ACM.56 How I’d abuse your Lambda operate on a pentest if you happen to don’t correctly safe your inputs
This can be a continuation of my sequence of posts on Automating Cybersecurity Metrics.
One of many issues we’re gong to wish to change within the Lambda operate we simply created earlier is the power to move in a parameter with the batch job title. Let’s take a look at how we are able to try this and what kind of safety issues may ensue if we aren’t cautious.
Create a New Check Occasion to Move in a Batch Job Identify
When you recall whereas testing our Lambda operate within the console, we used the default take a look at occasion configuration which was spending some values within the request to the Lambda operate.
Return to the take a look at Lambda we created earlier (the one we created manually, not the one we deployed with CloudFormation) or create a brand new one if you happen to already deleted it.
Click on on Check > Configure take a look at occasion.

The defaults are some take a look at values:
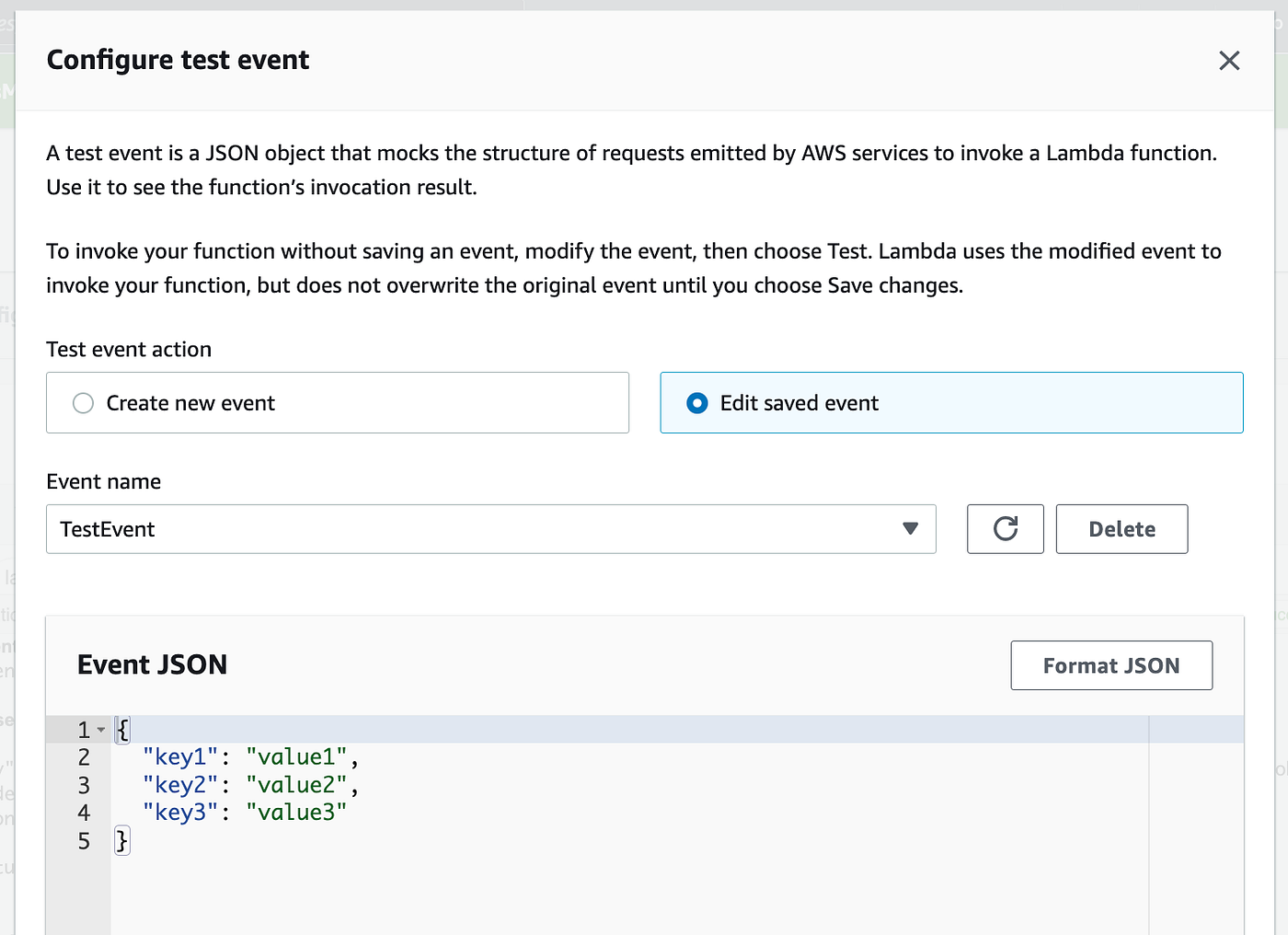
Click on Create New Occasion. Identify it. Change the take a look at worth as follows:

