Organizing AWS assets to seek out assets, cut back errors, plan for development, and deal with safety incidents extra effectively
This can be a continuation of my collection on Automating Cybersecurity Metrics.
We’ve been creating quite a lot of issues with CloudFormation all through this weblog collection. It’s time to pause a bit and take into consideration how we would higher manage these assets — particularly for these in a big group.
Let’s say you might be looking by way of your account for all of the assets associated to a selected undertaking. Wouldn’t or not it’s good when you may simply kind an inventory by title and see all of the associated gadgets collectively? If you’re at a big firm, would you wish to see all of the gadgets in a selected division grouped collectively? What in case you are taking a look at CloudFormation stacks and also you wish to discover all of the templates that create a job?
AWS Tags
AWS Tags are sometimes touted as the answer to all of your issues when organizing assets for governance and billing. AWS Tags are helpful, however they’re additionally problematic. I’ve labored in a corporation with 11,000 builders who had been instructed to tag issues a sure approach. Let’s simply say that’s not gonna occur. If you need issues tagged appropriately you need to automate it. That’s what I did on the subsequent firm I went to. I obtained my DevOps staff to construct out a deployment system that mechanically tagged assets with person names primarily based on Lively Listing login names.
Tags produce other cons as properly. Though you need to use tags to attempt to categorize and search on gadgets, not all gadgets will be tagged. It’s additionally extra sophisticated to look the listing of CloudFormation stacks by tag than title. Should you’re attempting to base your billing off of tags there will probably be issues that fall between the cracks. Tags simply aren’t complete and they’re error inclined.
Moreover, it’s merely tougher to look on tags then simply sorting assets by title for people who find themselves utilizing the AWS Console. Now some builders on the market will scoff and say, “I can simply run an AWS CLI question and simply get this data!” Sure, you possibly can.
However it’s simpler to only log into the console and sort “function” and have all of the templates come up. There could also be a case the place an individual much less technical than you similar to an auditor, a safety one who doesn’t know find out how to program, or another person must shortly discover that data. Tags are attainable, however they aren’t as simple as a great naming conference.
AWS Useful resource Teams
You can even use one thing known as AWS Useful resource Teams to prepare your assets. This looks like an concept that obtained off the bottom however was by no means accomplished.
As soon as once more, you’ll be restricted to the assets that work with Useful resource Teams and there are quite a lot of assets lacking from this listing.
Not like Azure Useful resource Teams, AWS assets will not be required to outline a useful resource teams. Useful resource teams additionally will not be used for assigning insurance policies to a set of assets. They’re merely for grouping and querying associated gadgets.
One of many nicest issues about Useful resource Teams on Azure is the power to delete a useful resource group and mechanically every thing in that useful resource group is deleted. AWS Useful resource Teams don’t have that performance or something prefer it that I do know of — you’ll must create scripts to create and delete assets in a undertaking. I created such a script on this GitHub repo however it was a lot improved by the point I delivered it in school. It will provide you with an concept of what I’m speaking about nonetheless:
Grouping assets by accounts
Though the above strategies of grouping assets are attention-grabbing and could also be useful in some circumstances, I discover it simpler to place related gadgets in the identical account when safety is a matter. AWS accounts present the governance performance of administration teams and useful resource teams on Azure. They outline IAM boundaries that folks inside them can’t cross. It’s simpler to make sure an individual doesn’t go outdoors of that boundary inside an account than attempting to create sophisticated insurance policies primarily based on tags and circumstances inside an account.
The one draw back is when somebody wants cross-account entry issues can get difficult, and I’m not satisfied the logging is at all times adequate. I’m nonetheless exploring that matter. The opposite factor is that when you’re sending visitors cross-account you’ll must ship it outdoors the account. Should you ship it over the Web which is much less safe, it should price extra. It will likely be safer over a peering connection, however you will have to maintain it inside a single availability zone to keep away from further charges:
Including new accounts may additionally enhance charges when utilizing one thing like AWS Management Tower that costs you primarily based on the variety of Config Guidelines you create in every account.
