Profitable hacking includes extra than simply gaining unauthorized entry to a system. As soon as inside, malicious actors prefer to cowl their tracks not solely to forestall getting caught, but in addition to maximise how a lot knowledge they’ll extract. To this finish, the Iranian-backed hacker group often known as Charming Kitten has been found utilizing a easy however efficient technique of evading detection.
Charming Kitten is understood for focusing on people that discover themselves at odds with the Iranian regime. One among its techniques was to make use of a instrument known as HYPERSCRAPE to steal knowledge from sufferer’s e mail accounts. HYPERSCRAPE – to not be confused with Ubisoft’s Hyper Scape – was first detected in 2021 by Google’s Menace Evaluation Group (TAG) and proof of its use dates again to 2020. TAG has now launched a breakdown of how the instrument operated.
HYPERSCRAPE is a comparatively easy .NET software which acts as a follow-on instrument as soon as a consumer’s account has already been compromised. Attackers must both receive a sufferer’s credentials via different means or hijack an authenticated session first. HYPERSCRAPE is then used to obtain the contents of an inbox with none signal to the sufferer that one thing is amiss. It has been used towards Gmail, Yahoo!, and Outlook accounts, however solely its methodology towards Gmail is detailed within the writeup.
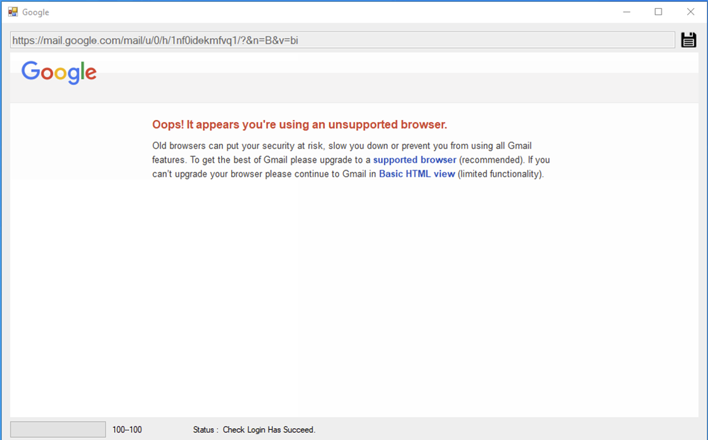
HYPERSCRAPE first tips Gmail into displaying the fundamental HTML view as a substitute of utilizing its new enhanced interface. It accomplishes this by setting its Person Agent to show as an outdated browser. HTML view permits the instrument to instantly parse emails. After logging in, HYPERSCRAPE briefly adjustments the inbox’s language to English.
The instrument then downloads every e mail within the account one after the other. If an e mail was beforehand unread, the instrument takes care to mark it as unread after downloading. As soon as completed, the instrument reverts the settings it modified and deletes all safety notices from Google which leaves the sufferer none-the-wiser. Accounts can stay compromised indefinitely for continued surveillance.
TAG experiences that HYPERSCRAPE has been successfully deployed towards fewer than two dozen accounts inside Iran as a result of Charming Kitten’s very selective focusing on. However, the prospect of an entire and largely automated data dump may be very regarding. Different events may leverage related techniques for espionage, extortion, suppression, or worse at a broader scale. It additionally goes to point out how modernized defenses will be successfully side-stepped so long as legacy capabilities are in place.
Google’s TAG doesn’t disclose any explicit measures taken to forestall this assault from working sooner or later. HTML view remains to be a necessary fallback perform for a lot of customers all over the world. As an alternative, TAG recommends that high-risk customers who could also be focused in such an assault ought to leverage Google’s Superior Safety Program and Account Stage Enhanced Protected Searching to extend their defensive posture.
High Picture Credit score – Ashutosh Sonwani on Pexels