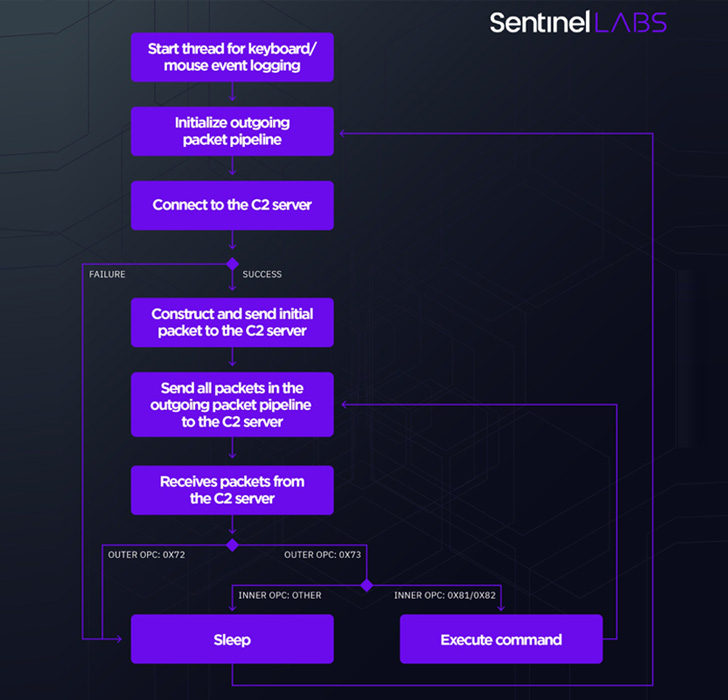
This consists of two completely different Home windows malware platforms referred to as metaMain and Mafalda which might be expressly engineered to function in-memory and elude detection. metaMain additionally acts as a conduit to deploy Mafalda, a versatile interactive implant supporting 67 instructions.
metaMain, for its half, is feature-rich by itself, enabling the adversary to take care of long-term entry, log keystrokes, obtain and add arbitrary recordsdata, and execute shellcode.
In an indication that Mafalda is being actively maintained by its builders, the malware gained assist for 13 new instructions between two variants compiled in April and December 2021, including choices for credential theft, community reconnaissance, and file system manipulation.
Assault chains have additional concerned an unknown Linux malware that is employed to assemble info from the compromised setting and funnel it again to Mafalda. The entry vector used to facilitate the intrusions is unknown as but.
What’s extra, references within the inside command’s documentation for Mafalda counsel a transparent separation of duties between the builders and operators. In the end although, Metador’s attribution stays a “garbled thriller.”
“Furthermore, the technical complexity of the malware and its energetic growth counsel a well-resourced group capable of purchase, preserve and prolong a number of frameworks,” researchers Juan Andres Guerrero-Saade, Amitai Ben Shushan Ehrlich, and Aleksandar Milenkoski famous.