Excessive-profile firms and native governments situated primarily in Asia are the themes of focused assaults by a beforehand undocumented espionage group dubbed Worok that has been lively since late 2020.
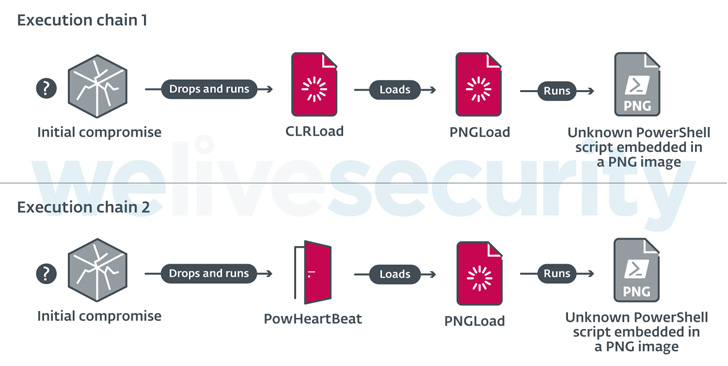
“Worok’s toolset features a C++ loader CLRLoad, a PowerShell backdoor PowHeartBeat, and a C# loader PNGLoad that makes use of steganography to extract hidden malicious payloads from PNG information,” ESET researcher Thibaut Passilly mentioned in a brand new report revealed immediately.
Worok is claimed to share overlaps in instruments and pursuits with one other adversarial collective tracked as TA428, with the group linked to assaults in opposition to entities spanning power, monetary, maritime, and telecom sectors in Asia in addition to a authorities company within the Center East and a non-public agency in southern Africa.
Malicious actions undertaken by the group skilled a noticeable break from Might 2021 to January 2022, earlier than resuming the following month. The Slovak cybersecurity agency assessed the group’s objectives to be aligned with info theft.
Preliminary foothold to focus on networks by way of 2021 and 2022 entailed the usage of ProxyShell exploits in choose situations, adopted by deploying extra customized backdoors for entrenched entry. Different preliminary compromise routes are unknown as but.
Among the many instruments in Worok’s malware arsenal is a first-stage loader referred to as CLRLoad, which is succeeded by a .NET-based steganographic loader codenamed PNGLoad that is able to executing an unknown PowerShell script embedded in a PNG picture file.
An infection chains in 2022 have since dropped CLRLoad in favor of a full-featured PowerShell implant known as PowHeartBeat that is subsequently used to launch PNGLoad, along with speaking with a distant server by way of HTTP or ICMP to execute arbitrary instructions, ship and obtain information, and perform associated file operations.
ESET mentioned it was unable to retrieve any of the final-stage PNG payloads, though it is suspected that the malware may very well be hid in legitimate, innocuous-looking PNG photographs and due to this fact “disguise in plain sight” with out attracting consideration.
“Worok is a cyber espionage group that develops its personal instruments, in addition to leveraging present instruments, to compromise its targets,” Passilly mentioned.
“Stealing info from their victims is what we imagine the operators are after as a result of they deal with high-profile entities in Asia and Africa, focusing on numerous sectors, each personal and public, however with a particular emphasis on authorities entities.”