One of many causes I’m trying into batch jobs and lambda features to set off actions throughout accounts is to beat this permission boundary difficulty. Keep tuned as I discover this concept as we proceed by way of this collection of weblog posts. Analysis is going on earlier than your very studying eyes.
Naming Conventions
Naming conventions may also help us manage and discover our assets. Completely different organizations might have totally different naming conventions primarily based on their dimension. For instance, a startup my manage gadgets by initiatives. A bigger group may additionally manage assets primarily based strains of enterprise and departments inside every line of enterprise.
One factor I discussed earlier than is that you could be wish to add a area title to your CloudFormation templates that title assets. Not solely will this assist you shortly determine the area the place a assets exists, it should additionally guarantee that you’ve got distinctive names throughout areas which is normally a requirement on AWS.
What kind of naming conference would you like? I’ve lately been discovering that naming conventions with a interval (.) are simpler to learn. Maintain that thought and browse the following part earlier than you begin naming your assets. First let’s think about what phrases we would need in our names.
Let’s say I’ve two departments — coaching and pentesting. I’ve initiatives (lessons and assessments) inside these departments. I might need naming conference like:
class.azure.customer1.resourcename
class.azure.customer2.resourcename
class.aws.customer3.resourcename
pentest.customer4.assets
pentest.customer5.assets
Now let’s say I’m on the safety staff and I wish to create batch jobs to run reviews for — safety metrics. I’ve numerous batch jobs that run totally different instruments and batch jobs that formulate the ultimate report. Perhaps I wish to have a naming conference that distinguishers batch jobs from different initiatives. My naming conference may look one thing like this:
batch.safety.instruments.2sl.recon
batch.safety.instruments.2sl.appscan
batch.safety.instruments.2sl.awsscan
batch.safety.instruments.2sl.gcpscan
batch.safety.instruments.2sl.awsnetworkmap
batch.safety.instruments.2sl.networkscan
batch.safety.instruments.2sl.appfuzz
batch.safety.report.information
batch.safety.report.remodel
batch.safety.report.gen
Should you plan to have failover to a different area, then you would need to add a area title to most assets like this:
batch.safety.instruments.2sl.recon.us-west-2
batch.safety.instruments.2sl.appscan.us-west-2
batch.safety.instruments.2sl.awsscan.us-west-2
batch.safety.instruments.2sl.gcpscan.us-west-2
batch.safety.instruments.2sl.awsnetworkmap.us-west-2
batch.safety.instruments.2sl.networkscan.us-west-2
batch.safety.instruments.2sl.appfuzz.us-west-2
batch.safety.report.information.us-west-2.
batch.safety.report.remodel.us-west-2
batch.safety.report.gen.us-west-2
or maybe like this:
batch.us-west-2.safety.instruments.2sl.recon
batch.us-west-2..safety.instruments.2sl.appscan
batch.us-west-2..safety.instruments.2sl.awsscan
batch.us-west-2.safety.instruments.2sl.gcpscan
batch.us-west-2.safety.instruments.2sl.awsnetworkmap
batch.us-west-2.safety.instruments.2sl.networkscan
batch.us-west-2.safety.instruments.2sl.appfuzz
batch.us-west-2..safety.report.information
batch.us-west-2..safety.report.remodel
batch.us-west-2..safety.report.gen
There’s nobody proper reply as to how you need to title your assets.
Caveat: AWS Naming Conventions are Fully Incosistent!
I like to call my CloudFormation templates the identical title because the useful resource it creates, however embrace the kind of useful resource. Or I’d put the useful resource sort within the useful resource title. I’d love to make use of the identical naming conventions inside my CloudFormation templates.
