Costa Rica’s nationwide well being service was hacked someday earlier this morning by a Russian ransomware group referred to as Hive. The intrusion comes simply weeks after Costa Rican President Rodrigo Chaves declared a state of emergency in response to an information ransom assault from a special Russian ransomware gang — Conti. Ransomware consultants say there’s good cause to imagine the identical cybercriminals are behind each assaults, and that Hive has been serving to Conti rebrand and evade worldwide sanctions focusing on extortion payouts to cybercriminals working in Russia.
The Costa Rican publication CRprensa.com studies that affected techniques on the Costa Rican Social Safety Fund (CCSS) had been taken offline on the morning of Might 31, however that the extent of the breach was nonetheless unclear. The CCSS is liable for Costa Rica’s public well being sector, and employee and employer contributions are mandated by legislation.
The fallout from this newest assault will not be but clear, however it’s more likely to be disruptive: A hand-written signal posted outdoors a public well being heart in Costa Rica in the present day defined that every one techniques are down till additional discover (due to @Xyb3rb3nd3r for sharing this photograph).

A hand-written discover posted outdoors a public well being clinic in the present day in Costa Rica warned of system outages because of a cyberattack on the nation’s healthcare techniques.
A duplicate of the ransom observe left behind by the intruders and subsequently uploaded to Virustotal.com signifies the CCSS intrusion was the work of Hive, which generally calls for cost for a digital key wanted to unlock recordsdata and servers compromised by the group’s ransomware.
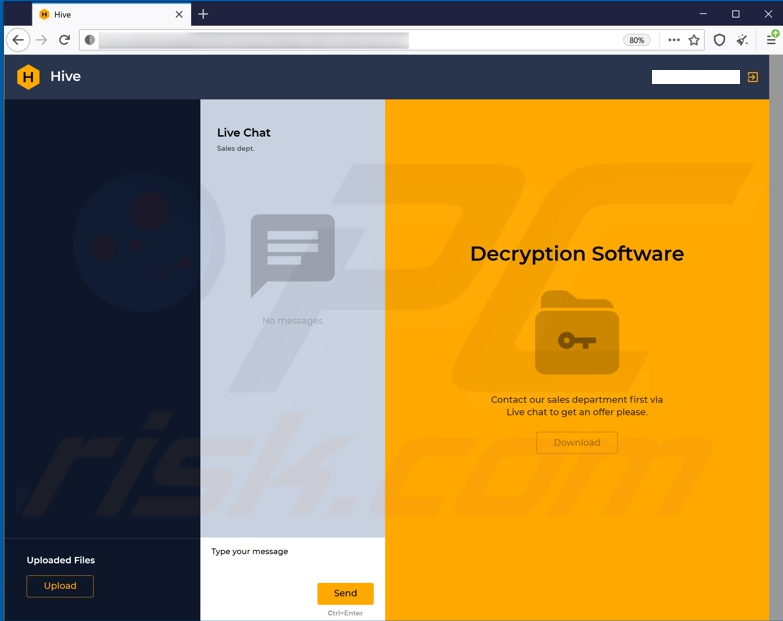
A HIVE ransomware chat web page for a particular sufferer (redacted).
On Might 8, President Chaves used his first day in workplace to declare a nationwide state of emergency after the Conti ransomware group threatened to publish gigabytes of delicate knowledge stolen from Costa Rica’s Ministry of Finance and different authorities companies. Conti initially demanded $10 million, and later doubled the quantity when Costa Rica refused to pay. On Might 20, Conti leaked greater than 670 gigabytes of information taken from Costa Rican authorities servers.
As CyberScoop reported on Might 17, Chaves instructed native media he believed that collaborators inside Costa Rica had been serving to Conti extort the federal government. Chaves supplied no info to help this declare, however the timeline of Conti’s descent on Costa Rica is value inspecting.
Most of Conti’s public communications in regards to the Costa Rica assault have very clearly assigned credit score for the intrusion to a person or group calling itself “unc1756.” In March 2022, a brand new consumer by the identical identify registered on the Russian language crime discussion board Exploit.
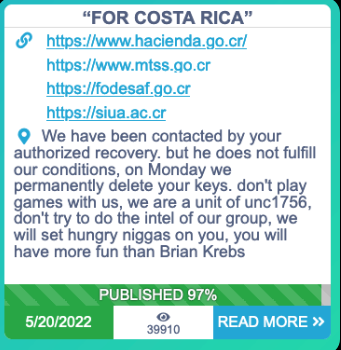
A message Conti posted to its darkish net weblog on Might 20.
