A state-sponsored superior persistent menace (APT) actor newly christened APT42 (previously UNC788) has been attributed to over 30 confirmed espionage assaults in opposition to people and organizations of strategic curiosity to the Iranian authorities not less than since 2015.
Cybersecurity agency Mandiant stated the group operates because the intelligence gathering arm of Iran’s Islamic Revolutionary Guard Corps (IRGC), to not point out shares partial overlaps with one other cluster known as APT35, which is also referred to as Charming Kitten, Cobalt Phantasm, ITG18, Phosphorus, TA453, and Yellow Garuda.
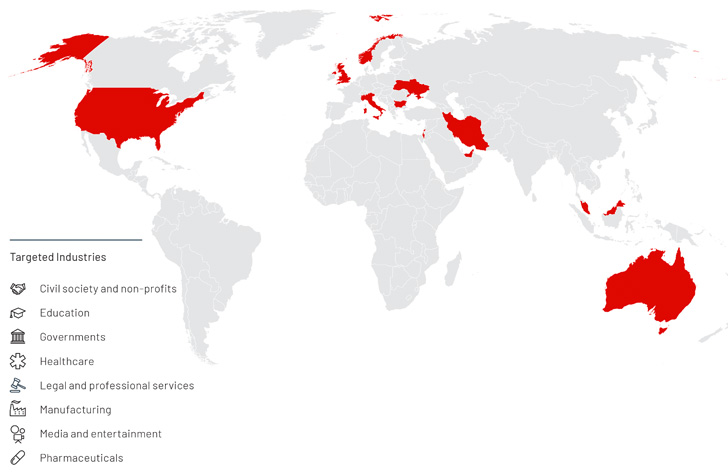
APT42 has exhibited a propensity to strike numerous industries equivalent to non-profits, schooling, governments, healthcare, authorized, manufacturing, media, and prescribed drugs spanning not less than 14 nations, together with in Australia, Europe, the Center East, and the U.S.
Intrusions aimed on the pharmaceutical sector are additionally notable for the truth that they commenced on the onset of the COVID-19 pandemic in March 2020, indicating the menace actor’s potential to swiftly modify its campaigns with the intention to meet its operational priorities.
“APT42 makes use of extremely focused spear-phishing and social engineering strategies designed to construct belief and rapport with their victims with the intention to entry their private or company electronic mail accounts or to put in Android malware on their cellular units,” Mandiant stated in a report.
The purpose is to take advantage of the fraudulent belief relationships to steal credentials, enabling the menace actor to leverage the entry to conduct follow-on compromises of company networks to assemble delicate information and use the breached accounts to phish extra victims.
Assault chains contain a mixture of extremely focused spear-phishing messages aimed toward people and organizations of strategic curiosity to Iran. They’re additionally conceived with the intent to construct belief with former authorities officers, journalists, policymakers, and the Iranian diaspora overseas in hopes of distributing malware.
Exterior of utilizing hacked electronic mail accounts related to assume tanks to focus on researchers and different educational organizations, APT42 is usually recognized to impersonate journalists and different professionals to interact with the victims for a number of days and even weeks earlier than sending a malicious hyperlink.
In a single assault noticed in Might 2017, the group focused members of an Iranian opposition group working from Europe and North America with electronic mail messages that contained hyperlinks to rogue Google Books pages, which redirected victims to sign-in pages designed to siphon credentials and two-factor authentication codes.
Surveillance operations contain the distribution of Android malware equivalent to VINETHORN and PINEFLOWER through textual content messages which are able to recording audio and cellphone calls, extracting multimedia content material and SMSes, and monitoring geolocations. A VINETHORN payload noticed between April and October 2021 masqueraded as a VPN app known as SaferVPN.
“The usage of Android malware to focus on people of curiosity to the Iranian authorities gives APT42 with a productive methodology of acquiring delicate data on targets, together with motion, contacts, and private data,” the researchers famous.
The group can be stated to make use of a raft of light-weight Home windows malware now and again – a PowerShell toehold backdoor named TAMECAT, a VBA-based macro dropper dubbed TABBYCAT, and a reverse shell macro generally known as VBREVSHELL – to enhance their credential harvesting and espionage actions.
APT42’s hyperlinks to APT35 stems from hyperlinks to an uncategorized menace cluster tracked as UNC2448, which Microsoft (DEV-0270) and Secureworks (Cobalt Mirage) disclosed as a Phosphorus subgroup finishing up ransomware assaults for monetary achieve utilizing BitLocker.
Mandiant’s evaluation additional lends credence to Microsoft’s findings that DEV-0270/UNC2448 is operated by a entrance firm that makes use of two public aliases, particularly Secnerd and Lifeweb, each of that are related to Najee Expertise Hooshmand.
That having stated, it is suspected the 2 adversarial collectives, regardless of their affiliation with IRGC, originate from disparate missions based mostly on variations in concentrating on patterns and the ways employed.
A key level of distinction is that whereas APT35 is oriented in the direction of long-term, resource-intensive operations concentrating on totally different business verticals within the U.S. and the Center East, APT42’s actions deal with people and entities for “home politics, overseas coverage, and regime stability functions.”
“The group has displayed its potential to quickly alter its operational focus as Iran’s priorities change over time with evolving home and geopolitical circumstances,” the researchers stated.