Industrial engineers and operators are the goal of a brand new marketing campaign that leverages password cracking software program to grab management of Programmable Logic Controllers (PLCs) and co-opt the machines to a botnet.
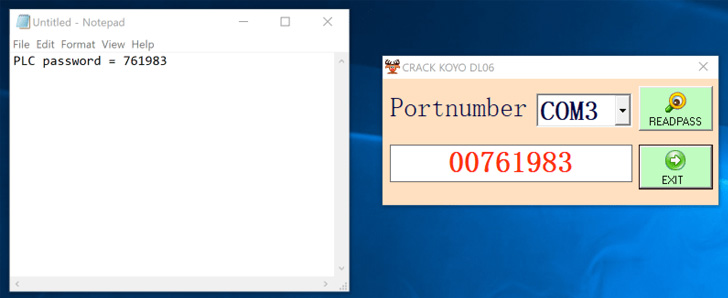
The software program “exploited a vulnerability within the firmware which allowed it to retrieve the password on command,” Dragos safety researcher Sam Hanson mentioned. “Additional, the software program was a malware dropper, infecting the machine with the Sality malware and turning the host right into a peer in Sality’s peer-to-peer botnet.”
The commercial cybersecurity agency mentioned the password retrieval exploit embedded within the malware dropper is designed to get well the credential related to Automation Direct DirectLOGIC 06 PLC.
The exploit, tracked as CVE-2022-2003 (CVSS rating: 7.7), has been described as a case of cleartext transmission of delicate information that would result in info disclosure and unauthorized adjustments. The difficulty was addressed in firmware Model 2.72 launched final month.
The infections culminate within the deployment of the Sality malware for finishing up duties comparable to cryptocurrency mining and password cracking in a distributed vogue, whereas additionally taking steps to stay undetected by terminating safety software program working within the compromised workstations.
What’s extra, the artifact unearthed by Dragos capabilities drops a crypto-clipper payload that steals cryptocurrency throughout a transaction by substituting the unique pockets deal with saved within the clipboard with the attacker’s pockets deal with.
Automation Direct will not be the one vendor impacted because the instrument declare to embody a number of PLCs, HMIs, human-machine interface (HMI), and mission information spanning Omron, Siemens, ABB Codesys, Delta Automation, Fuji Electrical, Mitsubishi Electrical, Schneider Electrical’s Professional-face, Vigor PLC, Weintek, Rockwell Automation’s Allen-Bradley, Panasonic, Fatek, IDEC Company, and LG.
That is removed from the primary time trojanized software program has singled out operational know-how (OT) networks. In October 2021, Mandiant disclosed how professional transportable executable binaries are being compromised by quite a lot of malware comparable to Sality, Virut, and Ramnit, amongst others.