On the night of April 18, Costa Rica’s Ministry of Finance disclosed the Conti intrusion through Twitter. Earlier that very same day, the consumer unc1756 posted a assist wished advert on Exploit saying they had been seeking to purchase entry to “particular networks” in Costa Rica.
“By particular networks I imply one thing like Haciendas,” unc1756 wrote on Exploit. Costa Rica’s Ministry of Finance is understood in Spanish because the “Ministerio Hacienda de Costa Rica.” Unc1756 stated they’d pay $USD 500 or extra for such entry, and would work solely with Russian-speaking individuals.
THE NAME GAME DISTRACTION
Specialists say there are clues to recommend Conti and Hive are working collectively of their assaults on Costa Rica, and that the intrusions are tied to a rebranding effort by Conti. Shortly after Russia invaded Ukraine on the finish of February, Conti declared its full help, aligning itself immediately with Russia and towards anybody who would stand towards the motherland.
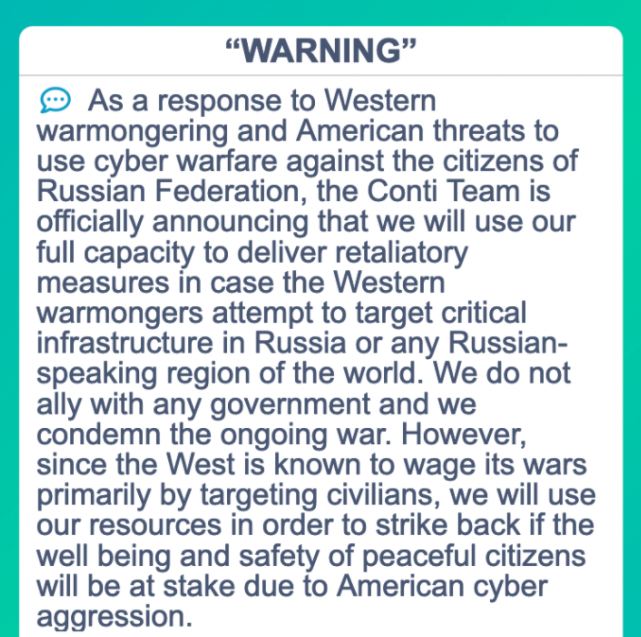
Conti’s threatening message this week relating to worldwide interference in Ukraine.
Conti rapidly deleted the declaration from its web site, however the harm had already been executed, and any favor or esteem that Conti had earned among the many Ukrainian cybercriminal underground successfully evaporated in a single day.
Shortly thereafter, a Ukrainian safety skilled leaked many months value of inner chat data between Conti personnel as they plotted and executed assaults towards lots of of sufferer organizations. These candid messages uncovered what it’s wish to work for Conti, how they undermined the safety of their targets, in addition to how the group’s leaders strategized for the higher hand in ransom negotiations.
However Conti’s declaration of solidarity with the Kremlin additionally made it more and more ineffective as an instrument of monetary extortion. In keeping with cyber intelligence agency ADVIntel, Conti’s alliance with the Russian state quickly left it largely unable to obtain ransom funds as a result of sufferer corporations are being suggested that paying a Conti ransom demand might imply violating U.S. financial sanctions on Russia.
“Conti as a model grew to become related to the Russian state — a state that’s at present present process excessive sanctions,” ADVIntel wrote in a prolonged evaluation (PDF). “Within the eyes of the state, every ransom cost going to Conti could have probably gone to a person beneath sanction, turning easy knowledge extortion right into a violation of OFAC regulation and sanction insurance policies towards Russia.”
