Cybersecurity researchers have reiterated similarities between the most recent iteration of the LockBit ransomware and BlackMatter, a rebranded variant of the DarkSide ransomware pressure that closed store in November 2021.
The brand new model of LockBit, referred to as LockBit 3.0 aka LockBit Black, was launched in June 2022, launching a model new leak website and what is the very first ransomware bug bounty program, alongside Zcash as a cryptocurrency fee choice.
Its encryption course of includes appending the extension “HLJkNskOq” or “19MqZqZ0s” to every file and altering the icons of the locked recordsdata to that of the .ico file that is dropped by the LockBit pattern to kick-start the an infection.
“The ransomware then drops its ransom be aware, which references ‘Ilon Musk’ and the European Union’s Basic Information Safety Regulation (GDPR),” Pattern Micro researchers mentioned in a Monday report. “Lastly, it adjustments the wallpaper of the sufferer’s machine to tell them of the ransomware assault.”
LockBit’s in depth similarities to BlackMatter come from overlaps within the privilege escalation and harvesting routines used to determine APIs required to terminate processes and different capabilities in addition to using anti-debugging and threading strategies designed to thwart evaluation.
Additionally of be aware is its use of a “-pass” argument to decrypt its major routine, a habits seen in one other defunct ransomware household named Egregor, successfully making the binary more durable to reverse if the parameter shouldn’t be out there.
As well as, LockBit 3.0 is designed to examine the sufferer machine’s show language to keep away from compromising programs related to the Commonwealth of Impartial States (CIS) states.
“One notable habits for this third LockBit model is its file deletion approach: As a substitute of utilizing cmd.exe to execute a batch file or command that can carry out the deletion, it drops and executes a .tmp file decrypted from the binary,” the researchers mentioned.
This .tmp file then overwrites the contents of the ransomware binary after which renames the binary a number of occasions, with the brand new file names primarily based on the size of the unique file title, together with the extension, in an try to forestall restoration by forensic instruments and canopy its tracks.
The findings come as LockBit infections have emerged because the most lively ransomware-as-a-service (RaaS) teams in 2022, the newest allegedly being the Italian Inside Income Service (L’Agenzia delle Entrate).
Based on Palo Alto Networks 2022 Unit 42 Incident Response Report printed as we speak primarily based on 600 circumstances dealt with between Might 2021 and April 2022, the ransomware household accounted for 14% of the intrusions, second solely to Conti at 22%.
The event additionally highlights the continued success of the RaaS enterprise mannequin, decreasing the barrier to entry for extortionists and increasing the attain of ransomware.
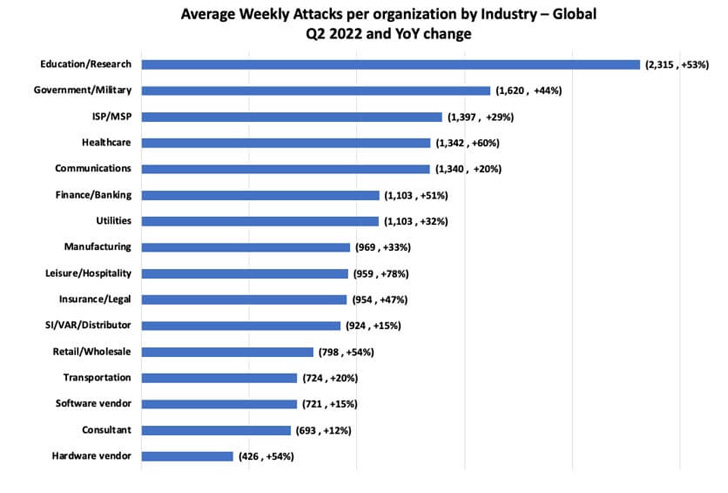
Examine Level’s evaluation of cyberattack traits for Q2 2022 reveals that the weekly common of impacted organizations by ransomware reached one out of 40, a 59% improve YoY from one out of 64 organizations in Q2 2021.
“Latin America has seen the most important improve in assaults, recognizing one out of 23 organizations impacted weekly, a 43% improve YoY, in comparison with one out of 33 in Q2 2021, adopted by Asia area that has seen a 33% improve YoY, reaching one out of 17 organizations impacted weekly,” the Israeli cybersecurity agency mentioned.