That’s pretty however right here’s the place we run into an issue. AWS naming conventions are fully inconsistent so it’s just about inconceivable to do this. Earlier than you determine on a naming conference check out the title restrictions for all of the assets we created and a few further assets we plant to create:
- S3 buckets
- Lambda Capabilities
- Stack Names
- CloudFormation Assets, StackNames, Parameters Outputs
- CloudFormation Outputs
- IAM Customers, Teams, Roles, Insurance policies
- KMS Keys
- Key Aliases
- VPCs, Safety Teams, Subnets, Route Tables
- Secrets and techniques, Parameter Retailer Parameters
I put this collectively in a spreadsheet which is a bit laborious to learn right here however let me sum it up for you beneath.
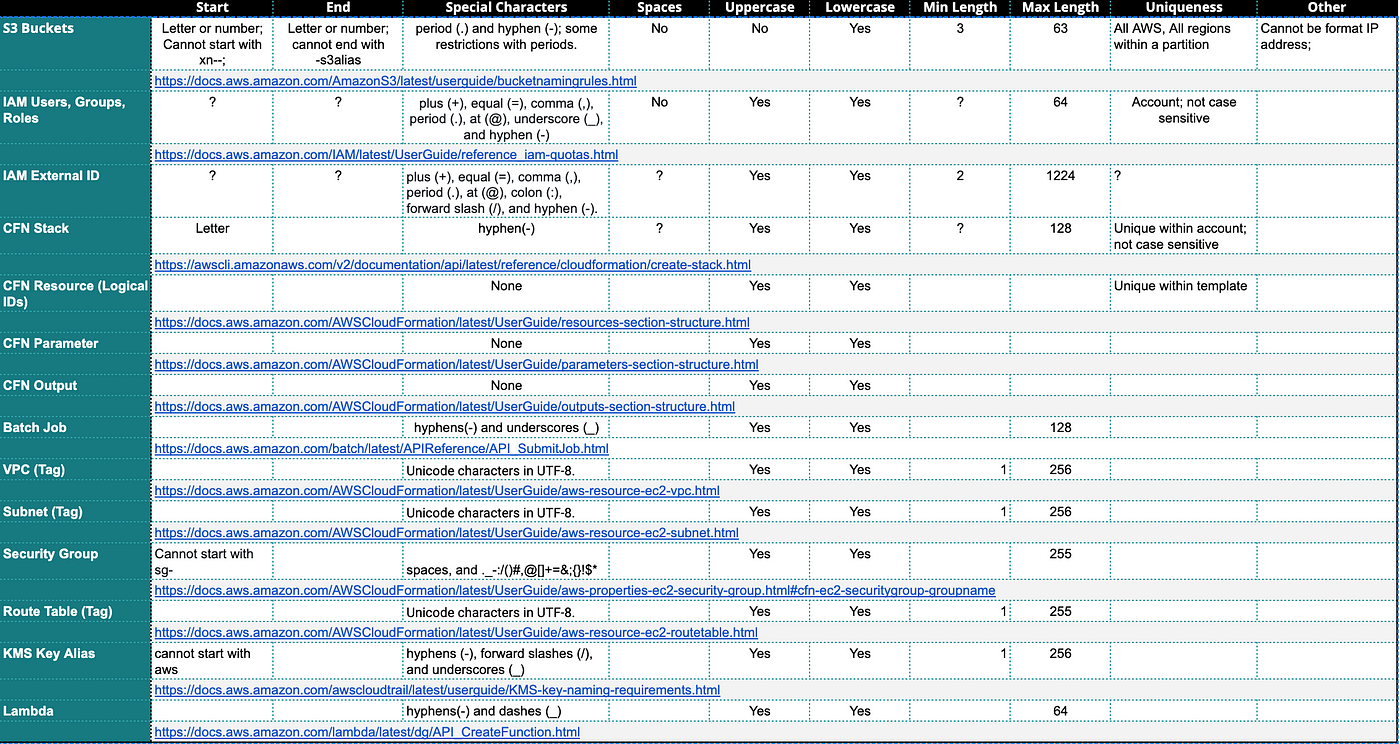
If you wish to use a naming conference that works throughout all these kinds of names you might have one choice: all decrease case.
