A malicious marketing campaign mounted by the North Korea-linked Lazarus Group is focusing on vitality suppliers world wide, together with these based mostly in the US, Canada, and Japan.
“The marketing campaign is supposed to infiltrate organizations world wide for establishing long-term entry and subsequently exfiltrating knowledge of curiosity to the adversary’s nation-state,” Cisco Talos stated in a report shared with The Hacker Information.
Some parts of the espionage assaults have already entered public area, courtesy of prior studies from Broadcom-owned Symantec and AhnLab earlier this April and Might.
Symantec attributed the operation to a gaggle known as Stonefly, a Lazarus subgroup which is best often known as Andariel, Guardian of Peace, OperationTroy, and Silent Chollima.
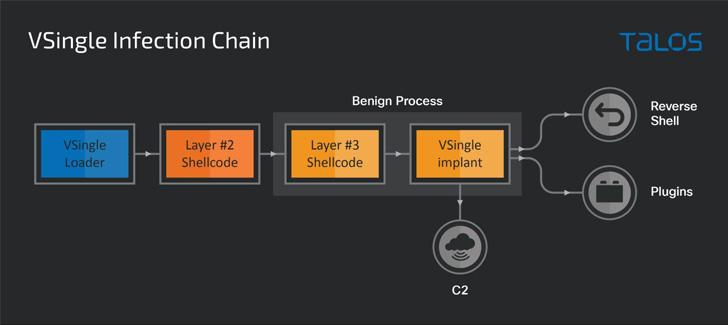
Whereas these assaults beforehand led to the instrumentation of Preft (aka Dtrack) and NukeSped (aka Manuscrypt) implants, the newest assault wave is notable for using two different items of malware: VSingle, an HTTP bot which executes arbitrary code from a distant community, and a Golang backdoor known as YamaBot.
Additionally put to make use of within the marketing campaign is a brand new distant entry trojan known as MagicRAT that comes with capabilities to evade detection and launch further payloads on the contaminated programs.
“Though the identical techniques have been utilized in each assaults, the ensuing malware implants deployed have been distinct from each other, indicating the big variety of implants out there on the disposal of Lazarus,” researchers Jung soo An, Asheer Malhotra, and Vitor Ventura stated.
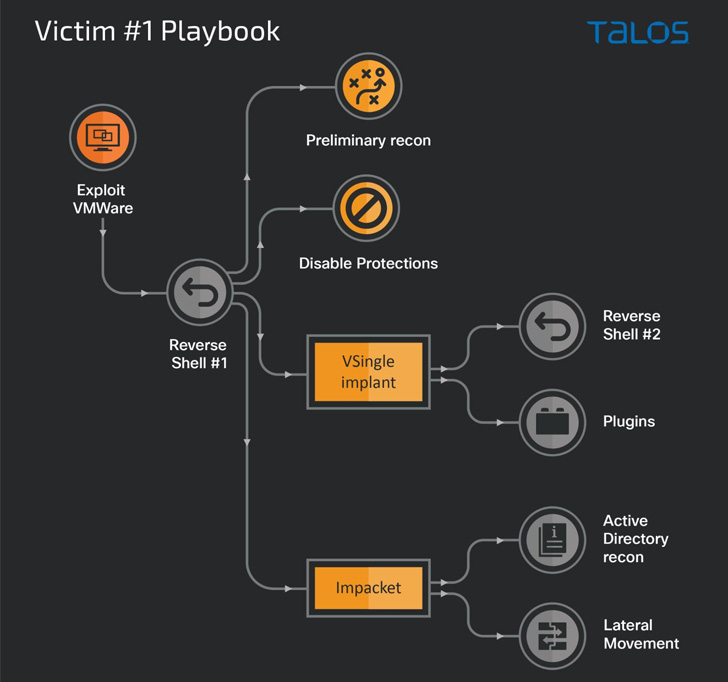
Preliminary entry into enterprise networks is facilitated via exploitation of vulnerabilities in VMware merchandise (e.g., Log4Shell), with the last word aim of building persistent entry to carry out actions in assist of North Korean authorities aims.
Using VSingle in a single assault chain is alleged to have enabled the risk actor to hold out quite a lot of actions equivalent to reconnaissance, exfiltration, and guide backdooring, giving the operators a stable understanding of the sufferer atmosphere.
Different techniques embraced by the group in addition to the usage of bespoke malware embody credential harvesting by way of instruments like Mimikatz and Procdump, disabling antivirus elements, and reconnaissance of the Energetic Listing companies, and even taking steps to cleanup their traces after activating the backdoors on the endpoint.