A zero-day flaw in a WordPress plugin known as BackupBuddy is being actively exploited, WordPress safety firm Wordfence has disclosed.
“This vulnerability makes it attainable for unauthenticated customers to obtain arbitrary recordsdata from the affected web site which might embrace delicate info,” it stated.
BackupBuddy permits customers to again up their complete WordPress set up from throughout the dashboard, together with theme recordsdata, pages, posts, widgets, customers, and media recordsdata, amongst others.
The plugin is estimated to have round 140,000 lively installations, with the flaw (CVE-2022-31474, CVSS rating: 7.5) affecting variations 8.5.8.0 to eight.7.4.1. It has been addressed in model 8.7.5 launched on September 2, 2022.
The problem is rooted within the operate known as “Native Listing Copy” that is designed to retailer a neighborhood copy of the backups. Based on Wordfence, the vulnerability is the results of the insecure implementation, which allows an unauthenticated menace actor to obtain any arbitrary file on the server.
Further particulars concerning the flaw have been withheld in gentle of lively in-the-wild abuse and its ease of exploitation.
“This vulnerability might enable an attacker to view the contents of any file in your server that may be learn by your WordPress set up,” the plugin’s developer, iThemes, stated. “This might embrace the WordPress wp-config.php file and, relying in your server setup, delicate recordsdata like /and many others/passwd.”
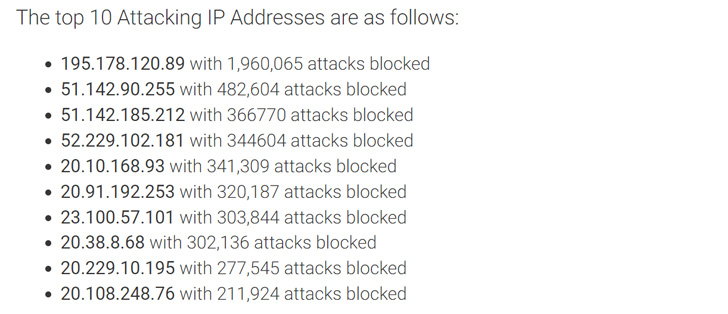
Wordfence famous that the focusing on of CVE-2022-31474 commenced on August 26, 2022, and that it has blocked almost 5 million assaults at the moment interval. A lot of the intrusions have tried to learn the under recordsdata –
- /and many others/passwd
- /wp-config.php
- .my.cnf
- .accesshash
Customers of the BackupBuddy plugin are suggested to improve to the newest model. Ought to customers decide that they might have been compromised, it is really useful to reset the database password, change WordPress Salts, and rotate API keys saved in wp-config.php.