The operators of the XCSSET macOS malware have upped the stakes by making iterative enhancements that add help for macOS Monterey by upgrading its supply code elements to Python 3.
“The malware authors have modified from hiding the first executable in a faux Xcode.app within the preliminary variations in 2020 to a faux Mail.app in 2021 and now to a faux Notes.app in 2022,” SentinelOne researchers Phil Stokes and Dinesh Devadoss mentioned in a report.
XCSSET, first documented by Development Micro in 2020, has many transferring components that permit it to harvest delicate info from Apple Notes, WeChat, Skype, and Telegram; inject malicious JavaScript code into numerous web sites; and dump cookies from Safari net browser.
An infection chains entail utilizing a dropper to compromise customers’ Xcode initiatives with the backdoor, with the latter additionally taking steps to evade detection by masquerading as both system software program or the Google Chrome net browser software.
The first executable is an AppleScript that is designed to retrieve second-stage AppleScript payloads from a community of distant servers that siphon knowledge saved in net browsers similar to Google Chrome, Mozilla Firefox, Microsoft Edge, Courageous, and Yandex Browser in addition to chat apps like Telegram and WeChat.
The menace actor can be identified to make use of a customized AppleScript (“itemizing.applescript”) to find out “how up-to-date the sufferer is with Apple’s XProtect and MRT malware removing instrument, presumably all the higher to focus on them with more practical payloads,” the researchers mentioned.
One of many novel points of the assault is that deploying the malware inside Xcode initiatives is seen as a way of propagation by way of GitHub repositories to additional increase its attain.
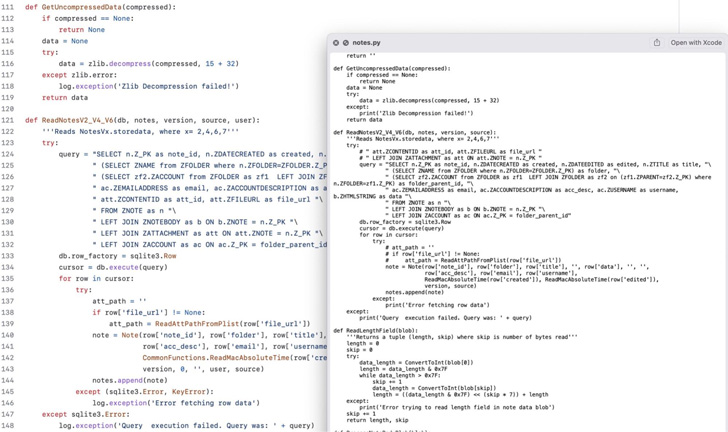
In addition to leveraging AppleScripts, the malware additionally takes benefit of Python scripts for dropping faux software icons on the macOS Dock and stealing knowledge from the reputable Notes app.
The most recent model of XCSSET can be notable for incorporating modifications to AppleScripts to account for Apple’s removing of Python 2.7 from macOS 12.3 launched on March 14, 2022, indicating that the authors are regularly updating the malware to extend their probability of success.
To that finish, the adversary is alleged to have up to date their “safari_remote.applescript” by eliminating Python 2 in favor of Python 3 for programs working macOS Monterey 12.3 and above.
Regardless of being within the wild for 2 years, little or no is understood in regards to the id of the menace actors and their motivations or their precise targets. That mentioned, XCSSET malware assaults have been reported in China as lately as Could 2022 that demanded victims pay 200 USDT in return for unlocking stolen accounts.
“At this time limit, it is unclear whether or not these contaminated repos are victims or crops by menace actors hoping to contaminate unwary customers,” the researchers famous. “It has been advised that unsuspecting customers could also be pointed to the contaminated repositories by way of tutorials and screencasts for novice builders.”