The menace actor behind the assaults on Twilio and Cloudflare earlier this month has been linked to a broader phishing marketing campaign geared toward 136 organizations that resulted in a cumulative compromise of 9,931 accounts.
The exercise has been condemned 0ktapus by Group-IB as a result of the preliminary objective of the assaults was to “acquire Okta identification credentials and two-factor authentication (2FA) codes from customers of the focused organizations.”
Calling the assaults properly designed and executed, the Singapore-headquartered firm mentioned the adversary singled out workers of firms which might be prospects of identification providers supplier Okta.
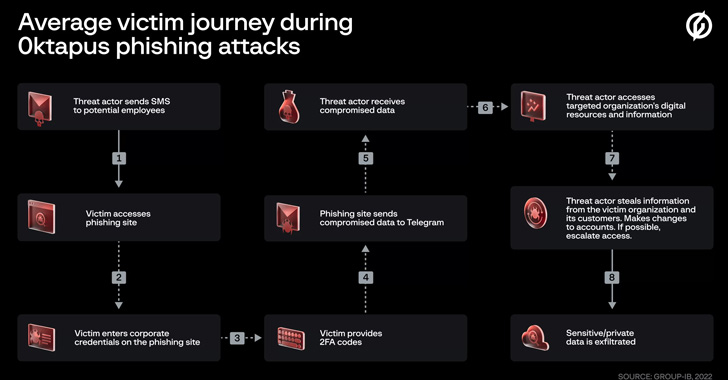
The modus operandi concerned sending targets textual content messages containing hyperlinks to phishing websites that impersonated the Okta authentication web page of the respective focused entities.
“This case is of curiosity as a result of regardless of utilizing low-skill strategies it was capable of compromise numerous well-known organizations,” Group-IB mentioned. “Moreover, as soon as the attackers compromised a corporation they have been shortly capable of pivot and launch subsequent provide chain assaults, indicating that the assault was deliberate rigorously prematurely.”
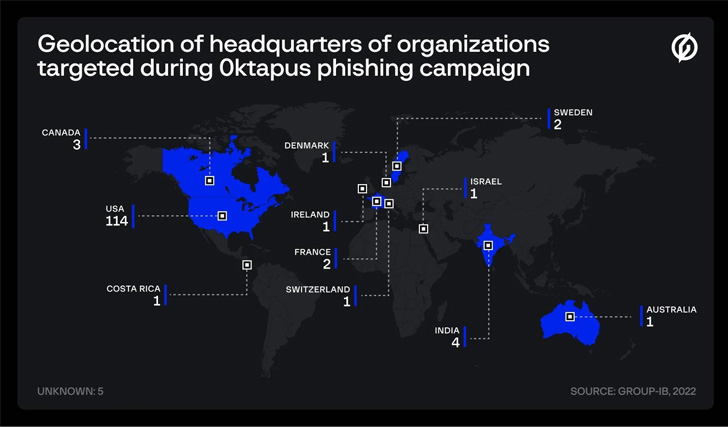
Not less than 169 distinctive phishing domains are mentioned to have been arrange for this objective, with sufferer organizations primarily situated within the U.S. (114), India (4), Canada (3), France (2), Sweden (2), and Australia (1), amongst others. These web sites have been united by the truth that they made use of a beforehand undocumented phishing equipment.
A majority of the affected organizations are software program firms, adopted by these belonging to telecom, enterprise providers, finance, training, retail, and logistics sectors.
What’s notable in regards to the assaults is using an actor-controlled Telegram channel to drop the compromised data, which included person credentials, electronic mail addresses, and multi-factor authentication (MFA) codes.
Group-IB mentioned it was capable of hyperlink one of many channel directors, who goes by the alias X, to a Twitter and a GitHub account that implies the person could also be primarily based within the U.S. state of North Carolina.
The final word targets of the marketing campaign stay unclear, however it’s suspected to be espionage and financially motivated, enabling the menace actor to entry confidential information, mental property, and company inboxes, in addition to siphon funds.
On high of that, the makes an attempt to hack into Sign accounts indicate that the attackers are additionally making an attempt to pay money for personal conversations and different delicate information. It is nonetheless not recognized how the hackers obtained cellphone numbers and the names of workers.
“Whereas the menace actor might have been fortunate of their assaults it’s way more probably that they rigorously deliberate their phishing marketing campaign to launch refined provide chain assaults,” Group-IB analyst Roberto Martinez mentioned.
“It isn’t but clear if the assaults have been deliberate end-to-end prematurely or whether or not opportunistic actions have been taken at every stage. Regardless, the 0ktapus marketing campaign has been extremely profitable, and the total scale of it is probably not recognized for a while.”