Understanding how Web3.0 allows machine studying to work with out violating privateness and sustaining belief.
Machine Studying is all about discovering latent relationships inside knowledge. These relationships can then be used to realize actionable insights for any enterprise.
Nonetheless, current years have proven an growing consciousness round possession of information by governments(ex: GDPR in Europe) and customers usually. Immediately, persons are not okay with their non-public knowledge getting used for analytics as per the whims and desires of an organization.
This results in the next dilemma:
- Corporations have to carry out analytics on consumer knowledge to higher perceive and improvise their companies. The extra knowledge they’ll get the higher their insights are. This creates a robust incentive to amass knowledge from different customers or third social gathering corporations. There may be additionally a robust financial incentive to promote knowledge as an asset to different corporations.
- Customers understand that their private knowledge will be misused or leaked to different corporations. This disincentivizes them to share knowledge with corporations.
How can we resolve this dilemma?
Web3.0 brings with it the thought of Zero Information Proofs to unravel such issues.
Zero Information Proofs are helpful in purposes the place knowledge privateness is paramount. ZKPs allow an software to show that an perception from knowledge is appropriate with out revealing the underlying knowledge.
A ZKP will be understood as an interplay between two gamers, a Prover and a Verifier.
- Prover: A prover executes a computation and desires to show to any third social gathering that the computation was legitimate.
- Verifier: A verifier’s function is to confirm that the computation executed by another person was legitimate. That is executed by accepting a witness from the consumer that has a pattern check knowledge level with inputs and anticipated corresponding outputs. That is utilized by customers to validate the authenticity of a prover.
Each Prover and Verifier are deployed onto a Blockchain Community to keep up transparency.
Let’s take an instance of a Sudoku Puzzle to reveal the working of a ZKP. Right here Bob is attempting to unravel a Sudoku Puzzle and Alice says that she is aware of the answer. Bob is now uncertain whether or not Alice truly is aware of the answer. To provide confidence to Bob, Alice must reveal the answer. However this might spoil the enjoyable for Bob! Is there every other option to give Bob confidence that Alice is aware of the answer with out truly revealing it? That’s precisely what a ZKP allows.

Alice can deploy a ZKP(Prover-Verifier) that takes a bit of the puzzle as enter and provides an answer to that part. That method Bob can ship a solved part alongside the anticipated consequence as ‘Witness’ to the ZKP’s Verifier. The Verifier can confirm if Alice’s prover additionally provides the identical resolution as Bob’s anticipated resolution. This might give Bob confidence that Alice truly is aware of the answer. He can then work together immediately with the prover for hints on particular sections of the puzzle.
So how precisely can ZKPs allow privacy-preserving machine studying?
There are two distinct situations the place ZKPs can allow privacy-preserving machine studying:
1. Analytics on Non-public Knowledge.
2. Knowledge and ML Algorithm Marketplaces.
Right here knowledge is non-public however the mannequin must be public to provide confidence within the nature of insights extracted and for it to achieve a bigger viewers.
We are going to take the instance of a credit score scoring software. Right here one may want non-public particulars of a consumer like age, gender, wage, previous debt compensation data, month-to-month bills, and many others. These are then used to compute a credit score rating for the consumer. Immediately there isn’t any option to know for positive if corporations that compute credit score scores respect consumer privateness. They will very nicely use this knowledge for different purposes or promote it to different events with out consumer consent. Placing the entire software on a public blockchain similar to Ethereum allows transparency and protects consumer consent.
There may be one main downside with placing the entire credit score scoring software on Ethereum. The ML mannequin computing credit score rating may be a proprietary know-how of an organization. Corporations haven’t any incentive to host on a public blockchain like Ethereum. That is the place ZKPs come into the image. ZKPs encrypt the core ML algorithm logic right into a Prover. One can consider a Prover as an entity that executes computations in a black field with out revealing the contents of the field to anybody. zk-SNARK and zk-STARKs are the favored encryption strategies to assemble such black-boxes(Provers). You possibly can learn extra about these right here.
We’ll proceed with the credit score scoring instance to grasp how one thing like this may be carried out. Let’s assume Alice runs an organization that computes credit score rating from a consumer’s non-public knowledge. The app is deployed throughout the ZKP framework to make sure consumer’s knowledge privateness. Any consumer similar to Bob can validate the correctness of this ZKP app by passing a witness comprising of check values(age, revenue, expense) together with the anticipated outcome(credit score rating vary) into the Verifier. The Verifier makes use of these values to validate if the output from Prover matches the anticipated witness output.

As soon as the consumer is assured within the correctness of credit score rating computation, he can immediately work together with the Prover that retains sure inputs non-public(Age, Revenue) and others public(Bills). The prover runs a computation and returns the credit score rating as output. This manner we let Alice carry out computations(Analytics) on Bob’s knowledge with out compromising privateness.