There’s one character which appears to be allowed in all assets besides these inside a CloudFormation template: a splash (-).
So for every thing besides the assets inside a CloudFormation template we are able to use lowercase and a splash.
For the gadgets inside a template we are able to use a CamelCaseNamingConvention.
Additionally word that many AWS assets have to begin and finish with a letter. That’s a bummer for my firm, 2nd Sight Lab. I can’t begin most useful resource names with a 2.
So for our batch jobs we would find yourself with one thing like this:
batch-us-west-2-security-tools-2sl-recon
batch-us-west-2-security-tools-2sl-appscan
batch-us-west-2-security-tools-2sl-awsscan
batch-us-west-2-security-tools-2sl-gcpscan
batch-us-west-2-security-tools-2sl-awsnetworkmap
batch-us-west-2-security-tools-2sl-networkscan
batch-us-west-2-security-tools-2sl-appfuzz
batch-us-west-2-security-report-data
batch-us-west-2-security-report-transform
batch-us-west-2-security-report-gen
After all, that may be a little complicated as a result of us-west-2 has dashes in it so we’re probably not delineating the area. However at the very least it appears to be like form of constant.
What concerning the assets we create like IAM roles and KMS keys. Will we wish to see these related to our batch jobs? Or do we wish then title of every useful resource to begin or finish the useful resource it’s? (function, key, person, job, lamba). In my case, I run the roles for various prospects so a key title might need a particular buyer related to it. An IAM function is likely to be associated to a particular check. So I’ll most likely find yourself sticking with the primary naming conference.
class-us-west-2-azure-customer1-s3bucket
pentest-us-west-2-customer2-iamrole
pentest-us-west-2-customer2-kmskey
I used to be simply making a Lambda operate to retrieve the credentials I encrypted earlier. The Lambda operate title was TriggerBatchJob. I’ll most likely camel case the useful resource title within the CloudFormation stack to maintain it collectively however make it extra readable. Possible I’ll drop the useful resource sort on the finish within the title of the useful resource.
lambda-us-west-2-TriggerBatchJob
lambda-us-west-2-TriggerBatchJob-kmskey
lambda-us-west-2-TriggerBatchJob-iamrole
lambda-us-west-2-TriggerBatchJob-iampolicy
The one factor that gained’t work for can be an S3 bucket. The CloudFormation stack may stay constant above. The S3 bucket would look one thing like this (dropping the useful resource title on the precise useful resource):
lambda-us-west-2-trigger-batch-job
or
lambda-us-west-2-triggerbatchjob
What about generic IAM insurance policies? We now have KMS admins and the associated coverage. These aren’t related to a selected undertaking, class, or penetration check. We are able to title IAM assets not related to a undertaking or software with an iam prefix:
iam-kms-admin
iam-admin
iam-batch-job-admin
If I began hiring a lot of penetration testers, builders, interns, and trainers to assist me out I’d add roles like this:
iam-pentester
iam-developer
iam-trainer
iam-intern
These people would have the ability to assume roles for a particular penetration check, class, or improvement undertaking.
I haven’t fully determined that that is the ultimate naming conference, however that appears prefer it decently retains assets collectively. I’ll must do some refactoring once more to attempt it out and ensure it really works.
And for my subsequent #awswishlist requests:
- Enable prospects to make use of the identical naming conference in all places together with uppercase letters and intervals at the very least.
- Create one thing like an Azure useful resource group to which prospects can apply insurance policies to a bunch of assets and simply delete them .
Teri Radichel
Should you appreciated this story please clap and comply with:
Medium: Teri Radichel or E mail Record: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, displays, and podcasts


