The variety of vulnerabilities disclosed within the first half of the 12 months topped 11,800, forcing corporations to find out the affect of a median of 90 safety points per weekday.
The numbers are from cybersecurity agency Flashpoint’s “The State of Vulnerability Intelligence — 2022 Midyear Version” report, which notes that the huge variety of vulnerabilities reported within the first half of the 12 months highlights the issues dealing with corporations as they attempt to triage software program safety points and decide which software program updates to prioritize.
With out higher steerage, organizations trying to type by way of the safety points battle to separate these which can be extremely crucial from minor vulnerabilities and people that will not have an effect on their atmosphere in any respect, says Brian Martin, vice chairman of vulnerability intelligence at Flashpoint.
“There are some points that can don’t have any bearing on any actual group on the planet — it could be a vulnerability in some Chinese language weblog that has seven installs worldwide,” Martin says. “However, we do have vulnerabilities in Microsoft merchandise, Google merchandise, Apple merchandise. Stuff that’s simply as high-profile and regarding as any situation from a Patch Tuesday.”
Clouding the difficulty is the main focus placed on zero-day vulnerabilities, these labeled as “found within the wild” by researchers earlier than a patch is on the market. These are troublesome to gather info on. Google’s Mission Zero documented 20 such vulnerabilities exploited within the wild within the first half of 2022, whereas Flashpoint discovered not less than 17 extra points.
But the commonest assaults often use recognized vulnerabilities.
“Found-in-the-wild vulnerabilities are sometimes utilized in high-profile breaches or are attributed to Superior Persistent Menace (APT) assaults,” the report states. “On account of their nature, organizations typically lack defensive choices for them. Nonetheless, enterprise leaders have to remember that discovered-in-the-wild vulnerabilities signify a tiny fraction of compromises occurring around the globe.”
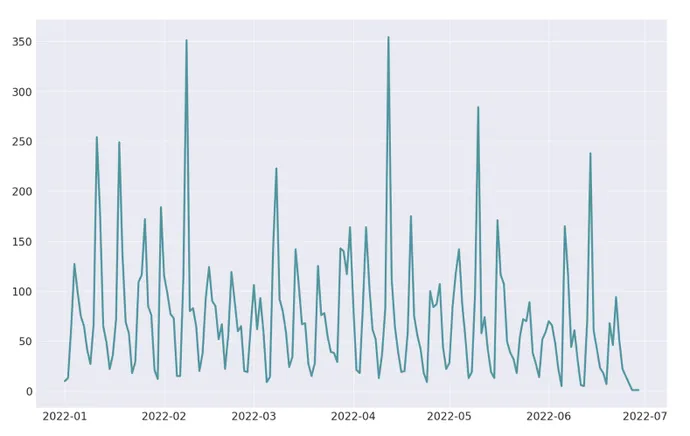
Organizations additionally needed to cope with a rising variety of days with tons of of reported vulnerabilities due to software program distributors’ commonly scheduled updates. In February, for instance, Flashpoint documented 351 points because of releases from Microsoft’s Patch Tuesday and disclosures from different software program distributors falling on the identical day. In April, an analogous convergence of software-vulnerability disclosures noticed the best variety of vulnerabilities, 356, launched in a single day.
“Organizations must be conscious that the vulnerability disclosure panorama is extremely unstable, with ‘customary’ days probably introducing volumes historically seen solely on Patch Tuesdays and different related occasions,” the Flashpoint report states.
Snowballing Ranges of Vulnerability Disclosures
The report additionally reveals that the variety of vulnerabilities disclosed to distributors continues to stay at excessive ranges.
The Nationwide Vulnerability Database (NVD) additionally documented greater than 11,000 flaws assigned Widespread Vulnerability and Exposures (CVE) identifiers within the first six months of the 12 months. Nonetheless, a fraction of these are usually not true reported vulnerabilities however distributors reserving CVE identifiers for future, or yet-to-be disclosed, vulnerabilities. Flashpoint estimates that its database has particulars on 27% extra vulnerabilities than documented within the NVD.
Whereas varied distributions of Linux topped the chart of weak purposes — comparable to SUSE, openSUSE Leap, and Ubuntu — open supply–targeted corporations accounted for under 4 of the ten distributors with the best vulnerability counts within the first half of 2022. But excessive counts are usually not essentially an indication of insecurity however are sometimes an indication that the software program firm has a course of in place to detect and remediate points.
“There are numerous underlying causes as to why sure merchandise and distributors are inclined to have excessive vulnerability counts, comparable to general market share, product-specific market share, routine — or lack of — schedule of disclosures, consideration from vulnerability researchers, and vendor response/patch time, amongst others,” the Flashpoint report states. “Due to this fact, organizations shouldn’t be instantly involved about well-known distributors having ‘extra’ vulnerabilities, because it might be an indication that they’re actively disclosing and patching points.”