Click on Save. Click on Check once more. Now you’ll be able to see a brand new take a look at and that it’s lively.

Alter the Lambda operate code as follows:

Discover that two variables are handed into our lambda_handler: occasion and context. I wish to print these out to see what they include. I simply recommended out the sooner code as a result of I’m going to make use of it once more later.
Click on Deploy. Then Check.

The Occasion accommodates the title and worth we added to our take a look at occasion and the context has some metadata in regards to the Lambda operate.

Alter the code to print out the BatchJobName contained within the occasion:

Deploy and Check:

Set the worth of the batch job title to a variable and return it within the response.
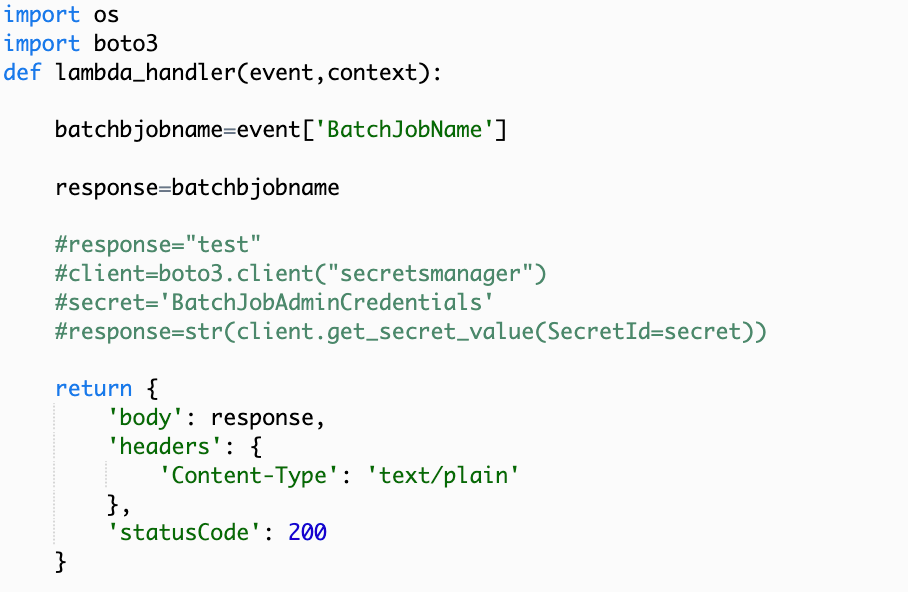
Deploy. Check.

You have got basically created an API that takes a batch job title as enter and returns a batch job title as output.
Reflection and Cross-Web site Scripting (XSS)
Returning a worth to a consumer precisely because it was entered is known as reflection, and it’s not an excellent ideally suited to permit folks to insert no matter they need into your utility and return it with out checking that it doesn’t include a malicious worth. What might I do with this as a pentester or an attacker? Many, many issues. Right here’s one instance.
Create a brand new file in your native laptop computer named take a look at.html.
Enter this code into the file and reserve it:
<script>alert(1)</script>
Double click on on the file and you will notice a popup field like this:

You’ve simply written executable code that routinely runs in a browser. No large deal proper?
Return to your take a look at occasion and enter this worth:

Check.

As you’ll be able to see, we’ve simply allowed customers to insert executable code into our Lambda operate. However we didn’t get a popup right here so no large deal proper? The code shouldn’t be executing. That’s as a result of AWS has taken steps to deal with the values handed into Lambda features within the AWS console securely.
The place may this be an issue? Learn on…
Completely different strategies for invoking Lambda Features
Check out the AWS documentation for the alternative ways we are able to invoke a Lambda operate. One is a Curl assertion.
One choice could be to make use of a curl assertion which is a solution to request an online web page and get the outcomes.

