The U.S. Cybersecurity and Infrastructure Safety Company (CISA) on Tuesday launched an industrial management techniques (ICS) advisory warning of seven safety flaws in Dataprobe’s iBoot-PDU energy distribution unit product, principally utilized in industrial environments and information facilities.
“Profitable exploitation of those vulnerabilities might result in unauthenticated distant code execution on the Dataprobe iBoot-PDU machine,” the company stated in a discover.
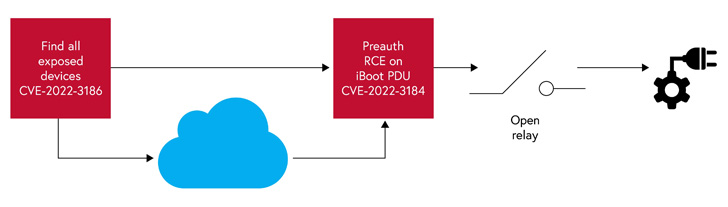
Credited with disclosing the issues is industrial cybersecurity agency Claroty, which stated the weaknesses might be remotely triggered “both by means of a direct net connection to the machine or by way of the cloud.”
iBoot-PDU is an influence distribution unit (PDU) that gives customers with real-time monitoring capabilities and complex alerting mechanisms by way of an online interface in order to regulate the ability provide to units and different gear in an OT surroundings.
The vulnerabilities assume new significance when bearing in mind the truth that no fewer than 2,600 PDUs are accessible on the web, with Dataprobe units accounting for practically a 3rd of these uncovered, in line with a 2021 report from assault floor administration platform Censys.
Claroty’s evaluation of the PDU firmware exhibits that the product is crippled by points starting from command injection to path traversal flaws, exposing prospects to extreme safety dangers –
- CVE-2022-3183 (CVSS rating: 9.8) – A command injection vulnerability stemming from a scarcity of sanitization of consumer enter
- CVE-2022-3184 (CVSS rating: 9.8) – A path traversal vulnerability that permits entry to an unauthenticated PHP web page, which might be abused to insert malicious code
Profitable distant exploitation of the issues “places an attacker inside arm’s size of disrupting crucial companies by slicing off electrical energy to the machine and subsequently, something plugged into it,” Clarory researcher Uri Katz stated.
The opposite 5 uncovered vulnerabilities (from CVE-2022-3185 by means of CVE-2022-3189) might be weaponized by a foul actor to entry the machine’s major administration web page from the cloud and even trick the server to hook up with arbitrary inner or exterior techniques (aka SSRF), doubtlessly leaking delicate info.
“Even an innocuous energy distribution unit remotely managed over the web or by way of a cloud-based administration platform can present a decided attacker to focus on the community, or with a solution to disrupt important companies by slicing energy to units plugged right into a PDU,” Katz stated.
Claroty additional disclosed that it discovered a solution to enumerate cloud-connected iBoot PDU units by exploiting a mix of a sound cookie and the machine ID (a sequential numeric worth that may be trivially guessed), thereby widening the obtainable assault floor to all linked units.
Customers of Dataprobe iBoot-PDU are advisable to improve to the newest firmware model (1.42.06162022) in addition to disable SNMP, Telnet, and HTTP, if not in use, as a mitigation in opposition to a few of these vulnerabilities.