Cybersecurity researchers have supplied perception right into a beforehand undocumented software program management panel utilized by a financially motivated menace group generally known as TA505.
“The group continuously adjustments its malware assault methods in response to world cybercrime traits,” Swiss cybersecurity agency PRODAFT stated in a report shared with The Hacker Information. “It opportunistically adopts new applied sciences as a way to achieve leverage over victims earlier than the broader cybersecurity trade catches on.”
Additionally tracked below the names Evil Corp, Gold Drake, Dudear, Indrik Spider, and SectorJ04, TA505 is an aggressive Russian cybercrime syndicate behind the notorious Dridex banking trojan and which has been linked to a variety of ransomware campaigns in recent times.
It is also stated to be linked to the Raspberry Robin assaults that emerged in September 2021, with similarities uncovered between the malware and Dridex.
Different notable malware households related to the group embrace FlawedAmmyy, Neutrino botnet, and a backdoor codenamed ServHelper, one variant of which is able to downloading a distant entry trojan known as FlawedGrace.
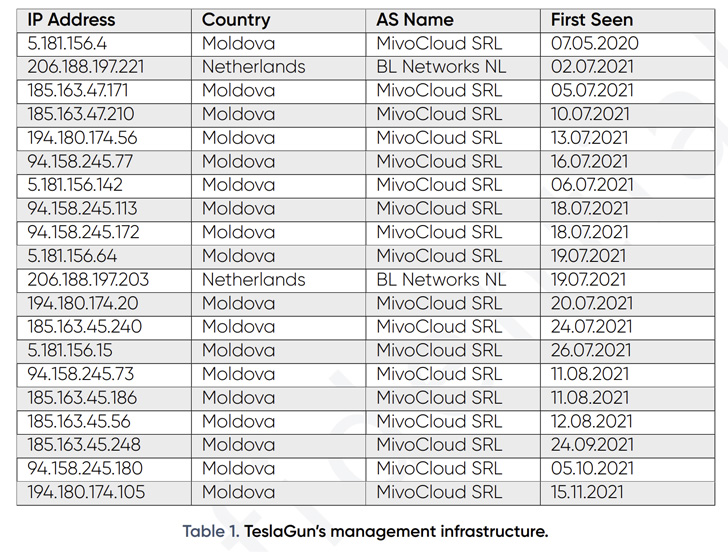
The management panel, known as TeslaGun, is alleged for use by the adversary to handle the ServHelper implant, working as a command-and-control (C2) framework to commandeer the compromised machines.
Moreover, the panel presents the flexibility for the attackers to problem instructions, to not point out ship a single command to all sufferer gadgets in go or configure the panel such {that a} predefined command is mechanically run when a brand new sufferer is added to the panel.
“The TeslaGun panel has a practical, minimalist design. The primary dashboard solely accommodates contaminated sufferer knowledge, a generic remark part for every sufferer, and a number of other choices for filtering sufferer data,” the researchers stated.
Except for utilizing the panel, the menace actors are additionally recognized to make use of a distant desktop protocol (RDP) device to manually connect with the focused techniques through RDP tunnels.
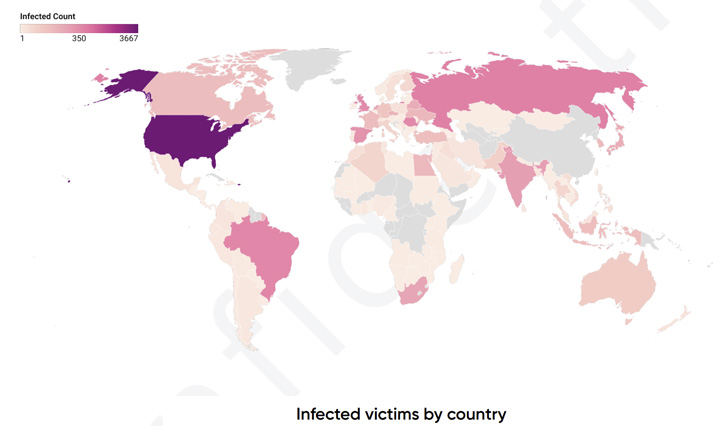
PRODAFT’s evaluation of TeslaGun sufferer knowledge reveals that the group’s phishing and focused campaigns have hit no less than 8,160 targets since July 2020. A majority of these victims are situated within the U.S. (3,667), adopted by Russia (647), Brazil (483), Romania (444), and the U.Ok. (359).
“It’s clear that TA505 is actively on the lookout for on-line banking or retail customers, together with crypto-wallets and e-commerce accounts,” the researchers famous, citing feedback made by the adversarial group within the TeslaGun panel.
The findings additionally come because the U.S. Division of Well being and Human Companies (HHS) warned of serious threats posed by the group to the well being sector through knowledge exfiltration assaults that intention to steal mental property and ransomware operations.
“Evil Corp has a large set of highly-capable instruments at their disposal,” the company’s Well being Sector Cybersecurity Coordination Heart (HC3) stated in an advisory printed late final month.
“These are developed and maintained in-house, however are sometimes used along with commodity malware, living-off-the-land methods and customary safety instruments that have been designed for official and lawful safety assessments.”