To request an online web page with curl we’d like a URL. Let’s create one for our Lambda operate.
Configure a URL to your Lambda Perform
Configure a Perform URL.

Select None for Auth kind and click on Save.

Copy the URL to your operate:

Alter your take a look at file to invoke the operate with the parameter
Edit the take a look at file we created. Enter this worth:

Now double click on in your take a look at file once more. Bingo.

I, as a tester, might move malicious code into your Lambda operate that will get executed in a Person’s browser. If this exists in your utility there are such a lot of methods I can abuse it. I’d have the ability to steal cookies or information belonging to customers on internet pages they’re visiting or trigger them to take actions on pages — mainly something that you are able to do with JavaScript in a browser if you happen to don’t have correct safety controls in your internet pages.
If you wish to know extra about safe programming I wrote about an important issues it’s essential to know right here and shall be including extra quickly as I’m engaged on a brand new e-book on safe coding primarily based on this sequence:
From there you’ll be able to dig into the main points that are many, beginning with this documentation from OWASP on methods to forestall injection assaults:
If you wish to see in case your internet utility has probably the most very primary safety flaws, enter this worth into each textual content field:
<script>alert(1)</script>
When you discover that any textual content field pops up an alert field as proven on this publish, please cease what you might be doing proper now and speak to me on LinkedIn for a penetration take a look at.
That is probably the most very primary type of testing for a cross-site scripting flaw and if this exists in your internet utility seemingly you have got different points which can be straightforward for an attacker to use.
Inner internet functions too!
Be aware that even when the applying requires somebody to login this may be abused by a malicious consumer or somebody who steals the credentials or methods the consumer into clicking a hyperlink. I wrote about how attackers used vendor credentials within the Goal Breach and no, they didn’t break into an “HVAC system.” They used vendor credentials and flaws within the system that the seller might log into.
After I carry out a penetration take a look at I get inner credentials from prospects to make sure that no solely the Web-facing content material is safe however all of the functions behind login pages.
A cross-site scripting flaw on AWS
If you wish to see one other instance of a cross-site scripting flaw I discovered on an AWS utility penetration take a look at — which can have been in AWS code — try my presentation from RSA 2020. It’s the primary presentation hyperlink on this web page. I’ve another movies and slides on cloud penetration testing in there as properly:
Earlier than I gave my presentation the shopper informed me the bug I discovered was in their very own code. Even so, I reported it to AWS however didn’t observe up on it as a result of I’m actually busy. AWS doesn’t have a bug bounty and I must put my time principally into paid work, aside from what I write on this weblog to assist folks out. It’s not like AWS can’t afford a bug bounty. #awswishlist.
However they don’t supply one for no matter motive, so I don’t spend a whole lot of time on the bugs I discover. I do report them to safety if they’re blatant. AWS replied that this was a bug in a “beta service” however past that every one I do know is that there was a bug that allowed me to carry out cross web site scripting utilizing a customized fuzzer I wrote to check APIs and acquire authentication credentials from an utility. I informed the shopper they need to work with AWS to resolve the issue as a result of if it was in AWS code that was their finest recourse.
After I carry out penetration checks I inform prospects what the bugs, how they’ll have an effect on the shopper, and methods to repair them. Troubleshooting with a third-party vendor could be out of scope and I didn’t assume paying me extra would resolve the issue any quicker if it existed in AWS code. I’m not one for over-charging prospects for providers they don’t want, however I’m completely satisfied to assist extra if requested and wanted.
XSS is among the most typical vulnerabilities I discover and it might probably do a whole lot of harm. Be sure to correctly validate any and all values {that a} shopper can manipulate in an online request. And I imply any. I’ve discovered cross web site scripting in shade pickers, http headers, and virtually any a part of an online web page you’ll be able to assume off. I’ve additionally been in a position to submit values to to internet functions that carry out cross-site scripting assaults later (often known as a saved XSS vulnerability) that direct customers to an online web page of my selecting.
Now that I’ve proven you methods to move parameters to a Lambda operate and what to not do, let’s see how we are able to use this to move in a batch job title and use it in our system structure. Observe for updates.
Teri Radichel
When you appreciated this story please clap and observe:
Medium: Teri Radichel or Electronic mail Record: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, displays, and podcasts