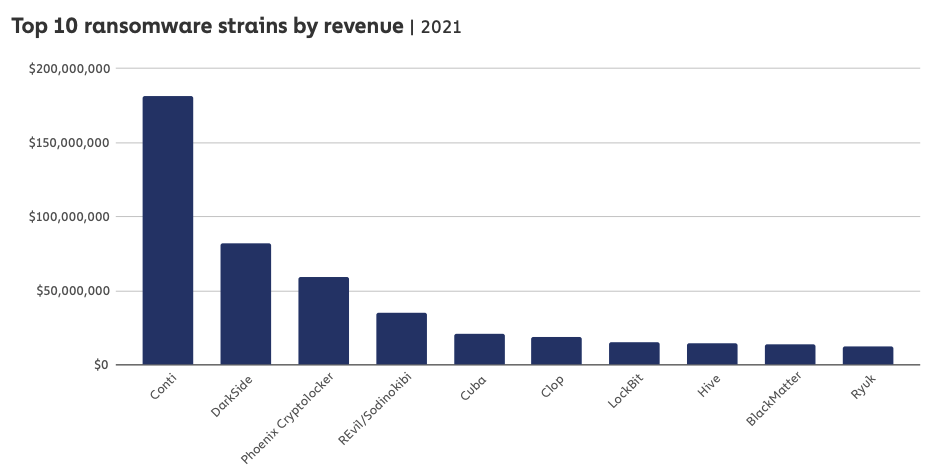
Conti is by far essentially the most aggressive and worthwhile ransomware group in operation in the present day. Picture: Chainalysis
ADVIntel says it first discovered of Conti’s intrusion into Costa Rican authorities techniques on April 14, and that it has seen inner Conti communications indicating that getting paid within the Costa Rica assault was not the objective.
Slightly, ADVIntel argues, Conti was merely utilizing it as a solution to seem publicly that it was nonetheless working because the world’s most profitable ransomware collective, when in actuality the core Conti management was busy dismantling the crime group and folding themselves and high associates into different ransomware teams which might be already on pleasant phrases with Conti.
“The one objective Conti had wished to satisfy with this ultimate assault was to make use of the platform as a instrument of publicity, performing their very own dying and subsequent rebirth in essentially the most believable means it might have been conceived,” ADVIntel concluded.
ADVIntel says Conti’s leaders and core associates are dispersing to a number of Conti-loyal crime collectives that use both ransomware lockers or strictly have interaction in knowledge theft for ransom, together with AlphV/BlackCat, AvosLocker, BlackByte, HelloKitty, Hive, and Karakurt.
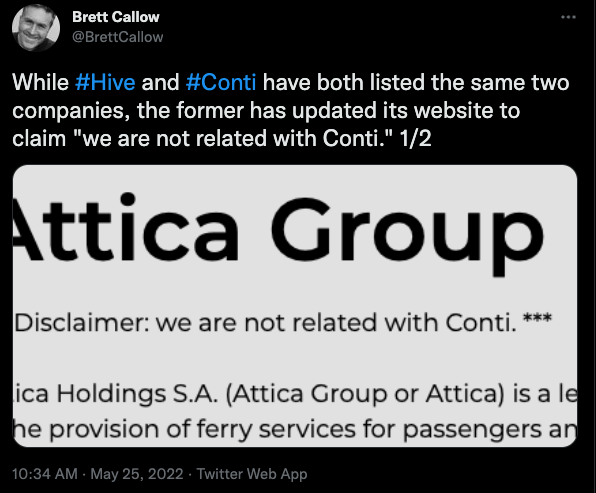
Nonetheless, Hive seems to be maybe the most important beneficiary of any attrition from Conti: Twice over the previous week, each Conti and Hive and claimed duty for hacking the identical corporations. When the discrepancy was referred to as out on Twitter, Hive up to date its web site to say it was not affiliated with Conti.
Conti and Hive’s Costa Rican exploits mark the newest in a string of current cyberattacks towards authorities targets throughout Latin America. Across the similar time it hacked Costa Rica in April, Conti introduced it had hacked Peru’s Nationwide Directorate of Intelligence, threatening to publish delicate stolen knowledge if the federal government didn’t pay a ransom.
However Conti and Hive usually are not alone in focusing on Latin American victims of late. In keeping with knowledge gathered from the sufferer shaming blogs maintained by a number of ransomware teams, over the previous 90 days ransom actors have hacked and sought to extort 15 authorities companies in Brazil, 9 in Argentina, six in Columbia, 4 in Ecuador and three in Chile.
A current report (PDF) by the Inter-American Improvement Financial institution suggests many Latin American international locations lack the technical experience or cybercrime legal guidelines to cope with in the present day’s threats and menace actors.
“This research reveals that the Latin American and Caribbean (LAC) area will not be sufficiently ready to deal with cyberattacks,” the IADB doc explains. “Solely 7 of the 32 international locations studied have a vital infrastructure safety plan, whereas 20 have established cybersecurity incident response groups, typically referred to as CERTs or CSIRTs. This limits their skill to establish and reply to assaults.”

