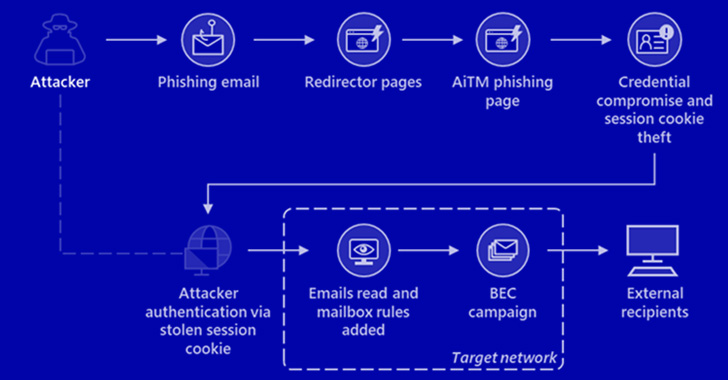
Microsoft on Tuesday disclosed {that a} large-scale phishing marketing campaign focused over 10,000 organizations since September 2021 by hijacking Workplace 365’s authentication course of even on accounts secured with multi-factor authentication (MFA).
“The attackers then used the stolen credentials and session cookies to entry affected customers’ mailboxes and carry out follow-on enterprise e-mail compromise (BEC) campaigns in opposition to different targets,” the corporate’s cybersecurity groups reported.
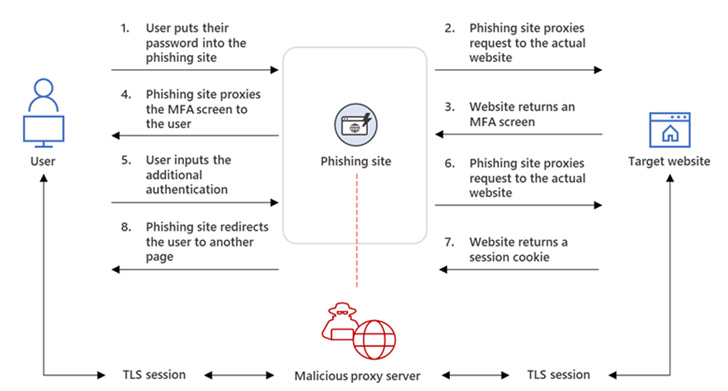
The intrusions entailed organising adversary-in-the-middle (AitM) phishing websites, whereby the adversary deploys a proxy server between a possible sufferer and the focused web site in order that recipients of a phishing e-mail are redirected to lookalike touchdown pages designed to seize credentials and MFA data.
“The phishing web page has two totally different Transport Layer Safety (TLS) classes — one with the goal and one other with the precise web site the goal needs to entry,” the corporate defined.
“These classes imply that the phishing web page virtually features as an AitM agent, intercepting the entire authentication course of and extracting precious information from the HTTP requests comparable to passwords and, extra importantly, session cookies.”
Armed with this data, the attackers injected the cookies into their very own browsers to bypass the authentication course of, even in situations the place the sufferer had enabled MFA protections.
The phishing marketing campaign noticed by Microsoft was orchestrated to single out Workplace 365 customers by spoofing the Workplace on-line authentication web page, with the actors utilizing the Evilginx2 phishing equipment for finishing up the AitM assaults.
This concerned sending e-mail messages containing voice message-themed lures that had been marked with excessive significance, tricking the recipients into opening malware-laced HTML attachments that redirected to the credential-stealing touchdown pages.
To finish the ruse, the customers had been finally redirected to the reliable workplace[.]com web site post-authentication, however not earlier than the attackers leveraged the aforementioned AitM method to siphon the session cookies and acquire management over the compromised account.
The assaults did not finish there, for the risk actors abused their mailbox entry to carry out fee fraud by utilizing a method known as e-mail thread hijacking to dupe events on the opposite finish of the dialog to illicitly wire funds to accounts below their management.
To additional masks their communications with the fraud goal, the risk actors additionally created mailbox guidelines that routinely moved each incoming e-mail containing the related area identify to the “Archive” folder and marked it as “learn.”
“It took as little time as 5 minutes after credential and session theft for an attacker to launch their follow-on fee fraud,” Microsoft famous.
The attackers are mentioned to have employed Outlook Internet Entry (OWA) on a Chrome browser to conduct the fraudulent actions, whereas additionally deleting from the account’s Inbox folder the unique phishing e-mail in addition to the follow-on communications with the goal from each the Archive and Despatched Gadgets folders to erase traces.
“This AiTM phishing marketing campaign is one other instance of how threats proceed to evolve in response to the safety measures and insurance policies organizations put in place to defend themselves in opposition to potential assaults,” the researchers mentioned.
“Whereas AiTM phishing makes an attempt to bypass MFA, it is essential to underscore that MFA implementation stays an important pillar in identification safety. MFA continues to be very efficient at stopping all kinds of threats; its effectiveness is why AiTM phishing emerged within the first place.”
The findings come as a bunch of researchers from Stony Brook College and Palo Alto Networks demonstrated late final yr a brand new fingerprinting method that makes it potential to determine AitM phishing kits within the wild utilizing a instrument known as PHOCA.