Software program vulnerabilities are a significant menace to organizations right now. The price of these threats is critical, each financially and by way of status.
Vulnerability administration and patching can simply get out of hand when the variety of vulnerabilities in your group is within the a whole lot of 1000’s of vulnerabilities and tracked in inefficient methods, comparable to utilizing Excel spreadsheets or a number of experiences, particularly when many groups are concerned within the group.
Even when a course of for patching is in place, organizations nonetheless battle to successfully patch vulnerabilities of their property. That is typically as a result of groups have a look at the severity of vulnerabilities and have a tendency to use patches to vulnerabilities within the following severity order: vital > excessive > medium > low > data. The next sections clarify why this method is flawed and the way it may be improved.
Why is Patching Troublesome?
Whereas it’s well-known that vulnerability patching is extraordinarily vital, it’s also difficult to patch vulnerabilities successfully. Vulnerabilities may be reported from sources comparable to pentest experiences and varied scanning instruments. Scans may be carried out in your internet functions, APIs, supply code, infrastructure, dependencies, containers, and so on.
The full variety of experiences that must be sifted via to prioritize patches can enhance drastically even in a brief time period, and when a number of groups are concerned, this may additional enhance the complexity and time required to coordinate and prioritize patches.
To make issues worse, new exploits carry on surfacing nearly every day, and conserving monitor of recent exploits and obtainable patches can turn into a mammoth activity that may shortly get out of hand if not addressed correctly. Except a company has a really mature safety program in place, it’s difficult to handle patching successfully.
Taking the Threat-Primarily based Strategy to Patching Vulnerabilities
Simplifying patching requires you to simplify prioritizing first. “Threat-based method” implies that you will weigh the potential impression of a vulnerability in opposition to the chance of its exploitation. This lets you decide whether or not or not it is price taking motion.
To simplify prioritizing, you must think about the next issues:
- The publicity of the asset,
- The enterprise sensitivity of the asset,
- The severity of the vulnerability reported in opposition to the asset,
- The provision of an exploit for the vulnerability reported,
- The complexity of the exploit, whether it is obtainable,
- The taxonomy of the vulnerability reported.
* Asset may very well be something inside your group, like an internet utility, cell utility, code repository, router, server, database, and so on.
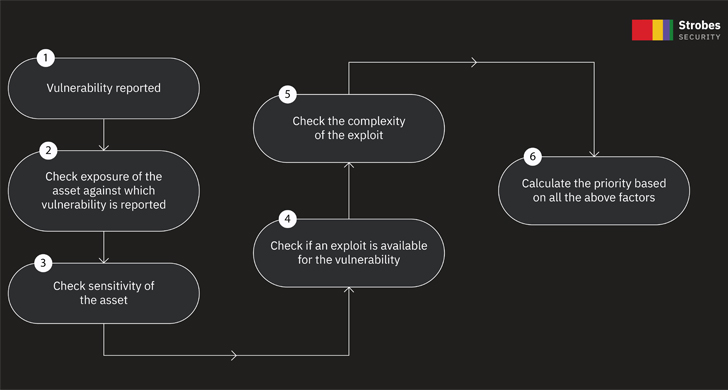 |
| Simplifying Prioritization |
This method helps in drastically lowering the time spent to prioritize vulnerabilities. Let’s focus on every level intimately:
Publicity: In case your asset is public-facing the Web, or non-public, i.e., behind a firewall inside the community with managed entry. Public property often carry a better threat, however that doesn’t at all times imply they need to be prioritized. The reason being that not each public asset is delicate. Some public property might merely be static pages that don’t comprise person information, whereas different public property may very well be dealing with funds and PII data. So even when an asset is public, you need to think about its sensitivity.
Asset sensitivity: Categorize the enterprise sensitivity of all of your property based mostly on how vital that asset is to your corporation. An asset that comprises delicate details about customers or processes funds could also be categorized as a vital enterprise sensitivity asset. An asset that gives just some static content material may be categorised as an asset with low enterprise sensitivity.
Severity of the reported vulnerability: This one is self-explanatory; you must prioritize vulnerabilities so as of vital > excessive > medium > low > data severity.
Exploit availability: Vulnerabilities for which public exploits are already obtainable ought to be prioritized over vulnerabilities for which no exploits can be found.
Exploit complexity: If an exploit may be very simple to take advantage of and requires little to no person interplay, then vulnerabilities for one of these exploit ought to be prioritized over vulnerabilities with very advanced exploits that usually require excessive privileges and person interplay.
Taxonomy: The classification of the vulnerability reported additionally must be considered and ought to be mapped with trade requirements like OWASP or CWE. An instance can be {that a} distant code execution impacting a server ought to be prioritized increased than a client-side vulnerability, say a Mirrored Cross Website Scripting.
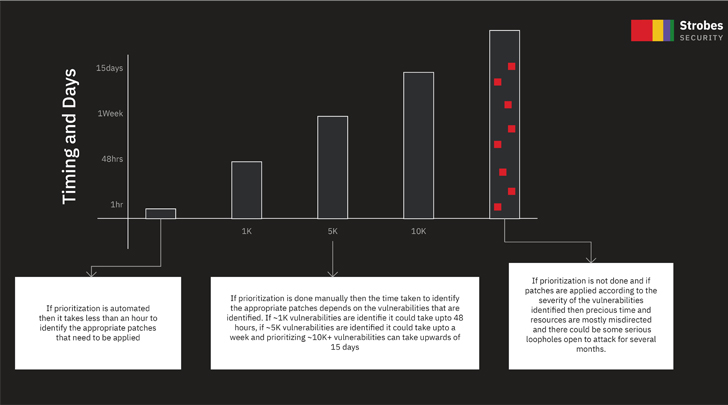 |
| Time spent to prioritize vulnerabilities |
An instance of a excessive prioritized vulnerability can be if the asset which is affected is publicly uncovered, has a vital enterprise sensitivity, the vulnerability severity is vital, an exploit is offered, and doesn’t require person interplay or authentication/privileges.
As soon as all vulnerabilities are prioritized, addressing essentially the most vital vulnerabilities will dramatically cut back the danger to your group.
So what points ought to a vulnerability administration report measure to guarantee your utility safety satisfactorily? – Try the Whitepaper.
Learn how to get the details about patches?
You may get details about patches from varied advisories like NVD. In these experiences, yow will discover a number of references on the way to patch the vulnerabilities. Additionally, the web sites of the merchandise you utilize often present this data. Whereas it’s potential to manually undergo all of the sources and get the details about the patches, if there are numerous safety vulnerabilities in your group, getting all the knowledge from a number of sources may be tedious.
The Answer:
Strobes can considerably assist organizations of all sizes dramatically cut back the time it takes to prioritize vulnerabilities and supply patching data inside the platform. Prioritization can be simple as a result of Strobes robotically prioritizes vulnerabilities for you based mostly on the metrics described within the Threat-Primarily based Strategy to Patching Vulnerabilities part.
Strobes Safety is main the best way to disrupt the vulnerability administration area with its flagship merchandise VM365 and PTaaS. In case you’re not but a Strobes Safety’s person, what are you ready for? Join free right here, or Schedule a demo.