Knowledge Marketplaces
ML fashions get higher with knowledge. This creates a robust incentive for corporations to promote and buy knowledge from each other. Immediately there isn’t any option to validate the standard of a dataset with out truly sharing it. That is the place ZKPs come to the rescue once more.
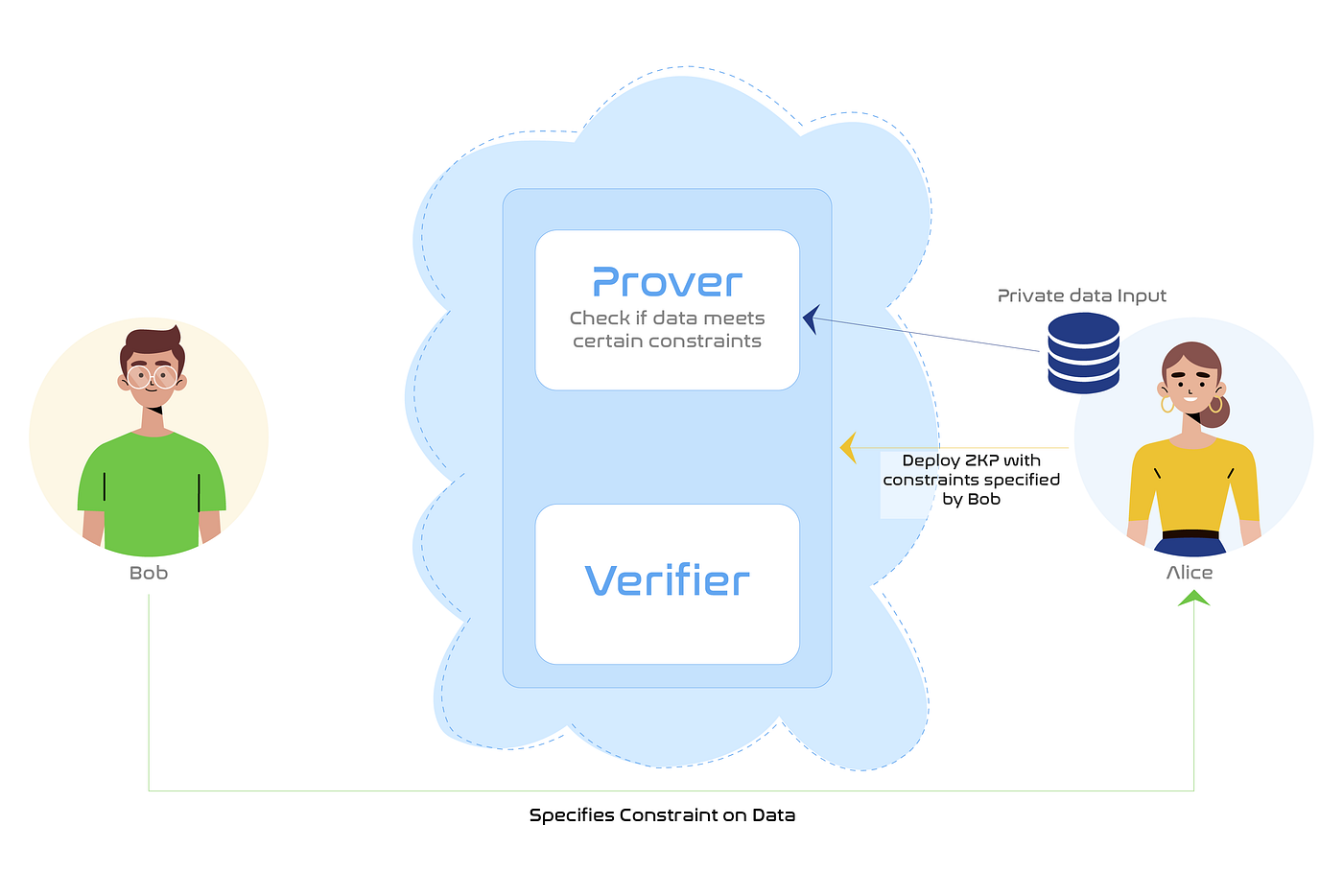
ZKPs can be utilized to assemble a Prover that makes use of sure computations to see if the information meets sure constraints or properties as a sanity examine. The Prover would maintain the information non-public and the actual fact it’s on a public blockchain would guarantee there isn’t any malpractice within the verification course of. This ensures that the purchaser has confidence in knowledge high quality earlier than shopping for the dataset.
If Alice was to promote a personal dataset to Bob, she should make sure that the information meets sure constraints as specified by Bob. A ZKP app is constructed as per Bob’s constraints and deployed onto a public blockchain. Alice can then ship her non-public dataset as enter to the Prover and present that her knowledge meets all crucial constraints.
ML Algorithm Marketplaces
Generally the issue at hand will be to promote the ML Algorithm and the related pre-trained mannequin. Right here too we face the issue of getting the validation from the vendor earlier than promoting it to them. ZKPs can be utilized right here in a fashion similar to the Knowledge Marketplaces downside mentioned above.
We will deploy a pre-trained mannequin right into a Prover through ZKPs. The purchaser can then ship a check dataset to confirm if the mannequin performs satisfactorily on the check set. This ensures that the purchaser has confidence within the ML Algorithm earlier than buying it.
The under illustration exhibits how Alice trains and deploys an ML mannequin into the ZKP framework. This permits bob to check out the efficiency of the mannequin on a customized check dataset earlier than truly buying the ML algorithm from Alice.


