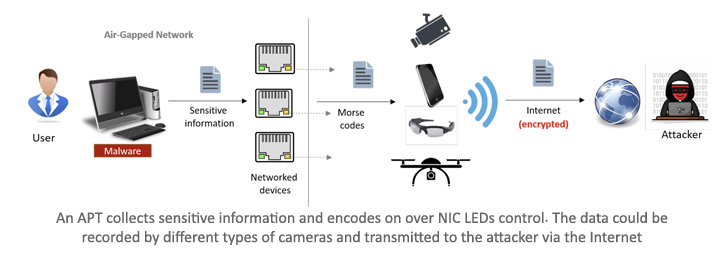
A safety researcher who has a protracted line of labor demonstrating novel knowledge exfiltration strategies from air-gapped programs has provide you with yet one more method that includes sending Morse code indicators by way of LEDs on community interface playing cards (NICs).
The method, codenamed ETHERLED, comes from Dr. Mordechai Guri, the pinnacle of R&D within the Cyber Safety Analysis Heart within the Ben Gurion College of the Negev in Israel, who just lately outlined GAIROSCOPE, a technique for transmitting knowledge ultrasonically to smartphone gyroscopes.
“Malware put in on the system may programmatically management the standing LED by blinking or alternating its colours, utilizing documented strategies or undocumented firmware instructions,” Dr. Guri stated.
“Data could be encoded by way of easy encoding reminiscent of Morse code and modulated over these optical indicators. An attacker can intercept and decode these indicators from tens to a whole bunch of meters away.”
A community interface card, often known as a community interface controller or community adapter, is a pc {hardware} part that connects a pc to a pc community. LEDs built-in into the community connector notify the person of whether or not the community is linked, and when knowledge exercise happens.
ETHERLED, like different adversarial approaches towards air-gapped programs, requires the intruder to breach the goal surroundings and plant malicious code that makes it doable to regulate the NIC LEDs.
The second section of the assault pertains to knowledge assortment and exfiltration, throughout which delicate data is encoded and despatched over an optical covert channel through the use of the community card’s standing LEDs.
Within the ultimate stage, the optical indicators are obtained by way of a hidden digicam that is positioned in a location with a direct line of sight with the compromised transmitting pc. Alternatively, the digicam may be a surveillance digicam that is susceptible to distant exploitation or a smartphone that includes a rogue insider.
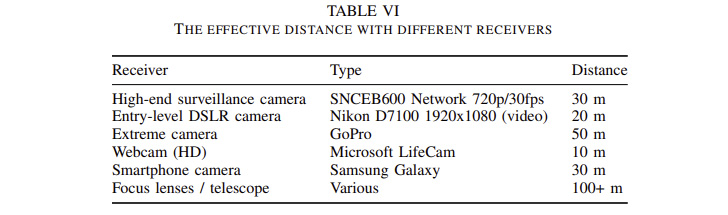
The assault can be utilized to leak varied varieties of data, together with passwords, RSA encryption keys, keystrokes, and textual content material, to cameras positioned wherever between 10m and 50m, a distance that may be additional prolonged to some hundred meters through the use of a telescope and particular focus lenses.
What’s extra, the ETHERLED methodology is designed to work with any peripheral or {hardware} that is shipped with Ethernet playing cards, reminiscent of printers, community cameras, network-attached storage (NAS) gadgets, embedded programs, and different IoT gadgets.
Countermeasures embrace proscribing cameras and video recorders in delicate zones, protecting the standing LEDs with black tape to dam the optical emanation bodily, reprogramming the software program to defeat the encoding scheme, and jamming the surroundings so as to add random noise to the modulated indicators.