This assault mirrored the smishing assault suffered by Twilio, which doesn’t come as a shock since Twilio hinted that different firms had been hit by the identical assault. Cloudflare’s weblog publish recounting the assault contains extra particulars that reveal how subtle and fast paced the assault was. Cloudflare staff are educated to report suspicious messages and habits to the corporate’s Safety Incident Response Staff, and Twilio staff are possible educated to file related stories. Because of this, the attackers have to maneuver shortly so as to achieve success.
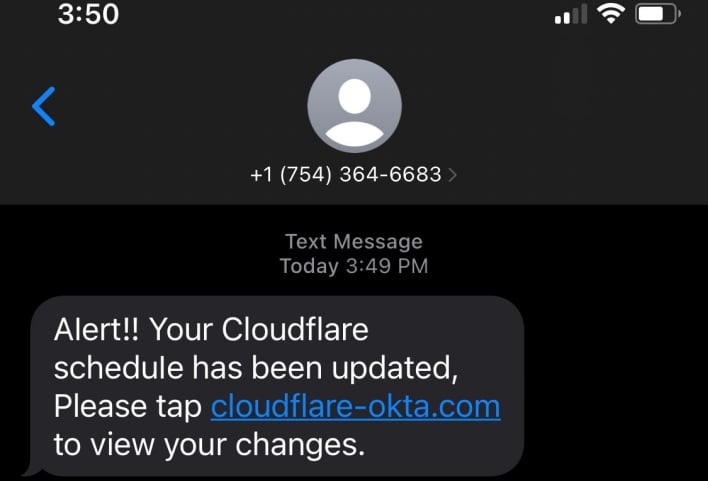
The fraudulent messages directed their recipients to go to the area cloudflare-okta.com. Some staff took this to be a reliable Cloudflare area, for the reason that firm makes use of Okta as its id supplier. The risk actors registered this area lower than 40 minutes earlier than sending the fraudulent SMS messages. Registering the area this shortly beforehand additionally speaks to the pace and class of the assault. Cloudflare runs an automatic system that detects newly registered domains utilizing the Cloudflare model identify so the corporate can shut them down. Nevertheless, the risk actors registered their area so quickly earlier than the assault that the area was not but revealed as a brand new registration on the time of the assault. Because of this, Cloudflare’s automated system hadn’t but alerted the corporate of the fraudulent area’s registration.
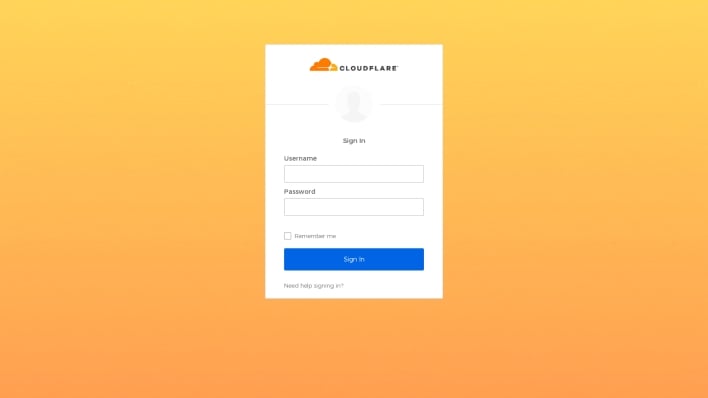
That stated, the risk actors had been in a position to achieve unauthorized entry to Twilio’s inside programs, so presumably Twilio does use TOTPs for 2FA, and a few of its staff entered TOTPs when prompted to take action. These codes had been then despatched to the attackers through Telegram, and subsequently entered into Twilio’s precise login web page, defeating Twilio’s 2FA safety measure. The truth that Cloudflare was in a position to thwart this smishing assault, whereas Twilio was not, demonstrates how {hardware} safety keys can forestall distant cyberattacks from succeeding. Cloudflare attests to this takeaway in its weblog publish, stating that the corporate hasn’t skilled any profitable phishing assaults since implementing bodily safety keys.


