Particulars of an eight-year-old safety vulnerability within the Linux kernel have emerged that the researchers say is “as nasty as Soiled Pipe.”
Dubbed DirtyCred by a bunch of lecturers from Northwestern College, the safety weak point exploits a beforehand unknown flaw (CVE-2022-2588) to escalate privileges to the utmost degree.
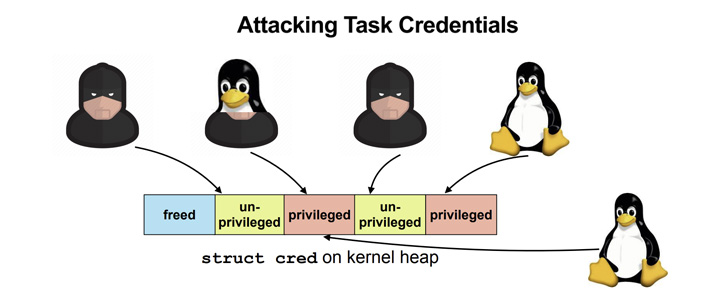
“DirtyCred is a kernel exploitation idea that swaps unprivileged kernel credentials with privileged ones to escalate privilege,” researchers Zhenpeng Lin, Yuhang Wu, and Xinyu Xing famous. “As an alternative of overwriting any crucial information fields on kernel heap, DirtyCred abuses the heap reminiscence reuse mechanism to get privileged.”
This entails three steps –
- Free an in-use unprivileged credential with the vulnerability
- Allocate privileged credentials within the freed reminiscence slot by triggering a privileged userspace course of corresponding to su, mount, or sshd
- Function as a privileged person
The novel exploitation methodology, in accordance with the researchers, pushes the soiled pipe to the following degree, making it extra normal in addition to potent in a way that would work on any model of the affected kernel.
“First, moderately than tying to a particular vulnerability, this exploitation methodology permits any vulnerabilities with double-free capacity to exhibit dirty-pipe-like capacity,” the researchers stated.
“Second, whereas it’s just like the soiled pipe that would bypass all of the kernel protections, our exploitation methodology may even exhibit the flexibility to flee the container actively that Soiled Pipe shouldn’t be able to.”
Soiled Pipe, tracked as CVE-2022-0847 (CVSS rating: 7.8) and affecting Linux kernel variations ranging from 5.8, refers to a safety vulnerability within the pipe subsystem that enables underprivileged processes to jot down to arbitrary readable information, resulting in privilege escalation.
The exploitable vulnerability was so referred to as after the Soiled Cow vulnerability found in 2016 primarily based on their similarities.
On condition that objects are remoted primarily based on their sort and never privileges, the researchers advocate isolating privileged credentials from unprivileged ones utilizing digital reminiscence to forestall cross-cache assaults.