Tried ransomware assaults declined within the first quarter of 2022, as firms continued to be much less more likely to pay requested ransoms and the warfare between Russia and Ukraine disrupted the Jap European teams liable for a big share of assaults, endpoint detection-and-response agency Trellix states in a brand new report.
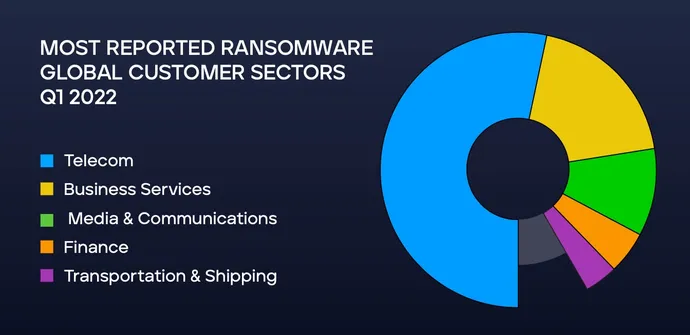
Corporations continued to come across the 2 most typical ransomware households — LockBit and Conti — greater than a 3rd of the time, however each ransomware assaults are seen far much less typically, with detections for LockBit dropping by 44% and Conti by 37%, in keeping with Trellix’s “Summer time 2022 Menace Report.” Globally, ransomware focused the telecom sector in additional than half of assaults, however enterprise providers dominated the concentrating on of US organizations, accounting for 64% of detections.
Whereas cybercriminals typically keep away from politics, the decline doubtless comes because of Russia’s invasion of Ukraine, which has led to extra geopolitical-related assaults however fewer ransomware campaigns, says Christiaan Beek, lead scientist at Trellix.
“The assaults are shifting,” he says. “Whereas we noticed some wipers and another malware, which continued in April and Could, they continue to be pretty low exercise, however we’re seeing extra exercise from hacktivism and [patriot] teams.”
The report from Trellix’s Menace Labs is the primary evaluation from the corporate to mix information and telemetry from two acquisitions — McAfee Enterprise and FireEye’s product enterprise — purchased by Symphony Know-how Group in 2021. In January, STG renamed the mixed companies Trellix.
The corporate additionally contains references to information from a 3rd occasion — incident response agency Coveware — that reveals solely 46% of firms paid a ransom within the first quarter of 2022, down from 85% for a similar quarter three years in the past. The common sufferer’s cost to ransomware teams additionally declined to $74,000, down greater than a 3rd from the fourth quarter of 2021, Coveware said in a Could weblog put up.
“That is what progress appears like towards ransomware. It’s sluggish,” the corporate said.
More durable to Compromise Programs
Nation-state exercise continues to be a serious menace, in keeping with Trellix’s report. Following Russia’s invasion of Ukraine — two international locations which are regarded as residence to a number of ransomware teams — assaults have centered on a purpose of information exfiltration whereas utilizing cybercrime as a strategy to fund the hassle.
In February, for instance, the Conti group publicly posted a press release supporting the Russian authorities. The next month, a Ukrainian researcher leaked years of Conti’s inside chats, displaying that the group had dozens of coders, operated like a enterprise, and maintained separate units of instruments to cover the precise measurement of their operations.
“[W]e ought to think about we may be witnessing the formation of a hybrid group, one that may assault targets chosen by the federal government, however sustaining the believable deniability of a criminal offense group after monetary achieve,” Trellix’s report states. “The ransomware might need a twin goal, on the one hand being disruptive in nature and then again serving as a distraction for an information exfiltration operation.”
Different main tendencies embody the continued adoption of living-off-the-land (LotL) methods. Whereas a red-team instrument, Cobalt Strike, continues to be the most well-liked assault instrument by far — utilized in a 3rd (32%) of campaigns — attackers proceed to make use of instruments resident on the focused methods, together with Home windows Shell, PowerShell, and the Home windows Administration Interface (WMI), Trellix’s report states.
Nonetheless, attackers do need to work tougher to compromise methods, with enhancing defenses requiring longer assault chains, says Beek. Prior to now, a sufferer would possibly click on on a hyperlink in an electronic mail or open an untrusted attachment and have a computer virus put in.
“Now, you see an electronic mail with an attachment nonetheless, nevertheless it has somewhat script in there that could be a URL, for instance, and it goes to 1 web site, downloads somewhat little bit of code,” Beek says. “There are extra levels which are taking place earlier than one thing is certainly being placed on the system.”
Whereas telecommunications firms and enterprise providers are at present the most well-liked targets of assaults, among the many most worrisome tendencies is the vulnerability of the healthcare trade and the continued ransomware assaults on the organizations that present medical care, Beek says.
He warns that the development will doubtless proceed, given the anemic funding for cybersecurity in healthcare.
“This isn’t simply the a ransomware perspective — it is also in regards to the degree of vulnerability,” he says. “For me, that could be a concern. You need to go to a hospital to get handled, and you do not need delays due to ransomware.”


